UTM: Unified Threat Management – A Pragmatic Approach for Information Security

Despite the billions of dollars spent on cyber security annually, new threats continue to emerge. The latest include misusing biometric info, compromising supply chains, crypto-jacking and using artificial intelligence for hacking company networks. A newer, more effective approach is needed, and many believe the answer is UTM, or unified threat management security.
On this page:
What is UTM (Unified Threat Management)?
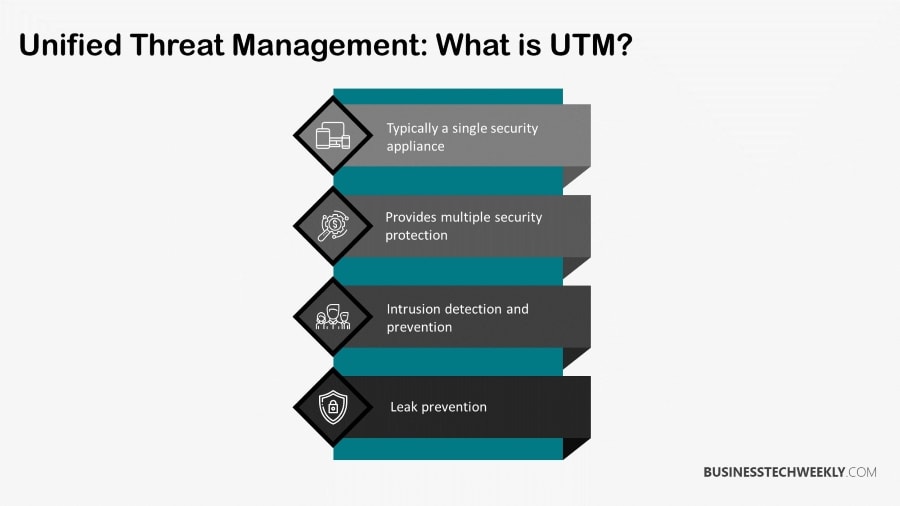
Unified threat management (UTM), refers to a single security solution, which fulfills multiple security protection roles in a single device or service on the network.
UTM appliances will typically provide anti-virus, anti-spyware, and anti-spam protection, in addition to network firewalling, content filtering, leak prevention, and intrusion detection and prevention (IDP).
RELATED: Types of malware businesses must protect against
More advanced devices will also provide services such as network address translation (NAT), remote routing, and virtual private network (VPN) support.
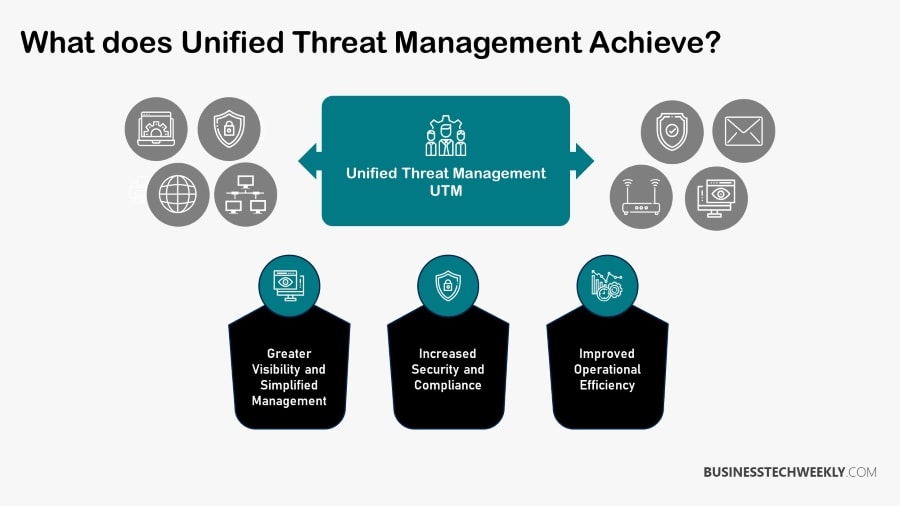
Simplicity is the primary attraction of UTM devices. A single UTM appliance which can perform all crucial security tasks, supported by one vendor, IT team, and administered through a single console.
How does Unified Threat Management (UTM) work?
UTM offers numerous security countermeasures for one network or device that defends users. It consists of anti-spam, web filtering, anti-virus, and content filtering.
Information Technology workers have to frequently devise ways to shield and maintain digital assets and organizational productivity against sophisticated and constantly evolving threats. Examples of such threats include viruses, spyware, Trojans and phishing. These dangers often have to be addressed with limited resources and budgets.
RELATED: Threat Detection and Response: Best Practices
Using numerous devices which are separated and configured to carry out particular security functions won’t make the task easier. Instead, the complexity and cost of managing different operating systems and tools increase.
UTM comes in the form of one system that solves multiple problems simultaneously. It accomplishes this by:
- Securing your network against malware, malicious attachments and viruses by incorporating Deep Pocket Inspection to scan any incoming data
- Blocking access to undesirable websites through increased web filtering
- Empowering administrators to handle a broader range of security-based functions from one management console
- Inspect packet headers to block attacks before they access the network
- Automatically updating to the newest virus definitions and security updates with minimal intervention by end-users
Benefits of Using United Threat Management
UTM will deal with spam by blocking or tagging unwanted email traffic by scanning outbound and inbound traffic.
This filtering enables users to utilize SBL (server-based spam block list) to white or blacklist email messages. For viruses, it will use both a database and scanning engine to protect networks and users against worms, spyware, malware and infected files via FTP, POP, HTTP, IMAP and SMTP protocols.
It is also possible to merge signature-based detection with the newest anti-malware countermeasures to identify and neutralize threats before they cause harm.
Content filtering is essential for preventing the loss of data. Traffic will be filtered based on the file extension, protocol commands and MIME type. Content filters may also be used to block Java Applets or ActiveX.
Additionally, some forms of UTM content filters don’t require an additional license. Web filtering is accomplished by using SurfControl servers, which are internet-based or Websense servers that are localized. Web-based filtering makes it easier to track the behavior of users as well as their productivity.
Why UTM is the Best Way to Mitigate Viruses
UTM based appliances will typically provide functions like network firewalls, leak prevention, and the ability to detect and block intruders.
The most advanced systems also offer NAT (network address translation), VPN (virtual private networks) and remote routing. These solutions are preferred due to their ease of use and simplicity.
In the past, it wasn’t unusual for a single corporation to have multiple vendors for each security task, but with UTM, everything can be consolidated beneath a single umbrella which is managed by one Information Technology team and processed through a single console
Viruses, in particular, have always been a threat, and new ones are being developed all the time. They are now being used in combination with malware to simultaneously target separate areas of company networks.
Stopping these attacks has historically been challenging because separate vendors were used. Each one must be individually updated and managed to stay current against the newest threats. UTM produces one defensive point, utilizing one console to address many evolving threats.
Unified Threat Management Drawbacks
While UTM is highly effective, it is not perfect.
Despite its ability to resolve various network security challenges, its centralized defensive point can also become a centralized point of collapse. For this reason, many institutions decide to supplement UTM with secondary software perimeters to deal with viruses or malware that manage to bypass the firewall of the UTM.
Traditional Security Solutions are no longer adequate
The advent of cloud and mobile-based technology has substantially changed the industry. IT experts are faced with the daunting task of quickly scaling up to account for these technologies while facing cyber-attacks which are doing the same.
It isn’t enough to address existing threats; IT departments must also watch the security horizon to prepare for the next hazard.
Data is being created faster, and this, combined with the growing complexity of the IT atmosphere, makes it quite challenging for institutions to secure their systems.
The line between hybrid, private and public cloud resources has become blurred, meaning that hazards can arise from multiple directions and endanger any system.
United threat management encompasses both software and hardware. It combines traditional security solutions with emerging technologies like automation and artificial intelligence. However, every organization must decide on complexity compromise.
What Is Complexity Compromise?
Complexity compromise is a phenomenon where greater security is usually complex and erodes end users’ experience.
A recent study found that nearly ninety per cent of institutions now utilize digital transformation in some form, which is used to enhance their services and products.
The challenge is that no effective roadmap has been developed for this transformation. Markets which prioritize digital solutions reward those who operate with substantial speed, but multiple solutions must be employed like analytics, cloud deployments and data collection.
As a result, institutions have been compelled to adopt numerous security approaches to compete, which has led to an overly complex and fractured environment to the point where security is ironically compromised.
This is the essence of complexity compromise: The greater the complexity of the IT environment, the harder it is to utilize effective cybersecurity methods like visibility in real-time or data protection.
Such environments are a boon for malicious actors because it enables them to bypass the threat management tools despite IT experts trying to increase their defenses.
Multi-vendor Defensive Collaboration
One aspect of UTM that is gaining traction is multi-vendor defensive collaboration.
Interoperability between security offerings and vendors has historically been limited. But since markets are in the process of standardizing, multi-vendor defensive collaborations have emerged. Many of their solutions comply with the NIST Security Framework and have reduced overall complexity while increasing security.
While detecting and preventing threats is essential, it is also vital to devise a way of contesting malicious actors once they access the system.
No organization is impervious to compromise. Many cyber security experts feel that institutions put so much energy, time, and money into preventing system infiltration that they spend little time planning what to do once cybercriminals have entered the system.
Multi-vendor defensive collaboration makes it easier to think and behave like hackers, which will make it easier to develop countermeasures, especially when combined with IR (incident response) plans.

