IAM vs PAM: What You Need to Know About the Differences

On this page:
- What Is Identity Access Management
- What Is Privileged Access Management
- IAM vs PAM: Differences Between IAM and PAM
- Strengths and Limitations of IAM
- Strengths and Limitations of PAM
- IAM vs PAM: Deciding Between IAM and PAM
- Best Practices for Implementing IAM
- Best Practices for Implementing PAM
- Key Points to Remember
What Is Identity Access Management
Identity Access Management (IAM) is a critical user identity management tool that plays a vital role in comprehensive access management.
By governing permissions within an organization’s digital ecosystem, IAM helps protect how users access digital assets and ensures appropriate access for authorized users.
By controlling who has access, IAM significantly lowers the risks of unauthorized access to sensitive information, which is crucial given the increasing average total cost of a security breach.
The integration of IAM with different authentication methods, such as multifactor authentication and single sign-on, enhances both security and user convenience. These multifactor authentication methods effectively verify user identities, reinforcing the organization’s security posture and ensuring compliance with regulations.
As organizations adopt IAM implementation, they can leverage effective identity security strategies to manage user credentials and access risks, ultimately fortifying their defenses against potential security breaches.
RELATED: Top 5 Identity and Access Management (IAM) Best Practices
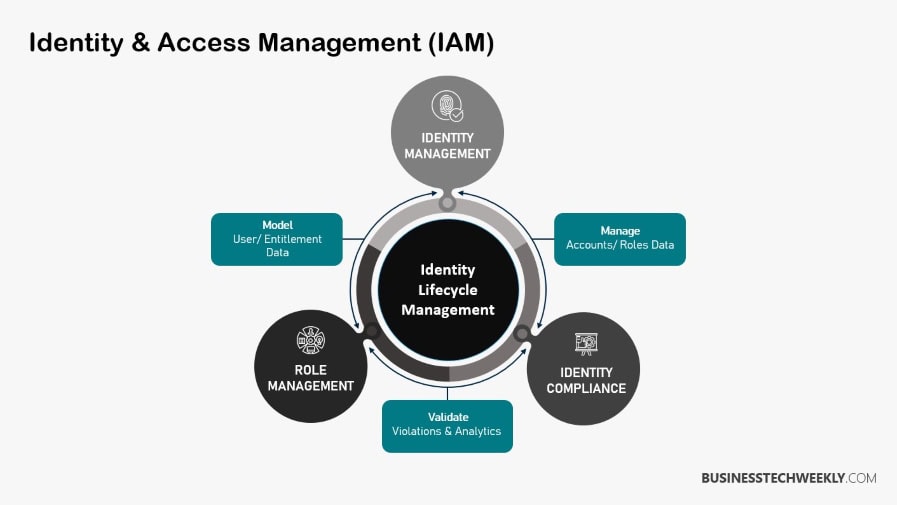
Key Elements of IAM
At its core, IAM consists of identifying who you are, authenticating that identity, and then authorizing access to resources.
Together, these elements ensure that only the right people can access the right resources.
User lifecycle management is key to sustained secure access, overseeing user statuses throughout onboarding to offboarding.
Single sign-on (SSO) makes the login process easier for users to sign in.
Multi-factor authentication (MFA) enhances security, adding an extra layer of protection for their information.
Role-based access control (RBAC) maps appropriate permissions to users’ roles, making access management easier while minimizing human error.
Benefits of Using IAM
IAM drastically minimizes the risk of data breaches by ensuring that only authorized personnel have access to sensitive information.
Automated user access management processes improve operational efficiency so IT departments can focus on other essentials.
Structured access controls enhance compliance with regulatory requirements, reducing the risk of violations.
IAM helps to make user access to necessary resources more straightforward, enabling employees to work more effectively and securely.
95% of data breaches are financially motivated. This is an increase of 24% since 2019.
Applications of IAM
IAM is particularly useful for enterprise-level user management. It automates onboarding and offboarding processes, allowing for smooth transitions and secure access.
In cloud services and SaaS integration, IAM offers uniform access control across platforms, ensuring security and user experience.
It also ensures regulatory compliance by enforcing strict access controls and maintaining detailed audit logs, enabling organizations to achieve rigorous standards.
IAM enhances user experience through convenient access features such as SSO, which simplifies authentication processes and minimizes password fatigue.
What Is Privileged Access Management
Privileged Access Management (PAM) is about watching what privileged users get up to.
Imagine a bouncer watching the superusers like a hawk. They are the ones who hold the keys to an organization’s most sensitive operations.
Because these superusers can make big changes, PAM makes sure they don’t exceed their authority.
PAM monitors and audits these actions, so you have a clear record of who did what and when. This tracking is crucial because insider threats are real and can cause serious damage.
With PAM, you minimize the chance of insiders misusing their access and keep your operations secure.
RELATED: Privileged Access Management (PAM): What is PAM & Why is it Important?
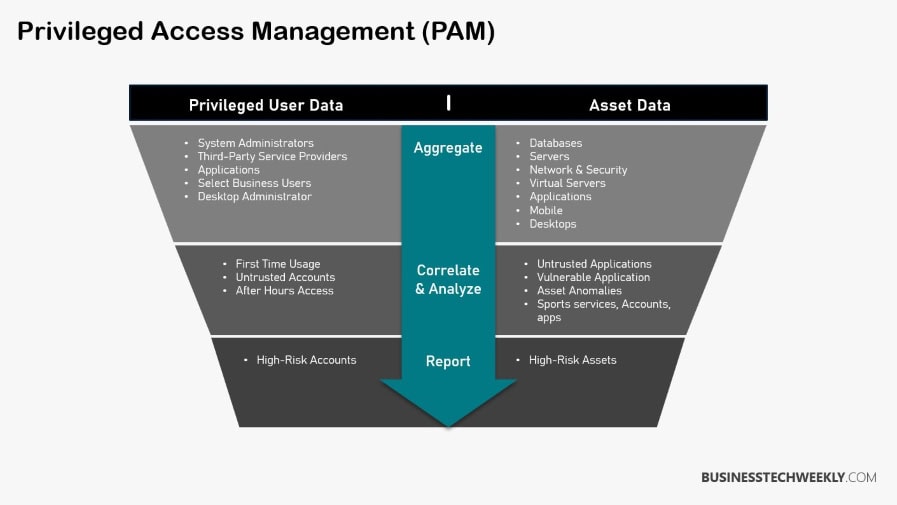
Essential Components of PAM
Privileged account discovery and credential management are key. They help you locate all those accounts with extra powers and keep their passwords locked down.
Just-in-time access provisioning means allowing access only when required. This method keeps unnecessary access in check.
Session monitoring and recording are like having a security camera — they watch every move, giving you the oversight you need.
PAM tools also excel at credential management, ensuring that only the appropriate personnel may access sensitive information.
All of these components come together to create a strong PAM system.
Advantages of PAM
PAM truly strengthens your security by keeping privileged accounts from being accessed by outsiders. It’s also a lifesaver when it comes to regulatory requirements, so you can meet those strict rules for controlling access.
By preventing insider threats and credential theft, PAM boosts your overall security. You have peace of mind knowing your sensitive data is locked up tight.
Practical Uses for PAM
Imagine securing those all-important admin accounts with PAM solutions. They prevent only authorized individuals from getting inside.
During a cyberattack, PAM limits lateral movement, which stops attackers from spreading.
It’s also critical for maintaining third-party vendor access—only letting them see what they absolutely require.
Finally, PAM ensures you adhere to stringent access rights and auditing requirements, keeping everything square.
IAM vs PAM: Differences Between IAM and PAM
1. Management Scope
Identity and Access Management (IAM) covers all user identities and access controls within an organization.
Whether it’s employees accessing company files or customers logging into a portal, IAM ensures everyone gets the right level of access to perform their tasks.
When comparing IAM vs PAM, we understand that, in contrast to IAM, Privileged Access Management (PAM) zeroes in on privileged user accounts, like system administrators or IT staff, who have access to critical infrastructure and sensitive data.
A good way to compare IAM vs PAM, is to think of IAM as the gatekeeper for general access, while PAM acts as the sentry for high-risk areas.
The unique challenges each framework addresses are crucial.
IAM is about operational efficiency, ensuring organizations manage user access effectively.
PAM, however, focuses on limiting lateral movement in cyberattacks, containing breaches before they spiral.
Implications of these scopes deeply influence security strategies, as IAM lays the groundwork for broad access, whereas PAM secures the inner sanctum.
2. Focus Areas
IAM is focused on user access management everywhere. It’s about making sure the right people get to the right resources—such as devices, applications, and network files—without putting up unnecessary walls.
PAM, however, focuses on protecting sensitive operations by superusers.
That means implementing strict policies to gatekeep critical systems and data. Both frameworks complement each other – IAM lays the groundwork for access in general, and PAM protects the secrets.
Covering both types of users is essential for true security—it’s a complete protective barrier against unauthorized access.
3. Security Tactics
IAM focuses on authentication and authorization, using tools such as passwords and role assignments to ensure identity verification.
PAM is all about credential security and continuous auditing. That means it will be diligently monitoring who accesses what and when.
Both tactics aim to reduce security risks. IAM keeps only approved users inside the club, and PAM monitors and protects their activities. These tactics are important to an effective security practice.
If you can combine this access management with credential security, then an organization’s defenses become even stronger.
4. Role-Based Access Control
Role-Based Access Control (RBAC) is a cornerstone of IAM. It defines the user roles and aligns them with appropriate permissions, thus minimizing the risks of unauthorized access.
PAM uses RBAC to control privileged users and ensures that only those with the right clearance can complete sensitive tasks.
The benefits are clear: implementing RBAC minimizes the risk of data breaches and ensures users access only what they need.
Aligning user roles with permissions helps organizations improve security overall.
RELATED: Role-Based Access Control (RBAC): What is it, and how does it work?
5. Multi-Factor Authentication
Multi-Factor Authentication (MFA) is crucial in bolstering IAM security.
By needing extra verification steps—such as biometric or one-time codes—MFA makes it much more difficult for someone to gain unauthorized access.
PAM can also leverage MFA, adding another layer of protection for privileged accounts.
Utilizing various authentication methods, such as smart cards or mobile authenticators, minimizes risks.
They easily plug into IAM and PAM frameworks and ensure that people are who they say they are, not just passwords.
RELATED: Why MFA Solutions are Critical for Cybersecurity
Strengths and Limitations of IAM
IAM Strengths Overview
When you look at Identity and Access Management (IAM), its strengths lie mainly in how it manages user identities across big organizations.
This capability makes it a breeze to handle who gets access solutions to what.
By streamlining user access management processes, IAM helps you reduce the time and effort needed to set up or change user permissions, which supports comprehensive access management strategies.
Imagine you’re running a business where employees need access to various applications and files.
IAM is your go-to solution for ensuring they can log in seamlessly without jumping through hoops.
This streamlined access doesn’t just save time; it also improves the overall user experience by providing quick and hassle-free access to necessary resources, thereby enhancing security aspects.
IAM is also a powerhouse when it comes to regulatory compliance. Enforcing strict access controls ensures that only the authorized users can access sensitive data.
This approach allows companies to satisfy important industry standards, such as GDPR or HIPAA, which are crucial for industries such as healthcare and finance.
Additionally, through minimizing the security risks of unauthorized access, IAM is critical for safeguarding sensitive data.
Recent breaches of data show that 62% involve credential misuse. It’s also important to ensure that you have solid IAM processes in place, such as identification, multifactor authentication, and authorization.
IAM Limitations Explained
Despite its many strengths, IAM isn’t without its challenges. One big problem is that you can’t keep up with changes.
This challenge is especially apparent when user roles and access needs change rapidly. Frequent employee role changes and the addition of new applications can create significant pain points, making network management much messier.
Another limitation is how IAM handles privileged access. This responsibility usually falls to the Privileged Access Management (PAM) systems, which are dedicated to securing sensitive systems.
Integrating IAM with existing IT infrastructures can also be complex, often requiring significant changes to policies and ongoing adjustments.
It can be difficult to train users to use IAM systems effectively, particularly those who are accustomed to more informal and less organized forms of access.
Furthermore, IAM does not track or monitor access once granted. While it manages user identities and controls access to devices, applications, and network files, it fails to track activities that take place after access has been granted.
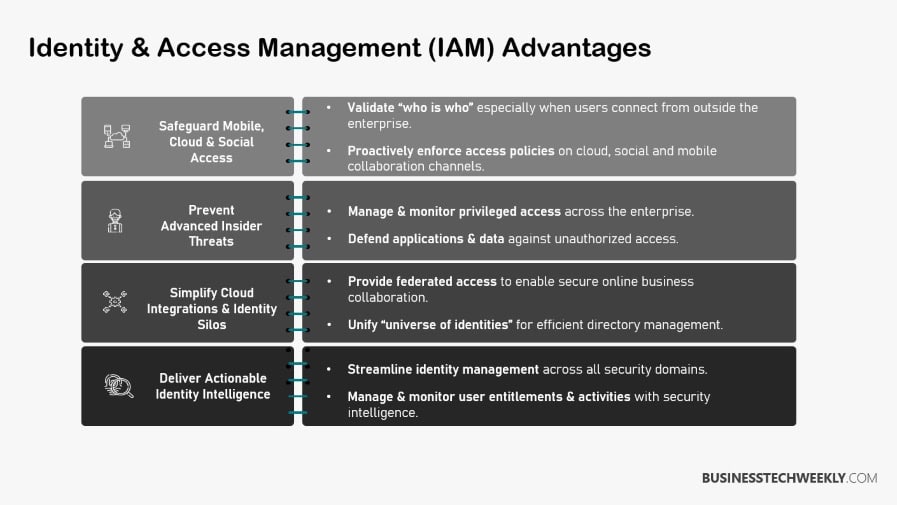
Strengths and Limitations of PAM
PAM Strengths Overview
Privileged Access Management (PAM) solidifies your organization’s security infrastructure by providing comprehensive access management solutions. It protects accounts with access to key systems and sensitive data, ensuring that only authorized users can access critical resources.
One of the biggest strengths is that it helps block access to sensitive systems from unauthorized individuals.
PAM accomplishes this by limiting access rights to only those users necessary to perform certain functions.
This is critical because limiting lateral movement during a cyberattack is essential to stanching potential breaches.
By enforcing just-in-time access, PAM makes it exponentially more difficult for bad actors to gain unauthorized access, enhancing your organization security posture.
Furthermore, detailed session monitoring increases security and enables the spotting of any bad movement throughout the network.
PAM is crucial to compliance mandates, as it enforces strict access controls, which are often required by industry regulations.
PAM actively monitors and audits privileged user activities. This continuous oversight catches any anomalies as they happen, improving your overall security.
It helps ensure that only authorized personnel can access sensitive resources, significantly reducing the risk of misuse or compromise.
Statistics show that 80% of data breaches walk in the door by leveraging privileged account credentials.
That’s what makes Privileged Access Management (PAM) an integral component of a strong security strategy. It acts as a digital insurance policy to keep your valuable items safe. By making each person use a unique login, it stops credential sharing and prevents unwanted access while fending off threats.
PAM Limitations Explained
PAM has many benefits, but it can be challenging. A significant drawback is the administrative burden of maintaining many dedicated privileged accounts.
This can become a heroic effort, particularly in massive companies with over a hundred accounts to monitor and audit.
Resistance from users to PAM policies and procedures can create challenges as well.
Many people may find the added ways to keep them secure annoying or disruptive. It’s important to balance security with practicality to ensure everything runs smoothly.
If not streamlined, PAM can create complexities in credential management.
Frequent changes in personnel or roles can create challenges in keeping access controls current.
It is vital to have a regular updating schedule for PAM systems, which means careful planning and resource allocation to prevent them from going astray.
Otherwise, newly surfaced threats won’t be handled properly, and your organization could be at risk.
The Internet Crime Complaint Center (IC3) receives 2,412 internet-related complaints every day, on average. This emphasizes the importance of maintaining PAM systems.
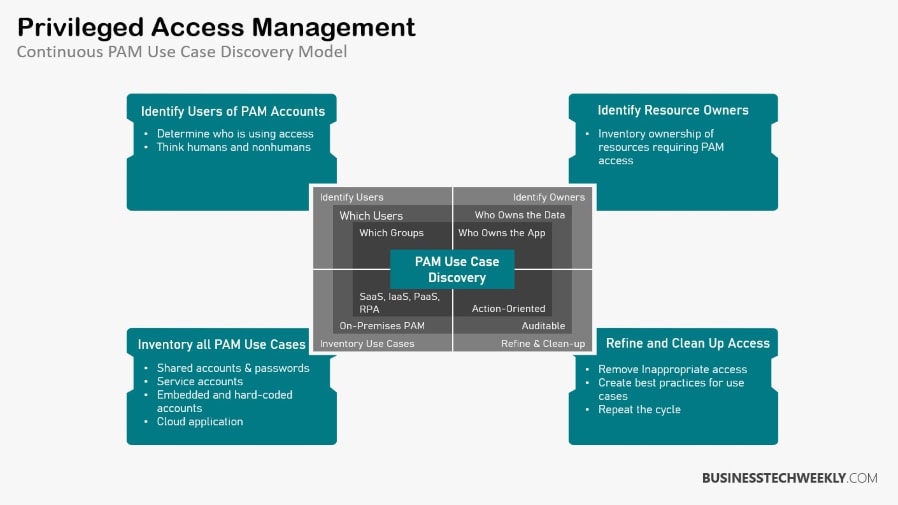
IAM vs PAM: Deciding Between IAM and PAM
Deciding between Identity Access Management (IAM) vs Privileged Access Management (PAM) is a vital decision for any organization.
It’s not just about picking a tool but understanding your specific security needs and user roles. A comprehensive access management strategy can help clarify these needs.
IAM is concerned with managing access for users. It identifies and verifies users, then assigns them rights to different applications and services.
This system is essential for organizations with varied user roles and access requirements, particularly those with regulatory compliance obligations.
When evaluating IAM vs PAM, imagine a university with students, faculty, and staff all requiring varying degrees of access to digital resources.
IAM can streamline processes such as user onboarding and offboarding, ensuring smooth transitions and consistent user management. This is crucial for maintaining appropriate access across diverse user identities.
On the other hand, PAM serves as a strong digital protection mechanism.
It focuses on protecting sensitive operations, especially in high-value asset and privileged account environments. Organizations with strict regulatory requirements, such as banks and healthcare organizations, need to prioritize limiting access to sensitive information through robust security controls.
This control is paramount for protecting their operations and maintaining compliance. PAM empowers administrators to limit user access with time restrictions.
This capability enables them to monitor activities and significantly mitigate the risk of insider threats, enhancing the overall security perspective of the organization — making PAM essential.
A key role PAM plays is managing third-party vendor access. It guarantees limited and controlled access to critical systems by external entities, ensuring that unauthorized individuals cannot gain access.
Feature |
IAM (Identity and Access Management) |
PAM (Privileged Access Management) |
| Purpose | Manages user identities and regulates access to resources across an organization. | Focuses on managing and securing privileged accounts and elevated access rights. |
| Scope | Covers all users (internal and external) and their access to systems. | Specifically manages access for users with elevated or administrative privileges. |
| Primary Function | Authentication, authorization, and user lifecycle management. | Securing, monitoring, and controlling privileged user access to sensitive systems. |
| Target Audience | General employees, contractors, and third-party users. | Administrators, superusers, and other individuals with elevated access. |
| Key Features | Single sign-on (SSO), Multi-factor authentication (MFA), User provisioning, Role-based access control (RBAC) | Privileged account discovery, session monitoring, password rotation, audit logs |
| Access Control | Provides fine-grained access control for regular user roles and permissions. | Provides tight control and oversight over high-risk accounts with elevated access. |
| Risk Mitigation | Prevents unauthorized access by enforcing policies like least privilege and strong authentication methods. | Minimizes the risk of misuse or attacks through privileged accounts by limiting access and monitoring activities. |
| Examples of Tools | Okta, Microsoft Azure Active Directory, Google Identity Platform. | CyberArk, BeyondTrust, Thycotic, Centrify. |
| Compliance Focus | Ensures compliance with regulations like GDPR, HIPAA through proper user access management. | Focuses on compliance with industry standards regarding privileged access control, such as PCI-DSS and SOX. |
| Integration | Works with various applications and services to manage user access. | Integrates with critical infrastructure to control access to sensitive systems and data. |
IAM vs PAM: Implementation
However, IAM and PAM implementation comes with its own challenges. It is crucial to align these strategies with your overall security goals.
Additionally, providing ongoing training and support for both users and administrators is necessary for effective implementation of identity governance.
Emerging security threats require that IAM and PAM strategies adapt and evolve continually to remain effective.
Rather than comparing IAM vs PAM, you could explore a unified security strategy that integrates both IAM and PAM strengthens your overall security posture, ensuring that all access risks are addressed.
This integration simplifies regulatory compliance and provides a cohesive approach to access management.
By granting and tracking access for both general and privileged users, you create an end-to-end security proposition that keeps your organization safe from both internal and external threats.
Best Practices for Implementing IAM
Implementing Identity and Access Management (IAM) effectively requires a deep understanding of your organization’s needs, current practices, and potential security gaps, particularly regarding comprehensive access management and security aspects.
To begin, here’s a list of best practices.
- Conduct a thorough needs assessment to identify gaps.
- Establish clear policies for user access and authentication.
- Utilize modern authentication techniques like MFA and SSO.
- Regularly audit and update access controls to maintain security.
Conduct Needs Assessment
Understanding where you stand is crucial. By evaluating your current access management practices, you can identify gaps that might leave your organization vulnerable.
This process should be thorough, involving input from stakeholders who can provide diverse perspectives on potential risks and needs.
By prioritizing user feedback, you ensure the IAM strategy aligns with real-world requirements and usability.
This alignment makes it more effective and less disruptive. For instance, if employees find your current systems cumbersome, their insights can guide you to choose scalable IAM solutions that integrate seamlessly with existing systems, minimizing friction.
Set Clear Policies
Sound rules are the backbone of robust IAM. When you set clear, specific policies for user access and permissions, you reduce confusion and enhance compliance.
These policies have to be dynamic, requiring routine reviews and updates to evolve with the changing landscape of user roles and security threats.
This ongoing evolution is crucial to cultivating a strong security culture.
Instead, use role-based access control (RBAC) to customize permissions based on specific job functions. This way, users only get access to what they really need, protecting against accidental breaches and vulnerabilities.
Use Modern Authentication Techniques
Advanced methods like Multi-Factor Authentication (MFA) add layers of security beyond traditional passwords.
Implementing Single Sign-On (SSO) increases security considerably while also making it easier for users by reducing the number of credentials they must manage.
Biometric authentication provides another layer, utilizing unique physical traits to confirm identity.
These modern techniques greatly reduce risks tied to passwords, which can be easily hacked. Automating these processes lightens the administrative load on IT teams, allowing them to focus on more strategic work.
Regularly Audit and Update Access Controls
Periodic access control reviews are part of a proactive approach to security.
Regular audits will expose unauthorized access and reveal security gaps, ensuring your systems stay safe. As user roles change, access permissions need to be updated timely to avoid unnecessary access.
Continuous monitoring, through native analytics tools, detects inappropriate use patterns and unexpected activity, providing an extra layer of oversight.
By implementing IAM in phases, you can handle disruptions gracefully and avoid negatively impacting users in the process.
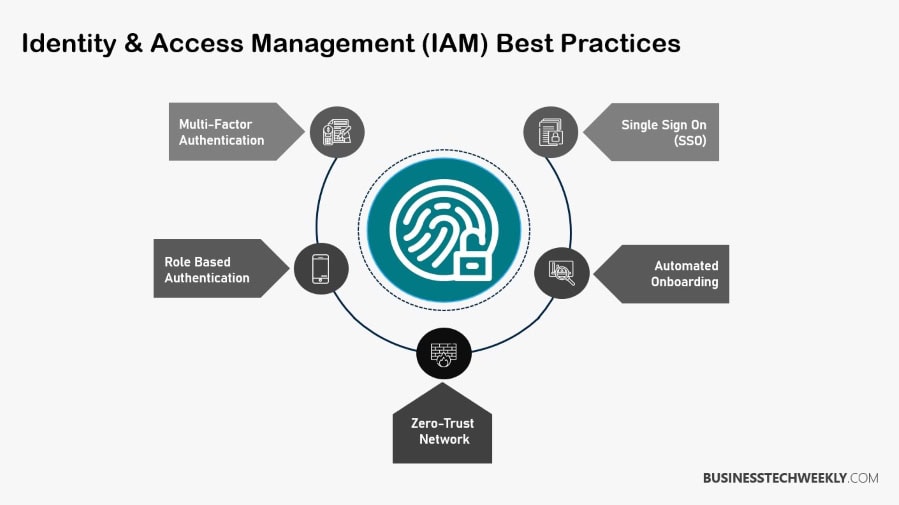
Best Practices for Implementing PAM
When it comes to Privileged Access Management (PAM), adopting the right practices is vital for ensuring comprehensive access management.
This method keeps your organization’s sensitive information safe through effective identity security strategies.
- Identify all privileged accounts requiring access to critical systems.
- Enforce the principle of least privilege for all users.
- Implement regular auditing and monitoring of privileged account activities.
- Rotate credentials frequently or consider credential-free login options.
Identify Privileged Accounts
To begin, you need to specifically identify each account that needs elevated access to key systems and data.
This step is critical because 80% of data breaches have privileged account credentials involved.
Privileged account discovery tools are a critical part of that process. They help you identify and chart out all those accounts that need extra attention.
Getting to know the various types of accounts will enhance your PAM strategies.
Adjust your approach to cater to each account’s unique needs. Maintaining an updated inventory of these accounts allows you to get a handle on access.
It also ensures you remain compliant with security policies.
Enforce Least Privilege Principle
The principle of least privilege restricts access to the absolute minimum necessary for users to perform their work.
In that way, you significantly reduce the risk of unauthorized access or data breaches.
Regularly reviewing access rights is crucial for compliance and ensures that no unnecessary permissions are given.
When applied, this principle results in a much tougher environment to penetrate, as it curtails points of failure and reduces vulnerabilities.
Regular Auditing and Monitoring
Continuous auditing of privileged account activities isn’t just a best practice—it’s a necessity.
Keeping a close watch helps you identify suspicious activity and possible hacks early.
Automated tools can definitely help with this, offering alerts and reports in real-time.
Regular audits help to meet industry regulations, ensuring that your organization adheres to all necessary legal requirements.
Rotate Credentials or Use Credential-Free Login
Frequent rotation of credentials is a simple way to reduce the scope of the risk.
Credential-free login solutions provide an alternative that lowers how often unauthorized access occurs via breached accounts.
Establish a secure process for managing credentials.
This will harden your defenses and ensure that each user has their own login, decreasing the chances of credential sharing.
Key Points to Remember
We’ve compared IAM vs PAM, and you know what IAM and PAM do, what they’re good at, and what they’re not good at.
Picking between them really depends on what you need.
IAM handles who gets in and out. PAM protects the crown jewels—your most valuable resources.
Each has its appropriate place.
Use IAM for the prerequisites for broad access. Use PAM for tighter control.
- Identity Access Management (IAM) and Privileged Access Management (PAM) are crucial for protecting an organization’s digital assets.
- When evaluating IAM vs PAM, remember IAM manages user identities and access permissions. PAM controls and monitors privileged accounts that have elevated access rights.
- Assessing IAM’s strengths and limitations, it offers comprehensive user identity management and streamlined access control. It may not provide the granular oversight needed for privilege account management.
- PAM is strong in securing privileged accounts – with detailed monitoring and auditing capabilities. It may not be that efficient at controlling regular user access throughout the organization.
- Implementing best practices for IAM and PAM involves ongoing assessment, regular updates, and ensuring compliance with security policies. Regular training and awareness programs are also essential for a strong security stance.

