What is a Security Operations Center (SOC)?

A security operations center (SOC) is a security unit dedicated to enhancing an organization’s resilience to cyber attacks.
Maintaining the CIA triad (confidentiality, integrity, and availability) of a contemporary information technology organization is vital, with cyber-attacks becoming more prevalent.
Security is becoming increasingly crucial in the information technology business. To address security concerns and provide timely reaction and resolution to security-related issues, most enterprises have established Security Operations Centers (SOC).
On this page:
What does a Security Operations Center (SOC) do?
Security operations centres, as a whole, are focused on threat detection, prevention, and repair. Their primary responsibility is to detect, analyze, respond to, report, and prevent cybersecurity risks.
RELATED: Benefits of Cyber Risk Management: What are the Advantages?
A SOC is available 24 hours a day, seven days a week, and 365 days a year. Larger companies and corporations frequently have their own SOCs that operate in-house.
The organization’s size dictates the size of the team. In organizations that require round-the-clock monitoring, the SOC will frequently work in shifts to ensure that staff members are available outside of regular office hours, however, on a reduced scale.
On the other hand, small-to-medium-sized businesses may lack the financial and technical resources necessary to maintain an in-house SOC and frequently outsource their SOC to managed service providers (MSPs).
RELATED: Finding a Technical Supplier for your Business
Security operations teams collect data from various sources, including cyber threat intelligence feeds, to evaluate, monitor, and protect assets and sensitive data.
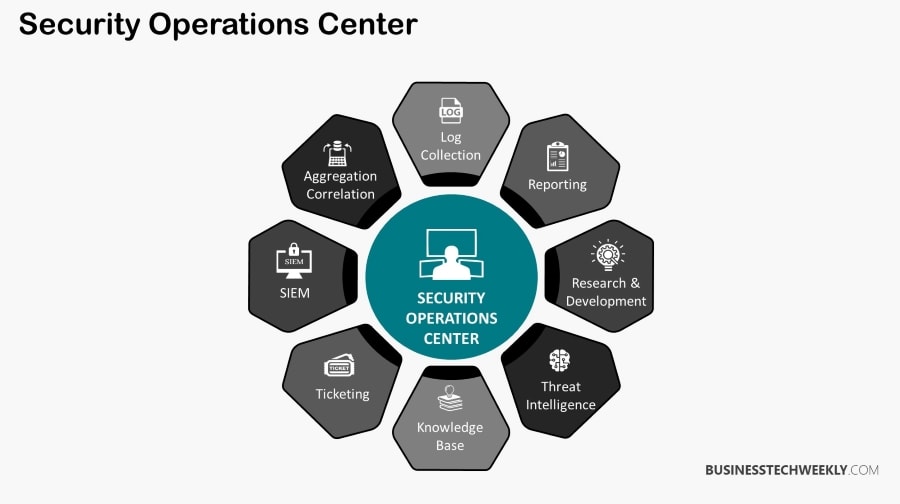
The operations centre must be adept at spotting dangers and assessing and investigating them, delivering reporting and remediation, and finally developing prevention tactics and policies to avoid similar incidents from occurring in the future. SOC teams must constantly upgrade and update existing security controls to secure firm data and information against even the most sophisticated new and zero-day threats.
Monitoring
The aspect of the SOC’s duty that frequently consumes the majority of its time is the constant, in-depth monitoring of the company’s network for any possible or developing threats. Because cyber criminals do not always work 9 to 5, and because threats might strike the network at any time, monitoring must be continuous.
Threat Response
Once an anomaly is proven malicious, the SOC will respond promptly, taking whatever steps are necessary to prevent the malicious information from propagating and causing harm. This can be accomplished by terminating malicious programmes, isolating endpoints, and removing files and data.
RELATED: Threat Management Best Practices & Common Challenges
Recovery and Remediation
After identifying and responding to emerging threats, the next most critical task is recovery and remediation in the event of an assault. Attacked systems must be restored, lost data must be retrieved, and apps, databases, and endpoints that were shut down using firebreak tactics must be reestablished. Systems will need to be modified, backups created, and affected endpoints erased and restarted.
Alert Ranking and Management
While threat detection solutions continue to improve sophistication, false positives still occur, and each event detected must be examined. False positives require the same amount of time to examine as genuine attacks.
As a result, centres must be able to prioritize the most immediate, destructive, and impactful threats first, allowing them to be mitigated before focusing on less vital security events.
A significant component of SOC’s cybersecurity approach is alert ranking and management. Alert ranking and management determine which threats are most critical, what they are targeting, and how they will damage the network, allowing SOC teams to focus on the most dangerous threats first.
Preventative Maintenance
While threat response and remediation are critical to the network’s overall security health, they are insufficient to provide complete protection against data breaches and losses. SOC teams must improve on defence as well as offence. A security operations center’s staff must stay current on all emerging threats and trends, ensuring their knowledge is as current as possible.
By being aware of these dangers, SOC teams can take proactive measures to secure the company’s network perimeter. This includes application security, system updates, firewall updates, patch management, and white- and black-listing.
Compliance Management
Regardless of their location globally, all firms must follow local government and industry regulations and recommendations. While SOCs generally adhere to best practices, they are also required to meet compliance guidelines—which are becoming increasingly stringent.
Compliance management typically comprises conducting research and learning about the requirements for protecting an organization’s data and applying such requirements within the network. GDPR, PDI-DSS, and HIPAA are standard compliance rules frequently viewed as fundamental requirements by most enterprises.
Additionally, SOC teams do an inventory of resources, root cause analysis, continuous monitoring, log management, security improvement, and security infrastructure updates.
What makes an effective Security Operations Center (SOC)?
A SOC team requires assistance from the rest of the enterprise to function effectively. This is divided into three major sections:
Personnel
A few elements are required for the operations centre to operate correctly and effectively. Which is the most critical? Personnel. A strong team is needed for an efficient SOC. Typically, this team is led by a SOC manager who reports directly to the Chief Information Security Officer (CISO).
The majority of a SOC team will comprise multiple positions, with some staff members frequently doing dual or multiple responsibilities as part of their job description.
Both junior and senior analysts compile and evaluate data from various sources but are particularly adept at following security breaches. Investigators conduct investigations into violations to determine how and why they occurred, frequently collaborating closely with incident responders.
Incident responders are the individuals who respond to a breach, implementing a variety of countermeasures to confine harmful code and safeguard data. Commonly, a single individual can perform the investigative and incident response functions.
Auditors maintain current compliance rules, ensuring that SOCs adhere to pre-existing mandates and making them aware of new ones. Threat hunters use their skill set to sift through analytics and reports in search of emerging or hidden risks. Additionally, they collaborate closely with other team members to assist in anticipating attacks.
Equipment
Security operations centres are more than a collection of highly skilled professionals. Additionally, they are a collection of modern technology and security measures. To perform their professions efficiently, a SOC requires a significant amount of cutting-edge equipment.
Among the solutions that are frequently observed (but are not limited to) in SOCs are the following:
- Security Information and Event Management (SIEM) – SIEM is a collection of software and services that enable real-time warnings and analysis of digital anomalies. It also helps SOCs with compliance by logging security data and reporting to teams. SIEM solutions collect data from several sources and frequently allow SOC teams to define “normal” system behaviour, reducing false positives.
- Intrusion Prevention Systems (IPS): Unified Threat Management (UTM) or firewalls are often used with IPS. Behind a firewall, it scans all network traffic for dangers that may have slipped past the firewall’s line of defence. It then stops malicious code and alerts SIEM protocols. Some IPS solutions can also sandbox malicious code. An intrusion prevention system (IPS) is a passive piece of software that detects and reports irregularities. Companies increasingly utilize a mix of the two or solely IPS.
- User and Entity Behavior Analytics (UEBA): UEBA is a convenient security technology centred on collecting, analyzing, and sharing user data. It’s especially beneficial for detecting and flagging account hack instances and any lateral movement or atypical user behaviour.
- Endpoint Detection and Response (EDR): As the name implies, EDR is a software solution that enables endpoint threat detection and response. It can detect, evaluate, and remediate threats, including malware, viruses, and misuse on endpoints. Once a danger is identified, the EDR solution can automatically contain and resolve it or notify the SOC team and advise remediation. System administrators can customize the level of automation used for response operations.
- Governance, Risk and Compliance (GRC) Systems: Although this is more of a framework, the phrase sometimes refers to specific software that assists in accomplishing this goal. GRC assists SOC teams in managing themselves and their operations in conformity with applicable governmental and industry laws. It essentially ensures that SOCs adhere to approved practices and assists them in managing security risks and cost reduction.
Threat Intelligence
Threat intelligence is a comprehensive, real-time, cloud-based threat intelligence solution that helps customers protect themselves against cyber threats across all vectors—file, online, message, and network.
By evaluating the propagation techniques and source of developing cyber risks, threat intelligence can help businesses protect themselves from emerging cyber dangers. It provides common threat intelligence to our security infrastructure, enabling security products to respond proactively.
RELATED: The crucial initial steps businesses must take when responding to a Ransomware Attack
Threat intelligence is required in the SOC to prevent the current threats. Certain threat intelligence providers can predict risks through data analytics before they manifest in the market. These services are in high demand since businesses do not want to jeopardize their brand. Certain threat feeds are incorporated automatically into the SIEM system, ensuring that feed updates occur instantly.
Threat Intelligence Platforms (TIP): Additionally, this solution harvests information from the network via various channels, focusing on gathering threat intelligence data. It then provides intelligence on known risks to SOC teams to aid in threat identification, investigation, response, and cleanup.
RELATED: Vulnerability Assessments: 4 Crucial Steps for Identifying Vulnerabilities in your Business
It’s particularly beneficial because it automates data gathering and management, freeing up threat analysts’ time to focus on threat analysis and investigation.
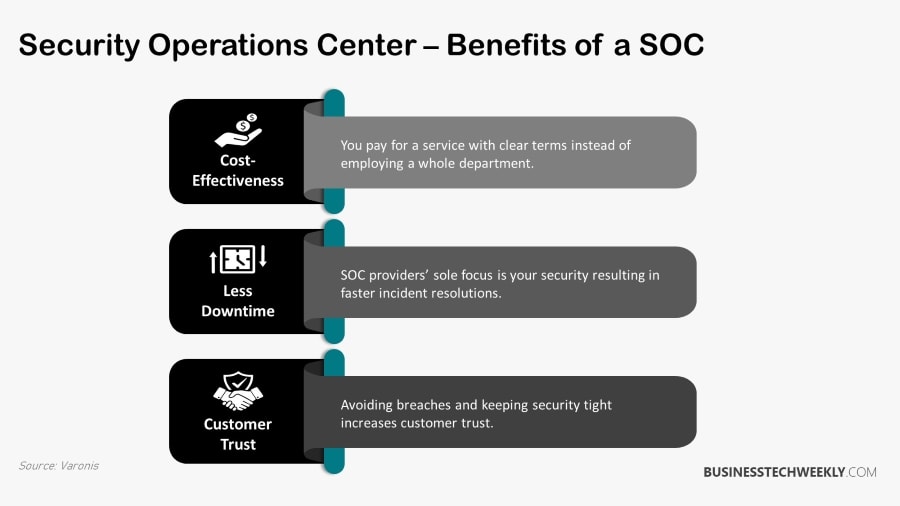
Advantages and Challenges of a SOC
There are numerous benefits of having a SOC. A managed SOC comprehensively answers a business’s security concerns by monitoring and regulating its actions. A properly configured SOC should include the following:
- Security Incident and Event Management (SIEM)
- Threat Intelligence
- 24/7 security monitoring
- Incident response
By incorporating the components mentioned above into a SOC, a company may ensure total protection. When you’re not concerned about security, performance can skyrocket. This type of implementation protects against sophisticated threats and dangers.
RELATED: Technology Risk Management
Despite monitoring and managing network-related issues affecting a business, a Network Operations Center’s (NOC) operations are distinct from those of a Security Operations Center (SOC). Personnel in the NOC are tasked with monitoring one or more networks. They should investigate and resolve network-related issues in collaboration with other responsible staff. The NOC’s key responsibilities are as follows:
- Network monitoring
- Communications management
- Reporting problems
NOC engineers may be tasked with resolving power outages, network breakdowns, and other issues. They must ensure that the network remains reliable to facilitate communication. Hardware should be appropriately configured to meet their requirements.
To provide complete security, an organization’s networks should be safeguarded. Nowadays, we can observe how the distinction between SOC and NOC is beginning to blur. Most businesses intend to merge these two hubs, resulting in significant efficiency increases.
Before deploying in a live setting, the professional should be taught in both domains. Numerous security and network management tools can be integrated to achieve optimal results. Analysts believe that while the two systems should not be linked, they should share some functions, particularly in security policy execution and auditing.
Integration of security and network operations offers numerous benefits. However, certain issues must be resolved when the two are mixed. Traditionally organized businesses establish a distinct infrastructure for monitoring security and network incidents.
This makes sense, as network operations are concerned with information on server utilization, heat concerns, and network traffic, among other things. The security team monitors security incidents on the same servers and routers.
In recent years, Security Information Management Systems (SIMS) has evolved into the technology platform around which SOCs are created. SIMs can receive security events from intrusion detection and prevention systems, firewalls, routers, and servers. With increased capability and utility comes increased complexity in implementation and cost. Several of the points are discussed below:
- Requires extensive planning
- Dedicated hardware requirements
- Technical complexity
- Identifying exact problems
- Frequent modifications according to the situation
The most challenging aspect of a successful SIM project is not deployment but post-deployment management. False alerts account for around 80% of all alerts reported. Without a comprehensive examination and inquiry, even the most technically savvy employees will be unable to determine if the alarm is fake or genuine.
Another issue that businesses are currently confronted with is the analysis of massive log files. Now, businesses rely on data analytics to sift through enormous log files and highlight the most important ones in dashboards. With the aid of big data platforms, more SIM solutions include log analysis functionality.
Summary
Security operations centres frequently focus on implementing best practices, adhering to rigorous compliance, and utilizing powerful network monitoring tools.
Many automated tools or artificial intelligence can replace a trained eye in critical situations despite this. Human analysis enables the most effective remediation of cyber dangers affecting the network and preventing future threats. This is why security operations centres are so effective.
RELATED: Information Security and Risk Management: Developing a comprehensive approach
A highly optimized, trained security operations centre is time-consuming but critical to monitoring potential security threats and defending your business against cyber-attacks. They serve as the first and last line of defence when protecting your most sensitive data and the people connected to your network—clients, customers, or workers.

