Gray Box Penetration Testing: Methodology, Pros & Cons

On this page:
What is Gray Box Penetration Testing?
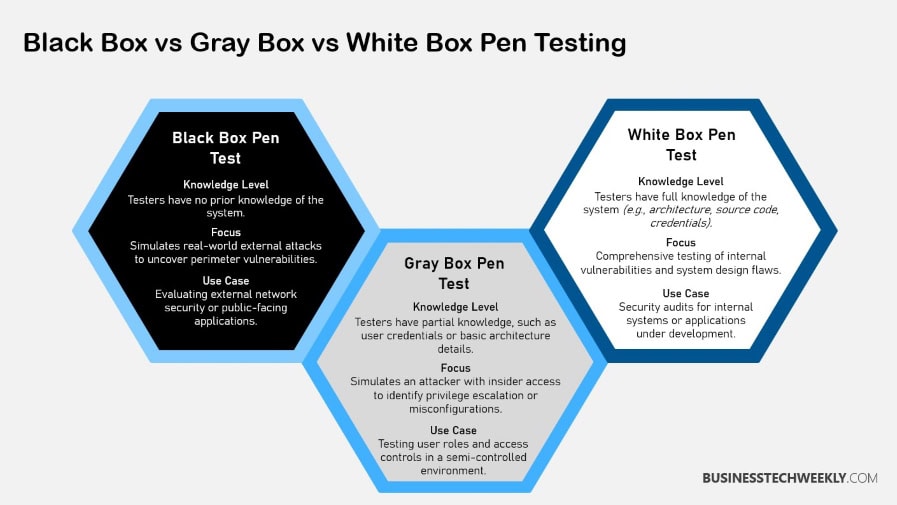
Gray box penetration testing combines the insights of white box testing, where testers have full knowledge of the system, with the exploratory approach of black box testing, where no prior knowledge is provided.
In gray box testing, you work within a controlled environment with limited knowledge about the client’s infrastructure, such as network diagrams or access credentials.
This method allows you to simulate realistic attack scenarios that both internal and external threats might pose. The balance achieved between depth and efficiency makes gray box testing a popular choice, with about 80% of organizations incorporating it into their security assessments.
Definition of Gray Box Testing
Gray box testing takes the strength of both white box and black box testing. It’s a high-octane hybrid security assessment methodology. Its primary function is to identify vulnerabilities in a system that could be exploited by cybercriminals.
Gray box testing gives testers limited insider knowledge that helps them emulate threats more accurately. It’s a very useful approach to help understand an advanced persistent threat (APT) scenario.
It allows us to read out how a technically able attacker would work over a sustained period.
By emphasizing vulnerabilities that can be exploited by both internal and external attackers, gray box testing offers a holistic view of security.
Purpose and Goals of Gray Box Testing
The goal of gray box testing is to mimic real-world attacks. It uses inside knowledge to increase the realism and effectiveness of the test.
This method increases an organization’s security by identifying weaknesses that could be exploited by attackers with limited information.
Understanding internal and external threats is very important. The training can simulate scenarios like a breach of the network by an insider or an outsider. By doing so, you can unearth valuable information about potential security gaps.
Having this knowledge allows you to create strategies that strengthen defenses against these threats.
Core Principles of Gray Box Testing
There are some foundational principles that guide the gray box testing methodologies. Testers take a balanced approach to knowledge and exploration.
They have partial knowledge of the system and are incentivized to actively look for its weaknesses.
We model realistic attack scenarios, which often include simulating insider threats or external attacks that have breached the network perimeter. This realistic approach ensures that security measures are robust and capable of withstanding sophisticated threats.
By simulating advanced threats, organizations are enabled to be ready for potential security incidents.
This proactive approach empowers their resilience to potential attacks.
How Gray Box Testing Compares to Other Types
|
Testing Type |
Knowledge Level |
Vulnerability Coverage |
Realism |
|---|---|---|---|
|
Black Box |
None |
Low |
High |
|
White Box |
Full |
High |
Low |
|
Gray Box |
Partial |
Moderate |
Medium |
Gray box testing stands out because it strikes that unique balance. It combines the unknowns of black box testing with the full transparency of white box testing.
That’s why this approach is such a favorite of many organizations — it combines practical realism with rich insights.
It’s this combination that helps them identify and uncover internal vulnerabilities. This is particularly important considering that about 34% of attacks are from insider threats.
This makes gray box testing a necessary method for accurately simulating those threats.
This testing method shines in scenarios where users have different user network permissions. It helps you identify weak spots in your system nicely.
More than 34% of companies around the globe suffer from insider threats every year
Differences from Black Box Testing
Black box testing works without any knowledge of what the system is. It only looks at the external behavior and not the internal workings. This gives an effective simulation of realistic attacks.
However, it can miss certain weaknesses, as it does not reflect the shape of the system. Gray box testing provides a comprehensive assessment.
Testers can know a bit, like an ordinary user, which makes for a middle ground approach for testers.
They can simulate external attacks while gleaning enough understanding to identify significant internal threats and minimize potential blind spots.
RELATED: Unveiling Black Box Penetration Testing
Differences from White Box Testing
White box testing gives testers complete access to the system. This makes it thorough, but it doesn’t always mimic real-world attack scenarios.
However, this approach can inundate testers with data, which can make it difficult to concentrate on actionable threats.
Gray box testing takes a semi-real-world approach, creating a middle ground between theoretical and practical evaluation. It enhances practical relevance to simulate the scenario of a tester having limited but valuable information.
This approach provides actionable insight without the exhaustive detail that is associated with white box testing.
RELATED: Unveiling White Box Penetration Testing
Comparative Advantages and Disadvantages
- Pros of Gray Box Testing:
- Strikes a balance between depth and efficiency.
- Quick and more effective than white box testing.
- Useful for simulating insider threats.
- Versatile across the web, mobile, and network infrastructure.
- Cons of Gray Box Testing:
- May not be as comprehensive as white box testing.
- Relies on seasoned testers who know both internal and external threats.
Gray box testing is economical and efficient, making it an ideal choice for organizations looking for a balanced approach. It requires skilled testers who can fuzz the system with partial knowledge.
It does have some limitations, especially in identifying outside vulnerabilities.
Nonetheless, it remains a strong choice for testing internal weaknesses and simulating insider attacks.
Steps to Conduct Gray Box Penetration Testing
1. Plan and Analyze Requirements
Before you start gray box penetration testing, you need to prepare. First, you need to scope it out and know what you want to accomplish. Think of this like mapping out a treasure hunt. You need to know what you’re looking for and why, or you could get lost.
Learn as much as you can about the client’s systems. Don’t forget to mention their apps for Android and iOS.
That process involves understanding what the application is going to look like and what the tech stack is going to look like.
This is where collaborating with the client is essential. You understand their security goals and what they’re hoping to get out of this exercise.
That will inform every step you take moving forward.
2. Conduct Discovery Phase
Let’s get into the discovery phase now. This is really more for you as a detective. This phase is really just about identifying assets and spotting potential weak spots.
You’ll have to combine a number of tools and techniques to build a profile of the target environment.
Not just networks; it also includes social engineering techniques to learn more about employees.
During this reconnaissance—sometimes called the “Recon” phase—you should come across IPs, hidden endpoints, and API endpoints.
This exhaustive sleuthing lays the groundwork for all the testing that comes next.
3. Perform Initial Exploitation
With your detective work done, it’s time to test those vulnerabilities. What you’re doing here is testing the waters on previously identified vulnerabilities to see the effect.
Along the way, record everything — every success, every failure. This documentation is important for later analysis.
You’re operating ethically here; your goal is to enhance security, not undermine it.
Do these tests while remembering the ethical guidelines.
RELATED: Understanding the Penetration Testing Lifecycle: Penetration Testing Phases & Tools
4. Execute Advanced Testing
After the initial exploits, dig deeper. This is why advanced testing techniques are commonly used to discover more sophisticated challenges.
Use a diverse set of pen testing tools to mimic sophisticated attacks. Change your approach based on what you learned in previous stages.
This may require more advanced methods for testing web apps, integration platforms, or distributed systems.
This is where the testing really happens, and it needs to be thorough and flexible.
5. Prepare Documentation and Reports
Then finish it off with thorough documentation. Make thorough reports that explain your conclusions and make recommendations.
The goal is to convey the vulnerabilities to the stakeholders in a way they can properly understand and remediate the issues.
Documentation is important; it’s not just a formality.
It actively assists clients in bolstering their security posture and stopping future breaches.
Techniques for Effective Gray Box Testing
To make sense of the various techniques in grey box penetration testing, let’s break them down into a table that categorizes each box testing technique by its specific purpose.
|
Technique |
Purpose |
|---|---|
|
Matrix Testing |
Evaluates program variables to find vulnerabilities |
|
Regression Testing |
Ensures functions work post-changes |
|
Orthogonal Array Testing |
Optimizes test cases for better coverage and efficiency |
Matrix Testing Approach
Matrix testing is like a detective with a magnifying glass, looking closely in the crevices of your program. It examines various variables to identify vulnerabilities that may be exploited.
Let’s imagine you’re examining a web app running on different platforms.
Matrix testing helps you find those specific vulnerabilities on, say, an iOS device versus an Android.
It’s organized and systematic. This test case organization allows you to quickly identify potential problems. It also highlights interactions between variables.
This insight lets you identify solutions to problems, so it’s a necessary part of your testing toolbox.
Regression Testing Method
When you update software, even minor changes can mess things up somewhere else. This is where regression testing comes in.
It verifies that everything still functions the way it should after updates or bug fixes. Consider it the safety net for your software.
It’s the best way to catch those pesky bugs that sneak in when you’re not looking.
By preserving system integrity, regression testing makes sure that you don’t simply continue to build on quicksand.
Instead, you’ve got a rock-solid foundation, protecting your software from things that go wrong.
Orthogonal Array Testing Strategy
Orthogonal Array Testing (OAT) is your go-to when dealing with software with a bunch of interacting parameters. It’s about working smart with your resources, skipping some tests and still getting the best output.
For example, if you have a system with multiple configurations, OAT helps you efficiently test input combinations.
This technique is strategic, cutting down time and cost without cutting corners. It’s especially handy when you need to balance multiple combinations to make sure all possible interactions are tested.

Benefits and Drawbacks of Gray Box Testing
When you dig deeper into gray box penetration testing, you’ll discover there are some pros and cons.
Here’s a quick look at the benefits:
- It identifies exploitable vulnerabilities in the real world.
- It is cost-effective and efficient.
- It provides a balanced approach to security by revealing hidden weaknesses.
- It is not an intrusive way to test, which expands testing coverage.
However, there are also drawbacks to consider. Gray box testing requires expert testers, which can lead to resource allocation issues.
There is a reliance on the tester’s knowledge, and there is a risk of missing vulnerabilities. Additionally, it may not be appropriate for testing algorithms.
Advantages of Using Gray Box Testing
Gray box testing is unique because it combines the benefits of black box and white box testing. This hybrid approach is non-intrusive, as it does not require full source code access, only enough to understand the algorithms.
You get a wide-angle view of the system, which helps you identify real-world issues and address them before they become major problems. Since it’s highly economical, it’s a great option for businesses that have to monitor budgets.
This approach offers the right balance, allowing you to test from both the user and developer angles. This makes it particularly effective for integration testing.
Limitations and Challenges to Consider
Despite its strengths, gray box testing isn’t without hurdles. The biggest challenge is finding skilled testers who can work to a deadline.
For this approach, you need to know the system well enough to simulate user interactions. Coordination with clients is key here because testers require specific information to conduct thorough evaluations. Without this information, there’s a risk of missing critical vulnerabilities.
Additionally, gray box testing doesn’t delve deeply into the internals of algorithms, so it may not find every flaw. While it’s great for integration and penetration testing, it’s not the best fit for detailed algorithm checks.
When to Choose Gray Box Penetration Testing
Ideal Scenarios for Gray Box Testing
- If you’re part of a company with a vast and intricate network structure, gray box testing is your ally. It doesn’t show your testers exactly how your network is laid out, and it hides some things. This makes it easier to find vulnerabilities without mapping every component.
- This approach excels in industries such as finance and health care. These sectors deal with intricate systems and are frequent targets for cyber attacks.
- In environments where security policies and infrastructure evolve rapidly, gray box testing is invaluable. If your company is rolling out new applications, you need a flexible testing approach. Frequent system updates also require a flexible approach to ensure everything still runs smoothly.
- Gray box testing flourishes in this ever-evolving landscape. It provides timely feedback that keeps up with the rapid development, so vulnerabilities are identified and patched quickly.
- If your organization operates in a sector with a high volume of cyber threats, such as e-commerce or cloud services, gray box testing helps simulate real-world attack scenarios. It’s the combination of the thoroughness of the white box test with the outsider’s perspective of the black box test.
- This balance makes it ideal for organizations that need frequent and rigorous security testing.
RELATED: Evaluating Your System’s Security with Internal Penetration Testing
Strategic Reasons for Selecting Gray Box Testing
- Gray box testing offers strategic advantages by bridging the gap between depth and efficiency. It can simulate insider threats, which are involved in about 60 percent of data breaches.
- In addition, you can also model the attacks that have already penetrated your network perimeter. An understanding of the architecture of the network allows testers to identify weaknesses.
- This approach uncovers vulnerabilities that may not have been visible during a black box test.
- This type of testing helps your organization remain vigilant against potential threats by simulating real-world attack scenarios. Gray box testing provides testers with some knowledge of your network.
- This approach helps identify vulnerabilities that advanced attackers could exploit, ensuring your defenses are robust against internal and external threats.
- By regularly engaging in gray box testing, organizations can instill a proactive security mindset. It promotes teams to become attackers in thinking toward shared security for all.
- It strengthens your defense mechanisms greatly. It also integrates your security strategies with your organizational goals, keeping you standing strong against cyber threats.
Key Points to Note
It’s time to get your hands dirty with gray box penetration testing. This method gives you a balanced view, bridging the gap between black and white box testing.
This method allows you to find bugs without having full access, so it’s the most realistic.
- Gray Box Penetration Testing is the happy medium between Black Box and White Box testing. The testers get partial knowledge of the system, enabling them to simulate an insider threat scenario.
- It’s essential to look at how Gray Box testing differs from other testing types. It combines the external perspective of Black Box testing with the detailed examination of White Box testing. This combination provides a comprehensive review of system weaknesses.
- Gray Box Penetration Testing involves a series of systematic steps. These steps include information gathering, threat modeling, vulnerability analysis, and exploitation, all of which ensure a disciplined process for revealing potential security gaps.
- To enhance the efficiency of Gray Box Testing, employ techniques such as automated scanning, manual testing, and code review. This approach enables testers to identify both general and specific vulnerabilities.
- Gray Box Testing provides a realistic internal assessment of security. It also has downsides, such as a lack of scope compared to full-access testing scenarios.
- Gray box penetration testing strikes a balance between transparency and security. It effectively counteracts both internal and external threats when you can’t talk freely about something or it’s just not economically feasible.

