Fortifying Your Online Presence: Web Server Hardening

One of the key aspects of fortifying your online presence is web server hardening, which involves implementing a series of security measures to protect your web server from potential threats.
In order to fortify your online presence, it is essential to assess your current security measures and identify any potential vulnerabilities. This involves conducting a thorough evaluation of your web server’s configuration, encryption protocols, and access controls.
By focusing on these foundational aspects of web server hardening, you can significantly reduce the risk of unauthorized access, data breaches, and other security incidents.
On this page:
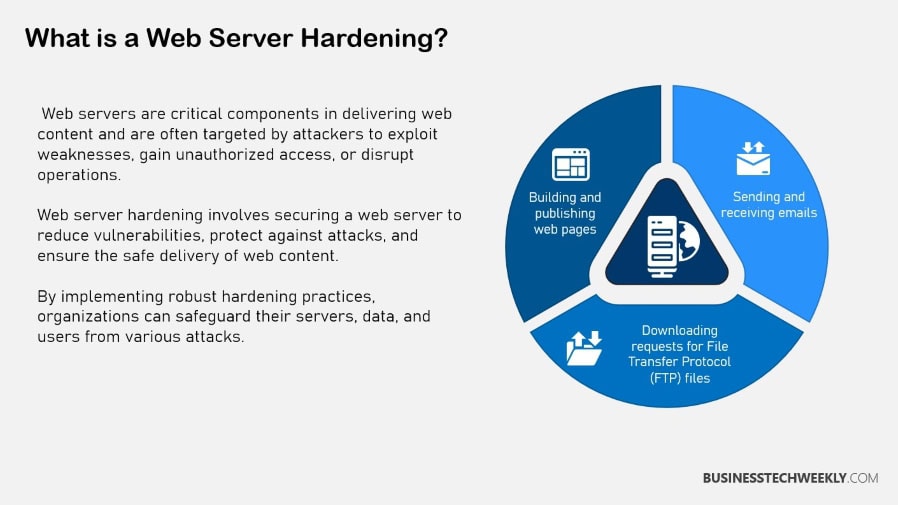
What is Web Server Hardening?
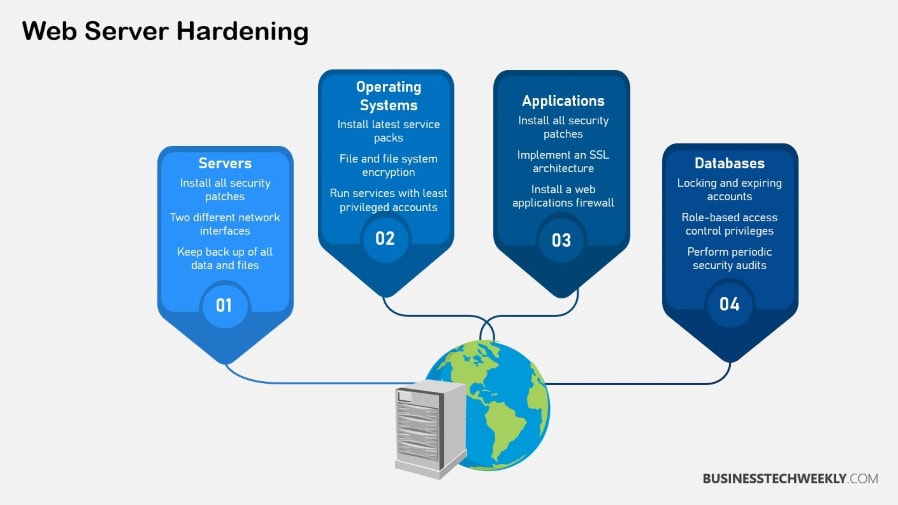
Web server hardening is the process of configuring and securing a web server to minimize vulnerabilities, protect it against cyber threats, and ensure reliable delivery of web services.
It involves a combination of best practices, security configurations, and tools to fortify the server and its hosted applications against attacks such as unauthorized access, data breaches, and denial-of-service (DoS).
Purpose of Web Server Hardening
- Reduce Attack Surface: Remove unnecessary features, services, and configurations that could be exploited.
- Enhance Security: Protect sensitive data and resources by implementing robust security measures.
- Ensure Compliance: Meet security standards and regulatory requirements (e.g., PCI DSS, GDPR).
- Maintain Performance: Optimize the server to handle traffic securely and efficiently.
Assessing your Current Security Measures
The first step in web server hardening, is to assess the current security measures. This allows for an unbiased evaluation of the existing vulnerabilities and instills a sense of urgency in implementing necessary improvements.
By conducting a comprehensive assessment, you can identify potential weaknesses in your web server’s defenses, such as outdated software, misconfigured settings, or weak authentication mechanisms.
This evaluation provides a clear picture of the risks your online presence is exposed to, enabling you to prioritize and address the most critical vulnerabilities first.
Furthermore, assessing your current security measures empowers you to take proactive steps in strengthening your web server’s defenses. It serves as a wake-up call, reminding you of the ever-evolving nature of cyber threats and the importance of staying one step ahead.
This evaluation instills a sense of urgency and responsibility, motivating you to invest time, effort, and resources in implementing necessary improvements.
By identifying and rectifying vulnerabilities in your online presence, you not only protect your own data but also contribute to the collective freedom of the online community.
The more resilient your web server becomes, the harder it is for malicious actors to compromise it, ultimately fostering a safer and more secure digital environment for everyone.
Update and Patch Your Web Server
Updating and patching a web server is crucial for ensuring its security and resilience against potential vulnerabilities and cyber threats.
Web servers are constantly targeted by hackers and attackers, who exploit known vulnerabilities in outdated software versions. By regularly updating and patching your web server, you can stay ahead of these threats and protect your online presence.
Updates and patches are released by software vendors in response to newly discovered vulnerabilities or bugs. They often include fixes and improvements that address these issues and enhance the overall security of the web server.
Failing to update and patch your web server can leave it exposed to various security risks. Hackers can exploit known vulnerabilities to gain unauthorized access, compromise data, or launch malicious attacks.
Outdated software versions may also lack important security features and mechanisms that have been introduced in later updates.
By neglecting updates and patches, you not only increase the likelihood of a successful cyber attack but also miss out on the opportunity to benefit from the latest security enhancements.
Therefore, it is imperative to regularly check for updates and patches provided by the web server software vendor and promptly apply them to fortify your online presence and protect against potential threats.
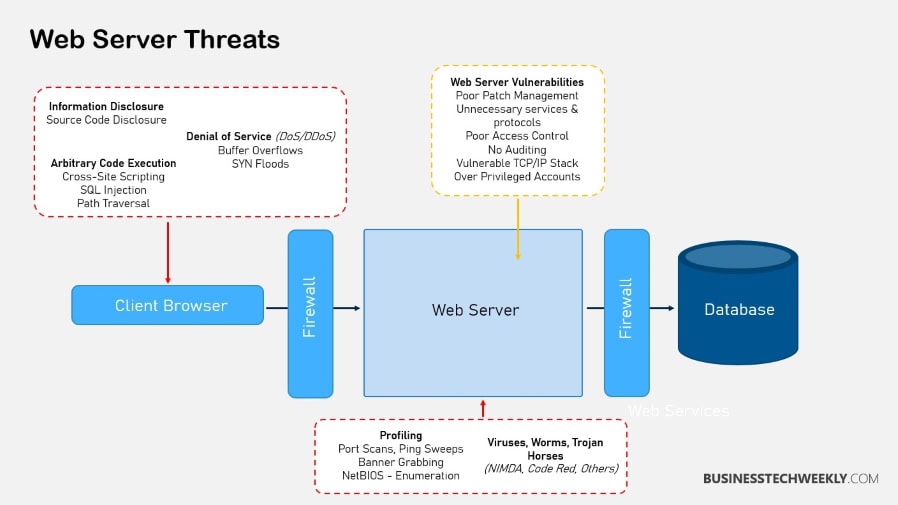
Secure Access to Your Web Server
Ensuring secure access to a web server involves implementing robust authentication measures and configuring firewall rules to control incoming and outgoing network traffic.
Authentication is a critical component of secure access, as it verifies the identity of users before granting them access to the server. This can be achieved through the use of strong passwords, multi-factor authentication, or even biometric authentication methods.
By implementing these measures, unauthorized individuals are prevented from gaining access to sensitive data or compromising the server’s security.
In addition to authentication, configuring firewall rules is essential to secure access to a web server. Firewalls act as a barrier between the server and the external network, monitoring and controlling incoming and outgoing traffic.
By setting up firewall rules, administrators can specify which IP addresses or networks are allowed to access the server and restrict access from unknown or unauthorized sources.
This helps prevent malicious attacks and unauthorized access attempts, further fortifying the server’s security.
To grab the attention of the audience, here are three key points to consider in securing access to a web server:
- Implement strong authentication measures such as multi-factor authentication or biometric authentication to verify the identity of users.
- Configure firewall rules to control incoming and outgoing network traffic, allowing access only from trusted sources.
- By ensuring secure access to the web server, individuals can protect their sensitive data and maintain the integrity of their online presence.
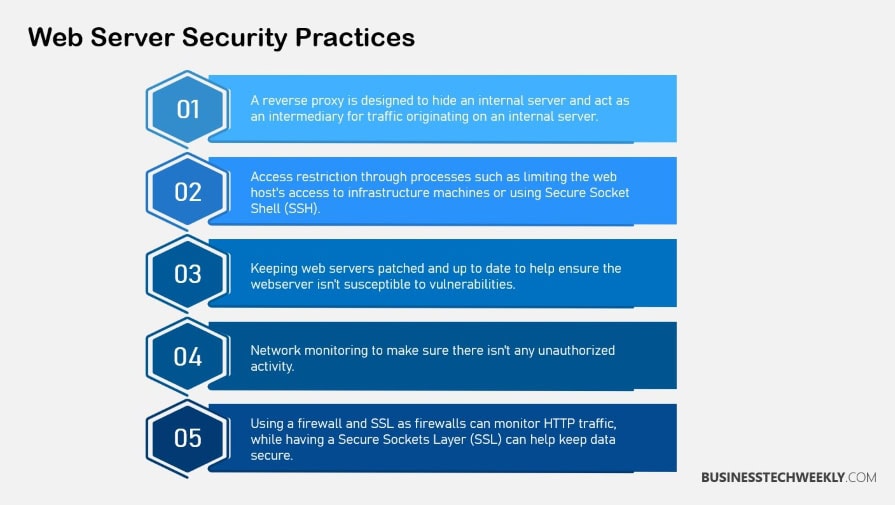
Harden your Web Server Configuration
This paragraph will discuss the key points of hardening your web server configuration.
The first point is to disable unnecessary services and ports, which helps to minimize potential security vulnerabilities.
Secondly, configuring a firewall and intrusion detection systems can further protect the web server by monitoring and controlling network traffic.
Lastly, enabling secure HTTPS encryption ensures that data transmitted between the web server and clients is encrypted, preventing unauthorized access or interception.
These measures collectively enhance the security of the web server and safeguard against potential threats.
Disable Unnecessary Services and Ports
Disabling unnecessary services and ports enhances the security of your web server, effectively fortifying your online presence and instilling a sense of confidence in your audience.
By disabling these services and ports, you minimize the potential attack surface for hackers and reduce the risk of unauthorized access to your server.
Here are three key reasons why disabling unnecessary services and ports is crucial for web server hardening:
- Increased protection against network attacks: Disabling unnecessary services and ports eliminates potential entry points that hackers can exploit to gain unauthorized access to your server. Each open service or port represents a potential vulnerability that can be targeted. By closing off these unnecessary services and ports, you significantly reduce the chances of a successful network attack.
- Improved resource allocation: Running unnecessary services and keeping unnecessary ports open can consume valuable system resources, such as CPU and memory. By disabling these services and ports, you free up these resources, allowing your web server to operate more efficiently. This improved resource allocation leads to better performance and responsiveness, ensuring a smoother user experience.
- Simplified server management: Having fewer services and ports to manage simplifies the overall server administration process. With a reduced number of services, there is less complexity and fewer potential points of failure. This simplification not only improves the efficiency of server management but also reduces the chances of misconfigurations or vulnerabilities being introduced during the maintenance or upgrade process.
Disabling unnecessary services and ports is a crucial step in fortifying your web server’s security. It not only enhances protection against network attacks but also improves resource allocation and simplifies server management.
By taking these measures, you can strengthen your online presence and provide your audience with a secure and reliable browsing experience.
Websites currently experience an average of 94 attacks every day, and are visited by bots approximately 2,608 times a week.
Configure Firewall and Intrusion Detection Systems
Configuring firewall and intrusion detection systems is an essential step in enhancing the security of a web server, as it helps to identify and block unauthorized access attempts and malicious activities.
Firewalls act as a barrier between the server and the external network, monitoring incoming and outgoing traffic and making decisions based on predefined rules.
By configuring the firewall, administrators can control which services and ports are accessible from the internet, effectively limiting the potential attack surface.
This ensures that only necessary services are exposed to the outside world, reducing the risk of exploitation.
Intrusion detection systems (IDS) complement firewalls by actively monitoring network traffic and analyzing it for signs of unauthorized or malicious activities. IDS can detect and alert administrators about various types of attacks, such as port scanning, brute-force login attempts, or suspicious network behavior.
By configuring IDS to analyze and respond to these threats, administrators can proactively protect the web server from potential vulnerabilities.
Additionally, IDS can provide valuable logs and reports that help in identifying patterns and improving the overall security posture of the server.
By implementing robust firewall and intrusion detection systems, web server administrators can provide a secure environment for their users and ensure the integrity and availability of their services.
Enable Secure HTTPS Encryption
Enabling secure HTTPS encryption involves implementing a cryptographic protocol that ensures data communication between a web server and client is encrypted, providing confidentiality and integrity of transmitted information.
HTTPS, which stands for Hypertext Transfer Protocol Secure, is the secure version of HTTP. It utilizes SSL (Secure Sockets Layer) or TLS (Transport Layer Security) protocols to encrypt data as it is transmitted over the internet.
This encryption ensures that any data exchanged between the web server and the client cannot be intercepted or tampered with by unauthorized individuals or malicious attackers.
RELATED: Understanding the benefits of an SSL Certificate for your Business Website
By enabling secure HTTPS encryption, individuals and organizations can protect their sensitive information from being compromised.
This is particularly important for activities such as online banking, e-commerce transactions, and accessing personal accounts.
With the increasing prevalence of cyber threats and the growing concern for online privacy, implementing HTTPS encryption has become a critical step in fortifying one’s online presence.
Moreover, secure HTTPS encryption also enhances the trust and credibility of a website, as it provides users with the assurance that their data is being transmitted securely.
As individuals strive for freedom in the digital world, enabling secure HTTPS encryption is a key step towards safeguarding their online activities. It empowers users to have control over their personal information and ensures that their online interactions remain confidential.
By adopting this encryption protocol, individuals can enjoy the freedom of browsing, shopping, and communicating online without the fear of their data being intercepted or compromised.
Secure HTTPS encryption allows users to exercise their right to privacy and protects them from potential threats in the ever-evolving digital landscape.
It is an essential measure for those who value their online freedom and seek to fortify their online presence.
Regularly Backup your Website and Data
One key point is to implement automated backup solutions, which can help ensure that backups are performed consistently and on a regular basis.
Additionally, it is recommended to store backups in secure offsite locations, such as cloud storage or remote servers, to protect against physical damage or loss.
Lastly, it is crucial to test and verify the integrity of backups to ensure that they can be successfully restored if needed.
By following these practices, website owners can safeguard their data and minimize the impact of potential data loss or security breaches.
Implement Automated Backup Solutions
Implementing automated backup solutions is a crucial step in fortifying your online presence, as it ensures the preservation and availability of valuable data, mitigates the risk of data loss, and facilitates a swift recovery in the event of a security breach or system failure.
With the ever-increasing volume of data generated and stored by websites, manual backup processes are often insufficient to keep up with the pace of changes and adequately protect the information.
Automated backup solutions offer a proactive approach by scheduling regular backups at predetermined intervals, eliminating the reliance on human intervention and reducing the chances of oversight or neglect.
By automating the backup process, website owners can rest assured that their data is consistently and reliably backed up without the need for constant monitoring or manual execution.
Furthermore, automated backup solutions provide an added layer of convenience and flexibility. They allow website owners to customize backup settings to suit their specific needs, such as selecting the types of data to be backed up, specifying backup frequency, and choosing storage destinations.
This level of control ensures that critical data is backed up frequently, while less crucial information can be backed up less frequently to optimize storage space and resources.
Additionally, automated backups can be easily restored with minimal effort, minimizing downtime and allowing for a quick recovery in the event of a security breach or system failure.
This not only enhances the website’s availability but also instills confidence in both the website owner and its users, as they know that their data is secure and can be quickly recovered if needed.
Overall, implementing automated backup solutions is an essential practice for fortifying online presence, providing peace of mind, and ensuring the preservation and accessibility of valuable data.
RELATED: Creating an Effective Data Backup Strategy
Store Backups in Secure Offsite Locations
Storing backups in secure offsite locations is a prudent measure that safeguards valuable data by ensuring its availability and protection against potential threats or incidents. By keeping backups offsite, organizations can mitigate the risk of data loss due to physical damage or theft of their primary servers.
In the event of a disaster or breach, having backups stored in a separate location ensures that critical data can be easily restored, minimizing any potential downtime or disruption to business operations.
- Peace of Mind: Storing backups in secure offsite locations provides a sense of peace and reassurance. Knowing that data is replicated and stored in a separate physical location brings a level of confidence that even in the face of unforeseen circumstances, such as natural disasters or cyberattacks, critical information will remain intact.
- Compliance Requirements: Many industries have specific compliance regulations that require organizations to maintain secure and accessible backups. Storing backups offsite can help meet these requirements by providing an additional layer of protection against data loss or tampering.
- Scalability and Flexibility: Offsite backups can easily scale with an organization’s growing data needs. As data volumes increase, organizations can opt for cloud-based storage solutions that offer virtually unlimited capacity. Additionally, offsite backups offer the flexibility to access data from anywhere, enabling remote work and collaboration.
By following the best practice of storing backups in secure offsite locations, organizations can safeguard their valuable data, comply with industry regulations, and ensure the continuity of their business operations.
This approach not only provides peace of mind but also offers scalability and flexibility, empowering organizations to adapt to changing business needs while maintaining the highest level of data protection.
An estimated 12.8 million websites are infected with malware worldwide
Test and Verify the Integrity of Backups
To ensure the reliability and effectiveness of backups, it is essential to regularly test and verify their integrity. Backups serve as a critical safety net, protecting valuable data from potential loss or corruption.
However, simply storing backups in secure offsite locations is not enough; they must also be regularly tested to ensure their integrity and functionality.
Testing backups involves simulating real-world scenarios and verifying that the data can be restored successfully. By conducting regular tests, organizations can identify and address any issues or vulnerabilities in their backup systems, ensuring that data can be recovered when needed.
Regularly testing and verifying the integrity of backups not only ensures their reliability but also helps organizations maintain a sense of freedom and security. Knowing that backups are functioning properly and can be restored effectively provides peace of mind and a sense of control over one’s data.
It allows organizations to confidently navigate the digital landscape, knowing that their important information is protected and can be recovered in the event of a disaster or security breach.
Continuously Monitor and Update your Security Measures
Continuously monitoring and updating your security measures is crucial for maintaining a robust online presence and mitigating potential vulnerabilities.
In today’s rapidly evolving digital landscape, cyber threats are constantly evolving, making it essential to stay vigilant in protecting their online assets.
To emphasize the importance of continuous monitoring and updating, here are four key reasons why it is crucial for maintaining a secure online presence:
- Stay ahead of emerging threats: Cybercriminals are constantly coming up with new techniques and strategies to breach security systems. By continuously monitoring and updating security measures, individuals can identify and address any emerging threats before they can exploit vulnerabilities.
- Patch vulnerabilities promptly: Software vulnerabilities are a common entry point for attackers. Regularly updating security measures ensures that any known vulnerabilities are patched promptly, reducing the risk of unauthorized access or data breaches.
- Adapt to changing technologies: As technology advances, new security challenges arise. Continuously monitoring and updating security measures allows individuals to adapt to these changes and implement new safeguards to protect against emerging threats.
- Enhance overall security posture: By consistently monitoring and updating security measures, individuals can improve their overall security posture. This includes implementing the latest best practices, leveraging advanced security tools, and staying informed about the latest security trends and developments.
Conclusion
Fortifying your online presence through web server hardening is crucial for maintaining the security and integrity of your website.
By assessing your current security measures, updating and patching your web server, securing access, and hardening your server configuration, you can significantly reduce the risk of cyber attacks and unauthorized access.
By implementing these practices, you can enhance the security of your web server and protect your online presence from potential risks.

