A guide to cyber security for small and medium businesses

In this cyber security guide, we take you through everything you need to know about cyber attacks, data breaches and cyber crime, identifying why your business might be at risk, what those risks are and what steps you should take to protect your business from information security breaches and cyber crime.
On this page:
- Protecting your business from cyber attacks
- Why your business should care about cyber security?
- Why your business is a target for cyber crime?
- Types of Cyber Security Threats
- How to protect your business from a Cyber Security Attack?
- Improving your Cyber Security even further
- What to do if your business suffers a cyber security attack?
- Top ten essential cyber security tips
- Other ways to protect your business from cyber crime
Protecting your business from cyber attacks
In recent times, cyber security has increasingly become a regular headline featured in the news. This is unsurprising, considering the increasingly sophisticated cyber attack techniques used in cyber crime, and the failure of businesses to keep their information security up to date.
In fact, global cyber attacks have increased by more than 50% in the last three years and the cost to businesses is enormous.
According to a report by Detica for the Cabinet Office, the cost of such attacks is estimated to be £21 billion annually to the UK business community.
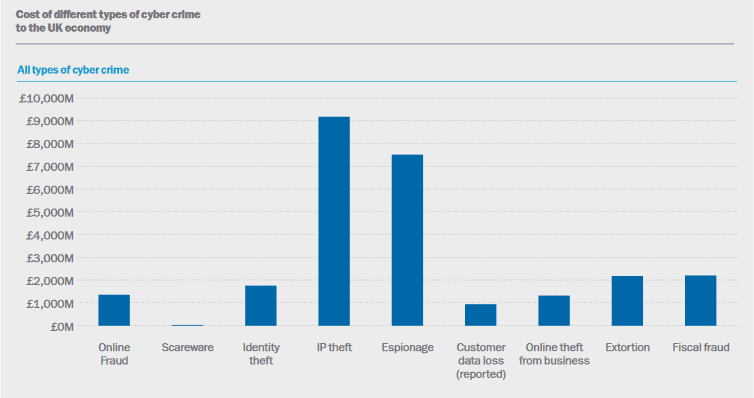
Impact to small and medium businesses
When we read the news what we tend to hear about are the big cyber crimes – Talk Talk, Tesco Bank, Three Mobile and Travelex are recent examples – affecting millions or sometimes, even billions of people. However, what you don’t hear about are cyber attacks on small-to-medium businesses.
But they do occur – a lot.
Furthermore, it’s easy to consider start-ups and small-to-medium businesses as unlikely targets of a cyber attack for a variety of reasons. However, 60% of all cyber attacks or breaches are now targeted at small businesses and whilst most attempts fail, a small business in the UK is successfully hacked every 19 seconds.
Moreover, these attacks are costly. The Cyber Security Breaches Survey 2019, measuring how UK organisations approach cyber security, found that the average financial costs for small and medium sized businesses that lost data or assets from breaches was £12,920, with the most severe breaches reaching as high as £310,800, up from £115,000 in 2014.
Why your business should care about cyber security?
For most small and medium businesses the subject of cyber security can seem overwhelmingly complex, but a fundemental understanding of cyber security is nowadays considered crucial for running a business.
However, a significant proportion of small and medium businesses still assume their operations are either too small or their data is not theft-worthy and as as result give insuffcient consideration to the impact a cyber security or data breach could have on their business.
The failure of such businesses to protect their organisations from such threats exposes them to three main risks – reputational, financial, and legal. Here, for the purposes of this cyber security guide, we look at a each of these risks in summary.
Reputational
The reputational damage your business could suffer as the result of a data breach caused by a lack of a cyber security policy may be catastrophic – 60% of SMEs closing permanently following a data breach or an incidence of data theft within 6 months.
In the event your data security is breached, whilst you may be able to salvage some relationships with your customers and even manage to retain some, the likelihood is that most customers would take their business elsewhere.
After all, would you trust a business whose lack of cyber security compromised your financial situation or led to your identity being stolen?
In the UK, 44% of consumers claim they will stop spending with a business for several months in the immediate aftermath of a security breach, and 41% of consumers claim they will never return to a business post-breach
Financial
Whilst the quantitative costs are easy for organisations to identify, measure and capture, there are many other aspects which many businesses overlook when calculating the costs and impact of their breaches.
Consequently, in reality the actual financial cost of cyber crime is often higher than the estimate of £12,920 for lost data or assests from breaches for SMEs (Cyber Security Breaches Survey 2019).
Indirect financial costs can include loss of customers (both current and potential), any costs related to cyber security remediation activities, and any outage time incurred during investigation and can generally be categorised into three areas:
- Indirect costs: e.g. downtime and loss of productivity.
- Ongoing costs: e.g. costs of putting together new procedures, measures and controls in place as a response to the breach.
- Intangible costs: e.g. reputational damage.
Legal, compliance & regulatory
In recent years, not only have we seen a raft of legislation introduced, but also an increased focus on industry standards which promote information security best practicies – all designed to help businesses address the increase in cyber crime and protect both businesses and consumers from cyber attacks.
Moreover, the legislations seek to protect user data and enforce information security standards on businesses, which in the event of compliance failures can result in fines or termination of key services, potentially impacting your business revenue and severly restricting your ability to conduct business.
As part of this cyber security guide, we have summarised in the table below the key regulations, standards or frameworks which are currently prevalent within the UK information security sphere :
Regulation, Standard or Framework & Body |
Type |
Applicable to |
Body |
Penalty for non-compliance |
| GDPR | Legal | UK Organisations which collect, store or otherwise process the personal data of individuals residing in the EU | ICO | Up to €20m or 4% of annual global turnover – whichever is greater. |
| NIS Directive | Legal | Operators of essential services (OES) and Digital service providers (DSP) * | Relevant Authority | Non-compliant UK organisations may be fined up to £17m. |
| PCI-DSS | Industry | All merchants and service providers that process, transmit or store cardholder data | PCISSC | Withdrawal of card payment facilities – a breach or theft of cardholder data may also breach GDPR. |
| ISO/IEC 27001:2013 | Optional | Any organisation which wishes to demonstrate its commitment to information security best practices | UKAS | Loss of accrediation – a breach or theft of sensitive and personal data may also breach GDPR. |
* OES are providers of the UK’s energy, transport, health, water and digital infrastructure sectors; DSPs are segmented into three groups – online search engines, online marketplaces and Cloud computing services.
The Regulations do not apply to DSPs which employ fewer than 50 people and whose annual turnover and/or balance sheet total is less than €10m (about £8.7m))
GDPR
Replacing the Data Protection Act (1998), the EU GDPR (General Data Protection Regulations) came into force on 25th May 2018. The GDPR is enshrined in law in all 28 EU countries. Since leaving the EU, GDPR has been enshrined into English and Scottish law.
If your business suffers an information security breach and as a consequnece suffers a data loss, GDPR requires you to inform the Information Commissioner’s Office (ICO) and also every single individual whose may have have been affected by the breach. Once you become aware of the breach, you must do all this within 72 hours (if feasible).
Failure to notify either the ICO or the individuals affected could “result €20 million or 4% of your global turnover. The GDPR is applicable to most businesses who hold personal data one their customers, suppliers and employees.
Our Guide to GDPR for Small and Medium Businesses provides a useful overview of GDPR and along with our GDPR FAQ and GDPR Compliance Checklist, will help your business understand and adhere to GDPR .
PCI-DSS
Set up by a consortium of lenders, the Payment Card Industry Data Security Standard (PCI-DSS) intends to protect sensitive cardholder data by helping businesses process card payments securely reduce card fraud.
This is achieved through a series of best practices, frameworks and guidelines which collectively form the PCI-DSS, enforcing controls regarding the storage, transmission and processing of cardholder data that businesses manage.
If your business is not compliant you may be liable for non-compliance fines if you do not work towards compliance with your acquirer. Ultimately, failure to comply may force your acquirer to terminate your relationship, which will prevent you from accepting payments by card.
ISO/IEC 27001
ISO/IEC 27001 is an information security standard, part of the ISO/IEC 27000 family of standards, of which the last version was published in 2013.
Whilst there is no legislation which stipulates that business must adhere to the ISO/IEC 27001 informaiton security standard, you may find that adherence to this standard improves you cyber security credentials by enabling you to document and verify that risks are identified and are managed, whilst demonstrating that you are determined to ensuring your customer’s, staff’s and supplier’s information is secure.
The ISO/IEC 27001 standard specificially aims to bring information security under management control and gives specific requirements. Businesses that meet the requirements may be certified by an accredited certification body following successful completion of an audit.
Our article, “Does your business needs to be ISO/IEC 27001 certified?“, will provide business with guidance if you are considering improving your cyber security credentials.
Why your business is a target for cyber crime?
The Internet is an international, instantaneous, trans-border communications network which offers automated data processing. These characteristics provide the opportunity to commit cyber crime with an increasingly level of anonymity.
Small and medium businesses, particularly those trading on the internet, can be lucrative targets for malicious hackers, who can use the data as an entry point to the bigger organisations in the supply chain.
Commonly there is a misconception that hackers will not be interested in attacking a business with little money or data.
Consequently, many businesses often overlook the value of the information they store, believing it to be of little value to anyone.
- According to the UK Gov’s ‘Cyber Survey 2019’, 31% of small businesses & 60% of med-sized businesses experienced a cyber-attack in 2018.
- The ONS estimate around 4.5 million cyber crimes were committed in England and Wales during 2018.
- Cyber crime now accounts for more than 50% of all crimes in the UK (National Crime Agency).
- The FCA’s Cyber and Technology Resilience survey 2017-18 , identified that nearly 80% of respondents struggle to maintain a view of what Information Assets they hold and of their third parties (tangible or intangible value that is worth protecting, including people, information, infrastructure, finances and reputation).
The value of your business data
Any personably identifiable information on customers like email addresses, phone numbers, or payment card details, is valuable to hackers who can use it to commit fraud or sell it on the dark web.
Top 10 most valuable information to cyber criminals |
|
| 1. Customer information (17%) | 6. R&D information (9%) |
| 2. Financial information (12%) | 7. M&A information (8%) |
| 3. Strategic plans (12%) | 8. Intellectual property (6%) |
| 4. Board member information (11%) | 9. Non-patented IP (5%) |
| 5. Customer passwords (11%) | 10. Supplier information (5%) |
Source: EY – Global Information Security Survey 2018-2019
So, what can cyber criminals do with your data?
- Manipulate your sales database to determine who your most affluent customers are to then sell that information on in the black market. The value of your data is at its highest in the first few days after it is stolen.
- Steal any unencrypted debit or credit card information.
- Use any details they find on an individual or a company which could then be used to change the information held by government or other authorities to take out loans or open credit card accounts.
- Copy the usernames and passwords used on the websites of companies from which you buy online.
- Steal commercially sensitive and valuable data.
- Discover the names of employees, managers, and board members in order to spoof their email details with the intention of committing fraud.
The opportunity for cyber crime
Small and medium businesses are vulnerable predominately because they don’t always fully appreciate the scale of the risk they face.
This vulnerability coupled with the opportunity for growth and efficiency the internet and computer technology provides to S
MEs provides ample opportunities for gaps in security to appear – potentially permeating through the supply chain.
It is these gaps that cyber criminals target and seek to exploit.
- Time: Operating a small and medium business is a time consuming affair. Leaders of such organisations typically spend long hours and restless nights nurturing, growing and managing their business. In such circumstances it’s easy to assign information security as a low priority on your list.
- Lack of expertise: As a multi-faceted topic, cyber and information security requires the correct implementation of technology and policies to be in place. Small and medium businesses typically don’t have the dedicated internal expertise to identify the responsibilities and wade through the guidelines regarding data security.
- Lack of data management: Tracking the volume of data your organisation has generated over any given duration can be difficult. The volume of customer data you manage will be small early on in your company’s growth, but it can quickly become substantial. The improper storage of customer data could lead to financial penalities from the ICO.
- Remote and/or flexible workforce: In a globalised economy, many businesses now rely on freelancers and remote workers – frequently accessing your systems from co-working environments or coffee shops. In such a circumstances, hackers can quite easily hack your data if there is no secure Wi-Fi connection.
- Every organisation is a potential target: Cyber criminals and hackers dedicate their time searching for organisations with information security vulnerabilities. Strengthening your cyber security stance will minimise your exposure. This hacking map shows the number of attacks happening in real-time.
Types of Cyber Security Threats
According to the 2019 Data Breaches survey by the Department for Digital, Culture, Media & Sport, the most common type of cyber attacks reported by SMEs were phishing type attacks.
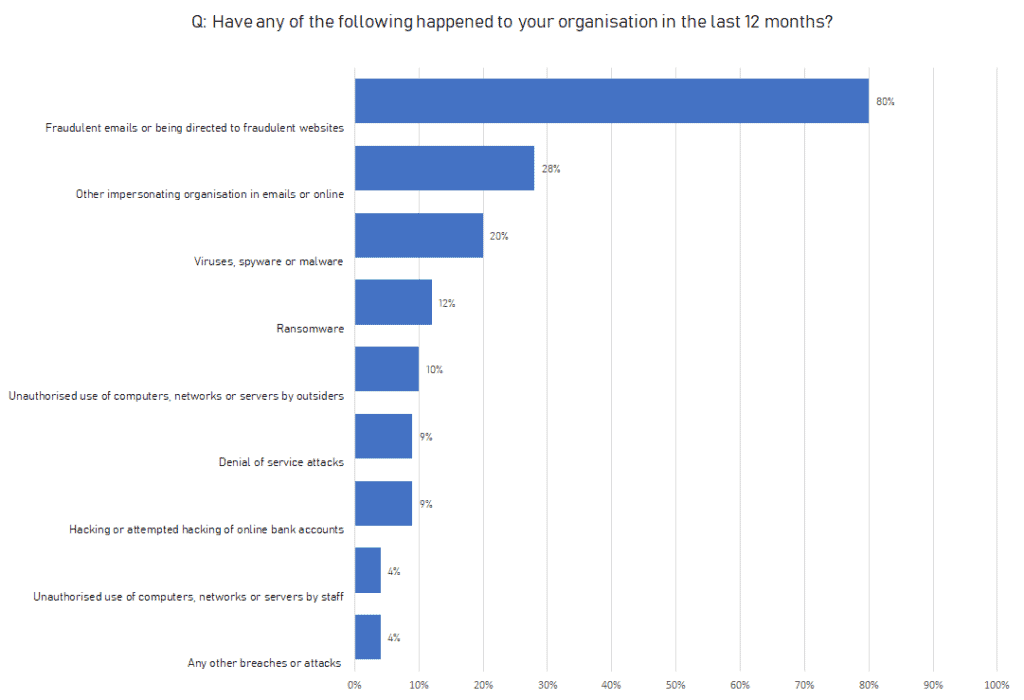
Source data: Cyber Security Breaches Survey 2019
As part of a phishing and social engineering attack, a cyber criminal will try to trick employees into revealing sensitive or confidential information, for example passwords and credit card details, by sending them instant messages or emails seemingly from a trusted sender — for example, their banks.
Unsuspecting employees can then be directed to fake sites that may prompt the employee to unwittingly install malware or steal password and bank account information from clients, customers or employees.
It’s worth noting, whilst data breaches and cyber attacks are typicaly lumped together, they are in fact perpetrated various cyber criminals, that will attempt to attack and access your business systems in a multitutde of ways.
Furthermore, they’re constantly learning and evolving, so staying vigilant to the latest threats is vital to minimising the risks to your business. Here is a summary of some of the major types of cyber threats facing startups and small and medium businesses:
Phishing
A popular mode of attack accounting for 90% of data breaches, phishing attempts to obtain sensitive data such as usernames, passwords and credit card details by sending out emails to multiple recipients, often posing as a trusted party such as social web sites, auction sites, banks, online payment processors or IT administrators.
The email will typically contain a malicious link or malware in the attachment, or will take the recipient to a fake website, owned and operated by cyber criminals, to enter confidential details such as account or password information, enabling cyber criminals to capture and exploit this sensitive data.
- Phishing: A phishing email is a fraudulent attempt to get sensitive data or information from people like their usernames, passwords, financial information or credit card details, by disguising as someone trustworthy.
- Spear phishing: Spear phishing is when an attacker singles out a specific organization or individual in order to gain access to sensitive data.
- Whaling: A whaling attack is in the category of phishing emails and specifically targets high profile individuals and executives with valuable information.
- CEO fraud: CEO fraud is when a hacker sends an email to an employee of a company posing as the CEO and requesting the transfer of funds or access to information.
Malware
Malware, a portmanteau for malicious software, describes any software or code which is designed to intentionally cause harm to a computer, system or network in a number of ways:
- Causing a device to become unaccessible or rendering it unusable
- Encrypting, deleting or stealing data
- Hijacking your devices to attack other organisations
- Stealing credentials to gain access to your systems or services
- Using services that may cost you money (e.g. premium rate phone calls)
A wide variety of types of malware exist, and are typically used in conjunction with phishing as a deployment mechaism to instigate an attack:
| Adware | Unwanted software designed to throw unwelcomed advertisements on your screen. |
| Blastware | Destroys the system it has infected once completing its task, leaving no traces. |
| Cryptojacking | Usually installed via a Trojan, allows your computer to be hijacked to mine cryptocurrency, i.e. Bitcoin. |
| Ghostware | Penetrates a network without detection, steals sensitive data, then cover its tracks before it leaves. |
| Exploits | Takes advantage of vulnerabilities in a system in order to allow the attacker to take control. |
| Keylogger | Records all the user’s keystrokes on the keyboard, sending the infomration to the attacker. |
| Ransomware | Locks you out of your systems and/or encrypts your files, forcing you to pay a ransom. |
| Rootkit | Provides the attacker with administrator privileges on the infected system, whilst remaining undetected. |
| Spyware | Secretly observes the computer user’s activities without permission and reports it to the attacker. |
| Trojan | Misrepresents itself as something useful. Once on your system, allows attackers to gain access. |
| Virus | When inadvertently executed by the user, replicates itself by modifying and infecting other software. |
| Worms | Self-replicating in order to spread to other computers over a network, usually destroying data and files. |
DoS/DDoS
“Denial of service” or “DoS” describes the ultimate goal of a class of cyber attacks designed to render a service inaccessible.
A ‘distributed denial of service’, referred to as “DDoS”, is when the attack orginates from multiple computers (or vectors) instead of just one.
Whilst these attacks have been in the media recently for high visibility targets such as Airbnb, Netflix, Reddit and Twitter, DDoS/DoS attacks can be perpertrated on any type of system, including industrial control systems which support critical processes.
Commonly conducted against websites, a DDoS/DoS attack can render the website to be unavailable to potential customers and users, leaving the business unable to trade for a period of time (anything from a few minutes to even days) depending on the on the duration of the attack.
Due to their website architecture, smaller companies are often at higher risk .
Insider threat
The term “insider threat” refers to the malicious threat the posed by those within the organisation (such as employees, former employees, contractors or business associates) which willfully steal, damage or expose internal data or systems.
Insider threats can be broadly categorised as follows:
- Malicious insiders: Individuals who take advantage of their access to inflict harm on an organisation.
- Negligent insiders: Individuals who make errors and disregard policies.
- Infiltrators: Individuals who obtain and/or misuse legitimate access credentials without authorisation. IBM’s 2015 Cyber Security Intelligence Index report identifies human error as a dominating factor in breaches.
Whilst only 23.5% of cyber attacks were carried out inadvertently by insiders (compared to 31.5% by malicious insiders), 95% of all breaches were directly attributed to human error.
Most serious insider threats in cyber security usually occur either through personal negligence, poor or inadequate security practices, or both, with a breach being caused by staff inadvertently sharing confidential information to the wrong audience, misplacing their company mobile device, using poor passwords or sometimes with malicious intent.
Despite the many risks, many small and medium businesses fail to implement the necessary controls, training and communication to prevent these kinds of breaches.
How to protect your business from a Cyber Security Attack?
Global organisations have a strong awareness of cyber security threats and the need to address it. However, this awareness does not always translate to preparedness.
NTT’s global survey reveals that only 28% of the total number of companies had fully-understood policies.
Bearing this in mind, we’ve outlined the steps you need to take to prevent your business being a victim of cyber crime:
Perform an information security risk assessment
A cyber or information security risk assessment will help you understand which information assets you need to protect (such as hardware, systems, laptops, customer data and intellectual property).
This will identify those areas where you are are most susceptible to a cyber attack and typically seeks to answer the following types of questions:
- What is your business’s most important data assets?
- In terms of customer information, what major impact will a data breach have on your business?
- What key relevent threats exist and what are the sources of those threats to your business?
- Which of the identified threats are internal and which are external?
- What will be the impact your organisation if these threats are exploited?
- How likely are these threats to be exploited?
- Which cyber attacks, threats, or incidents will impact your business operations and how?
- What levels of risk is your company comfortable taking?
For efficiency, we suggest spending the time defining a standard for determining the importance of an asset.
Typically, this could include asset value, legal standing and business importance. Once the standard has been determined, you can use it to classify each asset as critical, major or minor. For cost-effectiveness reasons, we recommend limiting your scope to the most business-critical assets.
Our guide to performing an information security risk assessement can help you understand, manage, control and mitigate cyber security risk across your business. Without a cyber or information security risk assessment, your approach to cyber security could waste time, effort and resources.
Similarly, the lack of a risk assessment may lead you to underestimate risks that could cause a significant impact.
Implement technical and non-technical controls
Once you’ve completed your information security risk assessment, you should have an understanding of your most valuable information assets, and any potential threat or vulnerability that is posed to a particular information asset.
You now need to secure it with the relevant controls to minimise or eliminate the probability of a threat or vulnerability.
Controls can be either preventative or detective:
- Preventative controls: Attempt to stop attacks like encryption, antivirus or continuous security monitoring.
- Detective controls: Discover when an attack has occurred like continuous data exposure detection. Controls can be implemented either through technical means (hardware, software, encryption, intrusion detection, automatic updates) or through non-technical means (security policies and physical mechanisms, i.e. locks or keycard access).
Some of the controls that will make a significant improvement to your cyber security:
- Create and maintain a comperehensive information security and data management policy.
- Establish a culture of security awareness to ensure adherence to security policies, processes and procedures.
- Ensure your network equipment (firewall, wi-fi, router, etc) are correctly and securely configured by a certified resource.
- Verify and maintain the latest patches on all end user devices, including those which are employee owned.
- Organise regular staff cyber security awareness training sessions.
- Implement secure remote access solutions such as a virtual private network (VPN) for remote and mobile workers.
- Deploy digital security measures (i.e. encryption and Two-Factor Authentication) to prevent unauthorised access.
- Update, maintain and test your disaster recovery protocols in the event of a cyber attack.
- Create and implement a robust password policy.
- Establish and regularly assess access controls to ensure staff have access only to information relevant to their roles and duties.
Increase security awareness and training
Your information security policy should underpin your communciations and outline the required processes and procedures – what employees should and shouldn’t do, and the potential consequence if the policy is violated.
The preceise issues will vary between organisations, but potential areas may include:
- Guideline for staff on how to handle sensitive information
- Password security controls
- Personal device and remote working policies
- How to identify, report & respond to security issues
- Required supplier and vendor checks to validate they are compliant with any regulatory requirements and adherence to cyber security best practices
Your cyber policy should be is accessible to all members of your staff, regularly updated , and your employees should be provided with appropriate training around the cyber issues annually.
Create a security focussed mobile culture
Sensitive business data which your employees can access both whilst inside and outside your company, can often be overlooked and needs to be protected all the time.
Here’s some guidelines which will keep your data secure when your employees are mobile:
- Encourage the use of complex passwords – see 5 password tips for better SME security
- Establish automatic passwords expiry and renewal
- Restrict access to malicious websites that could pose a risk to the security of your data
- Encrypt all mobile devices, laptops, phones, tablets used for business related activities
Implement vendor monitoring
The amount and level of information that vendorsand suppliers have access to can also present a security risk.
Most SMEs are not aware of the level of access a vendor may have. Confirming the vendor’s security controls needs to be a core part of your vendor and supplier vetting and onboarding process.
Key points to look for include:
- How will the vendor store your data
- Implement and monitor access controls for vendor’s employees
- Regularly conduct a vendor risk assessment for each of your vendors
- Ensure you vendor complies with General Data Protection Regulations
Implement employee monitoring
Current or former staff member, service providers, suppliers or anyone else that could get access to your sensitive data can be classed as an insider threat.
These individuals typically have access to sensitive information, and often have the responsibility to protect such data, leading to severe repurcussions if it transpires that they cannot be trusted.
You can take simple steps to prevent the misuse of data by employees.
Regularly conduct a vulnerability assessment
Finally, regular assessment and testing should be conducted to identify potential security risks to your business sytems and network.
In this scenario, 3rd parties can be hired to do stress test your systems and network to identify any vulnerabilities, providing your the opportunity to remediate before it’s too late.
Note:- You may be tempted to save a little money by going to an electrical retailer and purchasing network security equipment intended for home users. Whilst this may seem cost-effective, you will be better protected if you spending a little more money for equipment specifically intended for commercial use. Firewalls intended for personal are not designed with the capability to handle the levels of traffic a business grade firewall can and will likely result in slower internet speeds hampering your productivity.
Improving your Cyber Security even further
Once you have the essential components in place, you may consider improving your cyber security defence further.
There are many additional add-ons, apps and steps you can implement further secure your company to an advanced level. Here we look at some of the technologies available which will enable you to achieve this:
Mobile device management (MDM)
Whether you employ a Bring your own device (BYOD) policy or are providing your employees with mobile devices for work related purposes, these devices will be accessing company information such as email and potentially sensitive business applications.
Consequently, you will need a mobile device policy which will protect your company data in case the employee has their phone is stolen or manages to lose it. Mobile device management allows you to adminstrate mobile devices by creating, defining and implementing polices on the device to ensure mobile devices are kept secure at all times.
MDM offers functionality such as setting a mandatory requirement for a passcode, using an encryped password vault to store passwords, preventing mobile devices from being modified or jailbroken and allowing all devices to be kept automatically up to date with the latest security patches.
Multi-factor authentication (MFA)
Multi-factor authentication uses multiple credential to verify a user’s identity. MFA creates multiple security layers to increase the confidence in the verification of the user requesting access.
MFA can take several forms, including a code such as a password, pin code or a RSA token or a registered physical credential such as a smart card, fingerprint or facial scanner. MFA uses more than one of these methods for access dramatically increasing protection.
With Multi-factor authentication in place, whilst a cyber criminal may be able steal one credential such as username and password, the cyber criminal still won’t be able to gain access to the target systems as they will still need to verify their identity in a further different manner.
Data loss prevention (DLP)
DLP software products use rules to idenitfy and protect confidential information to prevent inadvertent or malicious sharing of data with an unauthorised recipient .
DLP prevents the leak of sensitive information such as corporate files to external sources sucha as cloud storage, personal email, social media sites, etc.
Organisations typically deploy DLP to protect and secure their data, minise data breaches and ensure regulatory compliance.
What to do if your business suffers a cyber security attack?
Despite effective security measures, you may find yourself powerless to prevent a breach.
As such, having an effective incident response plan is critical, allowing your to take control of the situation as soon as possible, with minimumal impact to your customers and company.
Despite its importance, less than a third of small and medium organisations have a data breach response plan.
An effective response plan would have a nominated a team consisting of IT, Legal, Operational, PR and HR personnel, emergency contact numbers and pre-agreed forms and processes.
Your plan should contain all the checklists, processes, templates and techniques that the response team need and should cover the following components:
- Legal response: As part of your plans, you should outline how you will handle the legal aspects of the breach, for example defending your company against any claims of negligence and informing and keeping the Information Commissioners Office (ICO) updated on the breach.
- Response to media queries: Following a breach, your company could find itself the focus of increased media scrutiny. Be prepared to manage external communications about what occured and how you are managing it. To do this effectively, you will most likely need professional expertise.
- Investigating what happened: An IT forensics expert will be able to investigate and identify the cause of the breach. They will have recommendations on how to rectify the problem quickly and preventative measures that need to be put in place to ensure it does not happen again.
- Keeping customers informed: Dependent on your customer base and the scale and type of the breach, you may have a significant number of unpleasant phone calls to make. Be prepared on how you will handle this communication efficiently.
Top ten essential cyber security tips
Many small business and SMEs have limited resources to utilise on security.
Cyber criminals know this, and leverage this as an opportunity to target small and medium businesses for this reason, essentially betting that you’ve neglected to protect yourself.
Ultimately, the level of impact on your business will be dependent on 3 things:
- The opportunities you allow for an attacker (in terms of system vulnerabilities)
- The exploitation capability of an attacker
- Their motivation for targeting your business
However, with careful planning and creative strategy, most small and medium businesses can undertake the essential activities to ensure their business is kept secure.
With limited resources, it is easy to overlook best practices, but observing these guidelines will prevent the majority of cyber attacks:
1. Effective management of user privileges
- Limit user privileges to named individuals and monitor user activity.
- Define users, account holders and access rights.
- Establish controlled access to activity and audit logs.
- The establishment of effective management processes to limit the number of privileged accounts will prevent misuse of accounts and introduce accountability for the defined users.
2. Ensure network security
- Defend your organisation’s network perimeter by filtering out unapproved access and maliciously intended content.
- Regularly monitor and assess security controls.
3. Establish and maintain disaster recovery protocols
- Establish disaster recovery and incident response principles and systems.
- Schedule the regular testing of your disaster recovery and incident response plans.
- Where necessary, provide training for disaster recovery and incident management.
- Establish clear escalation procedures to report criminal instances to legal authorities.
4. Establish a risk management system
- Evaluate any risks which may leave your information and systems vulnerable or exposed and prioritise to the same level as financial, legal, regulatory or operational risks.
- Embed risk management systems across your business which have the support of the senior managers and the board.
5. Improve user awareness and education
- Create a user security policy which define the secure and acceptable use of your business systems.
- Embed cyber security awareness as part of staff training and staff recruitment.
- Maintain an awareness of potential cyber risks by regularly providing staff with training and re-enforcing cyber security best practices.
6. Monitor and observe
- Create strategy for monitoring and design the necessary supporting policies.
- Embed the supporting policies into your day-to-day management activities.
- Regularly monitor all networks and systems.
- Continuously analyse system and network logs for suspicious activity that may be indicative of a cyber attack.
7. Take preventative actions against malware
- Create appropriate policies and implement anti-malware tools across your business.
- Ensure your systems are kept updated with the latest manufacturers’ updates.
- Deploy anti-virus/anti-malware solutions for documents and emails.
8. Develop a home and mobile working
- Establish a remote working policy and ensure adherence.
- Take steps to ensure data is secure in transit and when stationary, by encrypting mobile devices.
- Ensure staff are using a secure VPN to access the business systems.
9. Implement removable media controls
- Create a policy which governs the access of removable media devices, such as phones, tablets, USB etc.
- Limit the types of media types and their use – where possible, promote the use of secure cloud to share files and documents.
- Enable the scanning of media for malware upon connection to business systems.
10. Secure and maintain system configuration
- Ensure the latest security patches are applied and systems are securely configured.
- Produce an inventory of your systems identify a baseline build for all business devices.
- Ensure the secure baseline and build is applied to all devices.
Other ways to protect your business from cyber crime
Due to the potential risks, cyber security can seem daunting to small and medium businesses.
However, more security technology and tools are available to SMEs today, than ever before. Smaller companies don’t necessarily need to dedicate large number of resources and budgets to ensure their business is secure.
For most SMEs, following best practices and educating your employees will be sufficicient in protecting your business. However, futher option exist for those small and medium businesses that do wish to look at other ways to further minmise their risk exposure.
Small businesses that want to protect themselves from a cyber threat may need a more tailored and holistic cyber security plan. Some small and medium companies hire specialist consultants or firms who will work you and advise you on a tailored cyber security plan and provide the appropriate services to address your specific security risks.
This may be beneficial is your work in a regulated or commercially sensitive industry such as healthcare, finance or defence. To understand the advantages (and disadvantages) of outsourcing your cyber security to a service provider and what to look for in a provider, Infosecurity Magazine provides some useful tips.
With an increase in cyber attacks, many SMEs are now taking insurance covers cyber crime. If you do decide to take cyber and data risks insurance policy make sure you understand exactly what it does and does not cover.

