Types of malware businesses must protect against

The introduction of government initiatives, such as the Cyber Essentials scheme and GDPR, has led to an increase in cybersecurity awareness amongst businesses, causing the nature of cyber attacks to change in the last few years. While the types of malware attacks have seen a decrease, several malware types still represent a significant proportion of attacks on businesses.
Malware continues to grow and evolve, with a new type of malware attack available every other year – the threat from various types of malware attacks remains considerable.
In this article, we identify the different types of malware, describing what malware is, the impact malware has on businesses, and what steps companies should take to protect against several types of malware.
In this article, we explain:
On this page:
What is malware?
Malware (Malicious software) is a “catch-all” term for a code or program which is hostile and harmful to computer applicatons, hardware and infrastructure.
Malware can have different forms and functions. Viruses, worms, trojans, rootkits, spyware, adware, ransomware and botware are all types of malware.
All malware is, by design, intended to be intrusive. Malware seeks to infect, damage and immobilise computers, computer networks, tablets, mobiles and laptops. With the sole aim of extorting money from the target organisation.
Consequently, malware will seek to infiltrate and disrupt the target, by stealing, encrypting, deleting and hijacking severely hampering core functions to achieve its aim forcefully.
How does malware affect businesses?
The anonymity offered by the internet, coupled with its cross-border nature, provide cybercriminals with the perfect cover from which to launch attacks against organisations.
In particular, small and medium businesses and not-for-profit organisations, are lucrative targets for malware, with over 60% of attacks targeted towards companies with less than 1,000 employees (Varonis, 2018).
A well-executed malware attack could cripple your day-to-day operations. Such an attack could result in a complete breakdown of your computer network or the loss of critical data, leading to lost sales, custom and future business.
Several types of high profile malware attacks have been seen over the last few years:
- CovidLock, 2020 – Ransomware: The recent Coronavirus (COVID-19) pandemic has been greatly exploited by cybercriminals. The CovidLock ransomeware uses malicious files to infect victims with the promise of providing more details about Coronavirus. Once installed, Android device data is encrypted by CovidLock, denying data access to the victim. CovidLock victims must pay USD100 per device to be granted access to their data.
- LockerGoga, 2019 – Ransomware: LockerGoga infected large corporations, like Altran Technologies and Norsk Hydro. LockerGoga ransomware attacks include credential theft, malicious emails, and phishing scams. LockerGoga completely blocks system access. It is estimated that LockerGoga caused millions of dollars in damage in advanced and targeted attacks.
- Emotet, 2018 – Trojan: This trojan, became famous after the US Department of Homeland Security labelled Emotet as a leading destructive type of malware. Emotet received widespread attention due to its targeting of financial data theft, such as cryptocurrencies and bank logins. Emotet’s spread via malicious emails in the form of spam and phishing campaigns.
- WannaCry, 2017 – Ransomware: One of the worst ransomware attacks in recent history. WannaCry, caused infections via phishing emails, and impacted the UK’s national health service (NHS), exploiting a vulnerability in Windows XP. Estimate indicated that more than 200,000 people worldwide have been reached by WannaCry, including public sector bodies (hospitals, universities) and large enterprises (FedEx, Renault). Losses due to WannaCry are estimated to exceed USD4 billion.
- Petya, 2016 – Ransomware: Petya blocks the machine’s entire operating system. To release it, a ransom has to be paid by the victim. It is estimated that USD 10 billion in losses have been incurred by its victims since Petya and its more new and destructive variations was released. Victims of Petya have included banks, airports and oil and shipping companies from across the globe.
How can businesses protect against malware?
Most types of malware infections will go unnoticed, clandestinely impacting your business and operations in the following ways:
- Steals sensitive information and confidential data
- Allows unauthorised access to computer or server resources, such as CPU and memory
- Slows applications and web browsers
- Interferes with network connections and resources
- Results in frequent freezing or crashing of applications and hardware
Consequently, businesses must take the necessary precautions to detect and prevent malware infections. The lack of antivirus software and firewalls will freely let malware infiltrate your organisation and stay concealed until it has caused extensive damage.
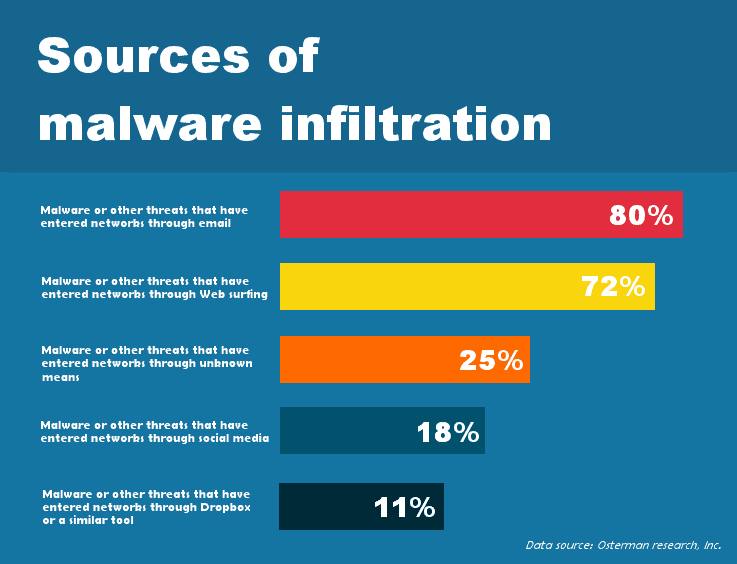
The primary sources of malware infection
Your organisation is most likely to experience a malware attack from several different types of malicious software from the following sources:
- Internet: A large proportion of malware attacks originate on the internet. For example, you may visit a website which contains malicious code or inadvertently download a malicious disguised as an ordinary application. A significant majority of malware is also concealed in files downloadable via peer-to-peer networks (torrents).
- Email: Different types of malware can also be hidden in the body of an email or the attachments. The opening of such emails or attachments will execute the malware to infiltrate your computer. For example, as part of a social media scam, users could also receive phishing and spam emails which entices them to a website containing malicious code.
- Software vulnerabilities: Software vulnerabilities can be exploited to allow cybercriminals to gain remote access to your data, as well as network resources and sources of confidential information. This may be perpetrated by enticing users with a fake patch or update.
- External storage drives: External drives and network folders could harbour malware. If users inadvertently execute a malicious application on an external drive, the malware could propagate a virus to all computers, wiping or encrypting the crucial data.
- New users: Another user, particularly new users, not familiar with the organisation’s cybersecurity policy, may inadvertently cause systems to become infected without realisation. Cybercriminals are known to use social engineering techniques to lure users into installing and running malware.
10 Tips to avoiding common types of malware attacks
As with most malicious activities, avoidance is best. Keeping your IT programs, applications, infrastructrure and hardware healthy and secure, through the use of robust antivirus and firewalls, and best practices, most organisations can avoid or minimise the impact of any malware infiltration.
Here are our top ten tips to help you protect your business against malware:
1. Be aware of the website you visit – Pay attention to domain names that end with obscure letters, for example, domain names ending in .com, .org, .edu, .co.uk, to name a few, are, in general trustworthy. Cybercriminals can set up spoof websites using uncommon TLDs, containing malicious code.
2. Keep your IT systems up-to-date – Ensure the operating systems, browsers, and plugins are always up to date with the latest manufacturers patches and updates.
3. Avoid clicking on suspicious web links – Instruct users to not click on pop-up ads while browsing a website. Users should refrain from clicking on unverified links in unsolicited emails, texts and WhatsApp messages. Downloading software from peer-to-peer file transfer networks or untrustworthy websites should also be avoided. Train users to avoid executing executable files and avoid enabling macros on Office files.
4. Be mindful of mobile devices downloads – For mobile devices, only download apps from Google Play Store or Apple’s App Store. Be wary and check the ratings and reviews first. It is best to avoid apps which have low ratings and downloads. Android devices have a function to switch off downloads from third-party sources.
5. Develop a mobile device security policy – To prevent malicious apps from threatening their computer networks, organisations should develop strong mobile security policies and deploy a mobile security solution to enforce those policies.
6. Invest in strong antivirus software – Business can invest in a good antivirus/anti-malware program with layered protection. This will scan and detect malware, such as adware and spyware while maintaining a proactive real-time defence to block threats such as ransomware. Any security program should also provide remediation and return the infected application or program to the last known normal state.
7. Follow network security best practices – Large networks can be segmented into smaller subnetworks – smaller targets are harder to attack. This will help to contain any breaches to a limited number of endpoints instead of your entire network.
8. Backup your data – Backup all your data, including all endpoints and network shares. This will allow you to wipe the infection and restore from a backup.
9. Educate employees – Businesses should educate employees on how to create strong passwords and should implement multi-factor authentication (MFA) where possible.
10 . Purge old or unused software and applications – Remove and get rid of old software which is past its expiration date. Updates for old software are rarely available, allowing malware to be developed to exploit security loopholes. Cybercriminals actively seek outdated and obsolete software to target.
How to remove common types of malware
There are three simple steps organisations need to take if they suspect a malware infection, or if they simply want to be cautious:
- Firstly, invest in a legitimate antivirus/anti-malware program. But before paying for an antivirus subscription, you can check out these free malware scanning and removal tools.
- Two. Once downloaded, install the application and run a scan. Anti-malware applications are intended to seek and eliminate any malware on your device.
- Lastly, once the device has been cleaned and any malware eliminated, it is a good idea to change your passwords. Make sure you change all passwords. Not only for the PC or mobile device, but also email, social media accounts, e-commerce sites, and online banking.
Note: Apple iPhone does not allow scans of its system. The only choice is to wipe the phone with a factory reset, then restore it from a backup.
The 7 different types of malware
Presented below are descriptions for the different types of malware, and their attack and infection methods.
Adware
Adware aims to force unwelcomed advertisements onto the user’s screen. The purpose of this is to compel users to watch an ad which will, as a result, earn cybercriminals money.
If users have been led to a different page to that which they clicked on, the likely cause is adware. In most cases, users will finally reach the page that they intended to visit. However, the injection of a random advertisement in your page code, can slow down browsers and make browsing the internet cumbersome.
Adware also works by altering application settings on the local computer. For example, certain types of adware will hijack your internet web browser and add unwanted search engines, toolbars, and even change the default home page on the New tab page.
Ransomware
An increasingly common type of malware attack, ransomware has risen to prominence in the last few years due to some high profile cases. In a ransomware attack, initially, no target data is damaged or lost. Instead, it is encrypted, effectively locking the user out of using that data, with the cypher key only being provided once a ransom has been paid. Ransomware can spread very fast and is typically instigated and propagated via trojans or worms.
The rise in prominence of ransomware correlates with the increasing popularity of cryptocurrencies, such as Bitcoin, which offer a degree of pseudo-anonymity to hackers. This makes it difficult for law enforcement officials to trace the perpetrators even once the money has been transferred to the bank account.
Ransomware is nothing more than a digital protection racket. With companies receiving a demand for a ransom and warnings that if not paid, their data will be lost forever. Unfortunately, most companies do not take any chance and pay the ransom.
The WannaCry ransomware in 2017 received extensive media attention. In the UK, the malware severely impacted the national health service (NHS), leading to an acute increase in awareness in ransomware.
Rootkit
A rootkit is a type of malware which has aims to gain privileged access, while remaining undetected. Not all rootkits are malware. However, those with malicious intent take privileges such as admin rights, gain full and unfettered access to the system. A rootkit can be used to install other malware, changing the names of the malware to hide its real intent, appearing as an innocent application to the user.
Rootkits spread via injection. Injection methods vary but can include piggybacking, whereby the rootkit is bundled with genuine software, such as an application plugin. Other injection methods include blended threat, whereby the rootkit takes advantage of vulnerabilities on the system, or via infected mobile apps.
Rootkits are very powerful. A more sophisticated type of rootkit malware is Ghostware which simply hides its existence, altering parts of the machine to make them appear healthy, thereby rendering the malware invisible to the computer user.
Spyware
As the name suggests, the purpose of spyware is to spy on your activities to report and steal data. Spyware will clandestinely collect and share potentially sensitive data with the cybercriminal, who will either use it or sell the data to whoever finds that information valuable.
Spyware infects machines via conventional malware attack sources including websites, email and ads. Spyware relies on an active internet connection since one of the critical functions of spyware is to send information back to the cybercriminal.
There are four types of spyware, namely, keyloggers, password stealers, infostealers and mobile spyware. You may sometimes see adware identified as the fifth type of spyware.
- Keyloggers: Also known as system monitors. Keyloggers record keystrokes entered on the keyboard. This data is then sent back periodically to the creator, who can reassemble the information to obtain sensitive and confidential data.
- Password stealers: This type of malware steals passwords entered on computers, including login details. Password stealers can steal passwords for email, banking and social media accounts.
- Infostealers: Used by third parties to collect sensitive information entered on an infected machine. This confidential information could include usernames, passwords, browser history, log files and emails. Infostealers typically infect a computer via web browser vulnerabilities.
- Mobile spyware: This targets mobile phones. This type of spyware is attached to SMS and MMS messages, infecting phones when they receive the message without any user interaction. The spyware will then use the mobile’s camera and microphone to snoop on the user, monitoring mobile’s web browser search history, and phone calls.
Trojan
This type of malware tricks users by posing as legitimate software. Once the trojan is downloaded, opened and executed on a computer, the trojan is activated and will have access to the system. Trojans typically infects via two general methods — either by hiding within a piece of software or through phishing.
Trojans can be attached to software downloads. A popular choice is to hide a trojan within freeware and shareware games. In phishing, the trojan is installed via a downloaded file from an email that has portrayed itself to be a trusted source. Trojans are now often delivered in Microsoft Office and PDF files to avoid suspicious executable files from unknown or random sources.
Different types of trojans exist and can be broadly categorised as follows:
- Backdoor Trojans: This type of trojan, once executed, creates vulnerabilities in the infected system’s security which allows other attacks to be perpetrated.
- Downloader Trojans: Downloader trojans act as a delivery mechanism to download malicious code, typically from the cybercriminal’s website, with the aim to gain control of the target.
- Rootkit Trojans: These trojans aim to install a rootkit which can be used by other attackers to gain access.
- Exploit Trojans: This type of trojan target specific vulnerabilities within the target and contains code which exploits this opportunity.
Virus
Viruses are one of the most commonly known types of malware. Viruses hide within application code and replicate until it has achieved its programmed task. When not reproducing, viruses will modify legitimate programs in a compromised system to insert its code.
A classic mainstay of malware, viruses have been around for a long time, historically being delivered via infected floppy disks and spreading through the circulation of these infected disks. With the prevalent use of the internet, the delivery mechanism has advanced to emails, files and websites.
A virus is activated by a user using a regular application which has been unwittingly infected. When the application is started, the virus code is executed.
There are 4 distinct phases in a virus attack, namely, dormant phase; propagation phase; triggering phase and execution phase.
- Dormant Phase: Not all viruses exhibit this phase; however, during the dormant phase, the virus is idle while residing in the infected system. In this phase, the virus requires interaction from the user to activate and trigger its malicious activity.
- Propagation Phase: The propagation phase is when the virus reproduces and attempts further infection. During reproduction, the virus clones itself to infect different programs and different parts of a system. Clones may not be identical to the original virus and are likely to change over time to avoid detection from antivirus software. However, each of these clones can replicate in the same way, meaning a system can become overwhelmed with an infection in a very short time.
- Triggering Phase: Once activated, the virus enters the triggering phase and executes the task(s) that it was intended to perform. This phase can be caused by running an application, or in some cases by a system event, for example, a reboot. Once triggered, the virus intends to deliver a payload to the broadest number of systems as possible.
- Execution phase: Viruses aim to deliver a malicious payload onto the compromised system. This payload could be minor, such as causing a pop-up to appear, or widely damaging, deleting files and folders.
The easiest way to prevent viruses is by installing an antivirus program into your system. While many modern operating systems now come with a bundled antivirus system, investing in business grade antivirus software will provide enhance protection and security.
See also: 10 free virus and malware removal tools
Worm
Worms, while similar to viruses, have a fundamental difference. Worms do not require user interaction (activation) to perform its programmed task, such as deleting files and stealing data. Worms commonly attack vulnerabilities that exist within the application or infrastucture.
Since worms act independent of the actions of third parties, they do not have an easily identifiable lifecycle. Once infected, worms will replicate, identifying other computers on the network, and execute its programmed task. Worms exist in several different forms, each having their own mechanism of infiltrating:
- Bot worms: Bot worms are a type of malware worm which infects intending to turn the victim computer into a bot or zombie. The infected machine is then used with other compromised machines to form botnets (robot network). Cybercriminals use botnets to launch large-scale, coordinated attacks, such as denial-of-service attacks (DoS). A DoS using multiple computers globally is known as a distributed-denial-of-service attack (DDoS); essentially, many infected computers working in unison. Users of the computer in a botnet may not even realise that their computer is taking part in DDoS attack. In a similar vein, a bot worm can be used for Cryptojacking – infecting and using unwitting machines to mine for cryptocurrency.
- Email worms: Email worms initiate infection either by the way an infected email attachment which infiltrates the target computer upon download or via a malicious link which will infect the target machine when clicked. A well-known instance of an email worm is the ILOVEYOU worm, which in 2000, had infected millions of systems.
- Internet-based worms: An internet-based worm is not picked up via web browsing; instead, it is spread when infected computers scan the internet for vulnerable machines that can be infected. Taking advantage of machines that have not received security and operating system updates, the worm identifies the vulnerabilities that have been fixed recently. From here, the worm locates a computer that has not yet had these updates installed.
- File-sharing (P2P) network worms: File-sharing networks have a glaring security weakness – you rarely know what you are downloading. This type of worm relies on users to be enticed to download an infected file, such as the latest movie or application, onto the machine. Once downloaded, the worm will execute the malicious actions it is programmed to do and self-replicate.
- Chat room and instant message worms: Similar to the email worm, this worm will use the contact list to send out messages containing malicious links. Typically, these links will direct the user to a malicious website laden with malicious worms, or it may simply download the worm itself.

