SIEM vs. SOC: What You Need to Know

SIEM collects and analyzes data from across an IT environment, while SOC involves a team that monitors and responds to threats. Both have distinct benefits.
SIEM also automates the data processing to prioritize threats in real-time. SOC also delivers the human expertise needed to respond to threats in a nuanced way.
Deciding between them really comes down to what your organization needs, what your resources are, and what your overall goals are.
On this page:
What is SIEM?
Definition of SIEM
SIEM, or Security Information and Event Management, is a core technology in the cybersecurity world. Its main value comes from its ability to collect, correlate and report on security-related activities across an organization’s entire network.
SIEM is one of the most effective ways to raise an organization’s overall security posture.
It creates a powerful bedrock to detect and mitigate threats before they happen.
This tool functions to automate all of this by automating the collection of thousands of events, aggregating this data into a centralized location. This centralization makes it possible for security analysts to quickly and efficiently sort through data, so that no critical security event is ever missed.
Organizations, particularly small and medium-sized entities, still face a lack of security resources. For them, SIEM gives them a powerful, efficient, and cost-effective way to keep their digital assets safe.
RELATED: What is SIEM? Understanding Security Incident and Event Management (SIEM)
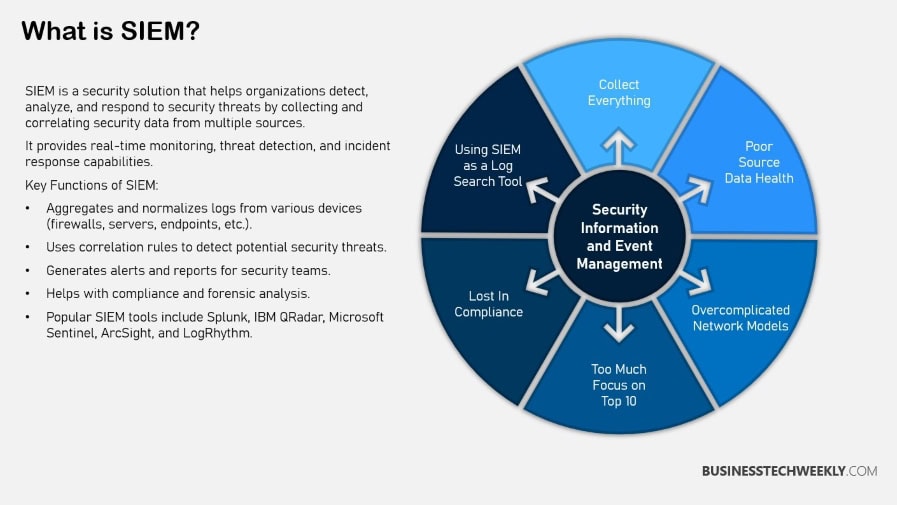
Key Features of SIEM
SIEM platforms are loaded with features that claim to make them a must-have in a Security Operations Center (SOC).
From data aggregation and normalization to threat detection, incident management, and compliance reporting, SIEM tools deliver a wide range of functionalities.
By aggregating log data from various sources, SIEM makes it easier to analyze data and even correlate events across an entire network.
Algorithms are key here, figuring out what a threat looks like by analyzing patterns and anomalies within the data. This advanced capability is key to augmenting SOC employees’ intelligence.
It enables them to quickly determine if a threat poses a risk to their network and quickly act to quarantine it. SIEM also provides advanced visualizations with clever analytics and customizable dashboards.
In addition, it features comprehensive threat hunting capabilities and forensics tools to aid in post-incident investigations.
These capabilities combine to make SIEM a critical tool for all security analysts to equip them to efficiently operate in the trenches on a daily basis.
Limitations of SIEM Solutions
However, despite all these strengths, SIEM solutions have their shortcomings. Their main sticking points being the high false positive rate and necessity of human intervention to properly contextualize alerts.
As we discussed, security teams are overwhelmed with the constant need for real-time data processing, leading to alert fatigue.
Integrating SIEM with existing security tools and processes can be complicated and take lots of time and effort. So though SIEM does a great job of log aggregation and event correlation, it isn’t able to carry out advanced asset-based vulnerability scanning.
Security analysts are right to be alarmed at the thought of missing important security events. In fact, a dismal 97% of Americans feel the same concern. To address these limitations productively, we must adopt a pragmatic and balanced approach.
That requires combining automated SIEM capabilities with expert human oversight to ensure comprehensive threat management.
What is a SOC?
Definition of SOC
SOC, short for Security Operations Center, is a dedicated team of cybersecurity professionals tasked with the critical responsibility of managing and overseeing an organization’s security operations.
Their function extends beyond mere oversight; they actively engage in incident response, ensuring that every potential threat is identified, assessed, and addressed in real-time.
The importance of SOC cannot be overstated, as it plays a pivotal role in maintaining a secure environment for organizations.
By providing a team of security experts available 24/7, SOC solutions integrate various security measures to coordinate and oversee the organization’s security efforts. Ultimately, this safeguards crucial data and business operations.
RELATED: What is a Security Operations Center (SOC)?
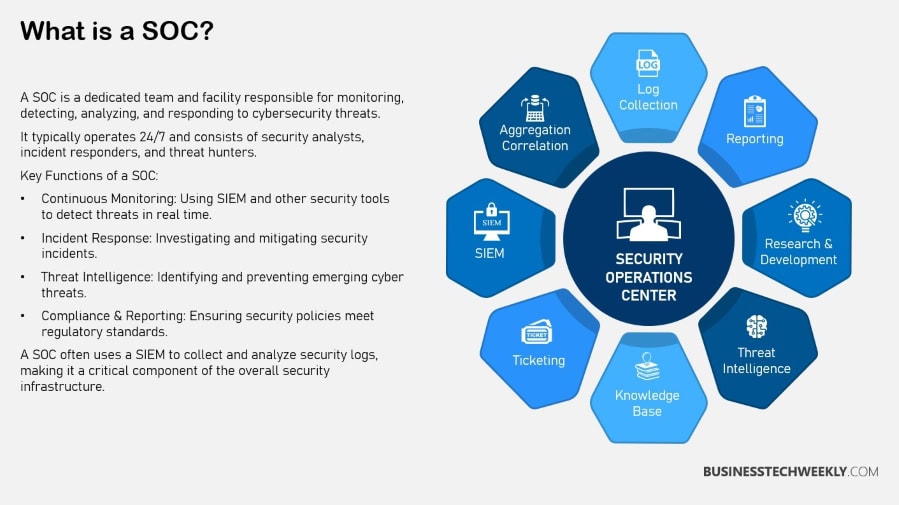
Key Features of SOC
The SOC encompasses a wide array of features designed to bolster an organization’s security posture. These include threat monitoring, incident response, threat intelligence, and forensics.
SOC teams diligently analyze security events, not just to respond to immediate threats but to prevent future attacks.
Their role extends to conducting thorough post-incident investigations, which are instrumental in improving security practices and helping the organization adapt to evolving cyber threats.
While SOC teams are resource-limited, often facing challenges in manpower, funding, and technology, their focus on data governance services, risk assessments, and security audits remains unwavering.
They are essential in network security, particularly within data centers or large enterprise environments.
Tools and Technologies in SOC
SOC teams use a broad range of tools and technologies to augment their capabilities. From Security Information and Event Management (SIEM) platforms to intrusion detection systems and threat intelligence platforms, the list is endless.
These tools are incredibly important when it comes to monitoring and analyzing malicious security events.
They provide the SOC with the contextual intelligence required to accurately prioritize, detect, and respond to threats. Automation tools are huge in enabling SOCs to accomplish more with less, but also in enabling fast, accurate threat detection and response.
SOC teams are responsible for producing the fundamental cloud security services. They are experts in incident response management and full-spectrum vulnerability management, including vulnerability scanning and patching management.
Though SOC and NOC employees are different from one another, they frequently work in tandem. They are often co-located in the same physical space to help improve security operations.
SIEM vs SOC
SIEM (Security Information and Event Management) is a technology-driven security tool that collects, analyzes, and correlates log data from various sources to detect potential threats and generate alerts.
It provides real-time monitoring, threat detection, compliance reporting, and forensic analysis, but it does not actively respond to threats.
In contrast, a SOC (Security Operations Center) is a team of security professionals responsible for monitoring, investigating, and responding to security incidents.
SOC analysts use SIEM tools, along with other security technologies, to analyze threats and take action against cyberattacks.
ssentially, SIEM is the technology that powers threat detection, while SOC is the team that manages security incidents and mitigates risks.
Organizations often integrate SIEM into a SOC to create a comprehensive cybersecurity defense system.
| Feature | SIEM (Security Information and Event Management) | SOC (Security Operations Center) |
| Definition | A security tool that collects, analyzes, and correlates log data from various sources to detect threats. | A team and facility responsible for monitoring, detecting, and responding to security threats. |
| Purpose | Provides real-time threat detection, log management, and incident reporting. | Offers continuous security monitoring, threat response, and incident mitigation. |
| Key Functions | – Log collection & correlation | – 24/7 monitoring & analysis |
| – Threat detection & alerting | – Incident investigation & response | |
| – Compliance reporting | – Threat intelligence & hunting | |
| – Forensic analysis | – Security policy enforcement | |
| Human Involvement | Minimal human interaction once configured; mostly automated processes for alerts & reports. | Requires high human involvement, with security analysts and engineers responding to threats. |
| Threat Detection | Uses AI, rules, and machine learning to detect patterns and anomalies. | Uses manual analysis, intelligence gathering, and automated tools to investigate threats. |
| Incident Response | Generates alerts but does not respond to threats. Requires human intervention or SOC integration. | Takes active measures to investigate and mitigate threats. |
| Use Case | Organizations looking for a log management and automated alerting system. | Businesses needing proactive threat response and security operations management. |
| Dependency | Can function independently, but works best when integrated into a SOC. | Often uses SIEM tools for log analysis and threat detection. |
| Examples | Splunk, IBM QRadar, Microsoft Sentinel, ArcSight, LogRhythm | In-house SOC teams, Managed Security Service Providers (MSSPs), or third-party SOC-as-a-Service providers. |
How SIEM Supports SOC Processes
In a Security Operations Center (SOC), integrating Security Information and Event Management (SIEM) data into workflows significantly enhances threat detection capabilities.
SIEM systems gather data from various sources, analyzing and aggregating it into a centralized location. This enables SOC teams to sift through potentially thousands of events, distinguishing between genuine threats and false positives.
The ability to quickly identify and assess threats is vital, as unmonitored environments can lead to breaches.
For instance, a SIEM system that effectively manages alerts can prevent analysts from becoming overwhelmed and apathetic, ensuring they remain vigilant and responsive.
Satisfaction levels with current SIEM solutions vary. The average satisfaction score ranges from 7.6 to 8.5 out of 10, indicating that while many organizations find their SIEM solutions adequate, there is room for improvement.
1. Event Classification Process
The security event triage process utilizing SIEM data is a regimented and organized flow.
SOC analysts will triage incoming events to classify them by severity level and potential impact, identifying which incidents require escalation and urgent action.
This classification is key to an effective incident response, as it helps focus resources on the most urgent threats first. By classifying with precision, SOC teams can address threats before they become serious, providing a strong line of security defense.
2. Prioritization and Investigation
Alert prioritization is a fundamental step in SOC operations, and risk assessment is central to this process. SOC teams focus on high-priority incidents, investigating them thoroughly to ensure timely resolutions.
Collaboration between SIEM and SOC enhances this phase, providing real-time data that informs decision-making.
A centralized SIEM platform improves incident response times, making it a cornerstone of efficient SOC operations.
3. Containment and Recovery Steps
Once a threat is detected, SOC teams need to respond quickly to contain it. This can include isolating impacted systems and taking action so that the threat can’t propagate.
Recovery actions come next, with the goal of returning their operations to normal and fixing any impacts caused by the incident. A well-defined containment strategy becomes even more important.
This minimizes downtime and prevents business disruptions, keeping the organization ready to weather even the most significant future threats.
4. Remediation and Mitigation Actions
Remediation is the process of patching vulnerabilities that are revealed during the incident response process. SOC teams go through great lengths to identify and remediate these vulnerabilities, ensuring they don’t happen again.
Implementing those mitigation strategies matters just as much, too, because it strengthens your defenses against that same threat. It goes without saying, the SOC is in many cases the engine that powers ongoing security enhancements.
It prepares the organization’s defenses to keep pace with the threat landscape.
5. Assessment and Audit Procedures
Continual measures such as security audits assist in measuring what works versus what doesn’t. Audits not only ensure compliance with established security policies, but they also provide an additional layer of scrutiny.
Evaluations are an integral part of keeping your organization’s security posture healthy. They find weaknesses and gaps and buttress them with best practice.
Ongoing evaluations help to make sure that the SOC is always moving forward—staying flexible and ready to meet new dangers as they arise.
Advantages of Using SIEM
Here are plenty of benefits that SIEM systems can provide to your organization’s cybersecurity posture. One of the biggest advantages is the improved threat detection and faster incident response.
With SIEM solutions, you can automate threat detection across your entire network, detecting and alerting on potential threats so you can respond in minutes instead of hours.
This visibility is especially important given today’s dynamic cybersecurity landscape.
Particularly in our hybrid work world, the speed of your response can make all the difference in whether a small incident turns into a serious breach. SIEM solutions give you the tools that let you immediately understand your log and threat intelligence data, providing an overall picture of your network’s security health.
In addition, SIEM systems play a big role in enhanced compliance and reporting processes. These solutions also automate report generation to help keep your organization compliant with regulatory bodies.
This saves your organization and your managed security service provider customers time and money while ensuring they avoid any potential violations.
SIEM tools offer powerful reporting features that allow you to maintain a detailed history of security incidents and your response to them. This can be particularly important for audits or regulatory reviews.
The cost-effectiveness of putting SIEM solutions in place is another important benefit. Traditional SIEM platforms can take weeks or even months to deploy.
By comparison, cloud-based SIEM solutions can be provisioned and operationalized in a matter of hours.
With all of that in mind, this fast deployment also accelerates your time to security. You can start actively defending your organization in minutes, avoiding the months of configuration associated with legacy solutions.
In fact, the SIEM industry is poised to grow by nearly 25% in the next five years.
This trend reflects the increasing demand for automation in cybersecurity and emphasizes the need to invest in robust cybersecurity strategies.
Benefits of SIEM Systems
Centralized log management and real-time alerting are two of the main advantages of SIEM systems. SIEM solutions ingest and normalize logs from multiple different tools across your IT ecosystem.
This centralization helps you to simplify and streamline your ability to analyze this data and take action.
Centralization also increases your visibility into security events occurring across your entire network. This provides you with a better understanding of your complete security posture.
With real-time alerting, you’ll be able to respond to security incidents in the moment, taking proactive measures before threats ever have a chance to escalate.
Proactive security SIEM systems also help support proactive security measures by providing insight into where your security posture is most vulnerable and under attack. You’re able to detect anomalous user behavior real-time.
In this manner, you can rapidly identify any irregular behavior, such as unusual access attempts or suspicious data movement. This proactive approach makes it easier to detect insider threats.
Beyond that, it increases your security posture by stopping breaches before they occur.
Effective Use of SIEM in SOC
In order for SIEM to be effective as part of a Security Operations Center (SOC), integration strategies are critical. Adding SIEM to SOC operations takes thoughtful planning and implementation.
Ensure that the SIEM tools you choose will integrate well with your current systems and processes.
Training SOC personnel to use SIEM tools effectively is just as critical. Having skilled personnel to fully leverage your SIEM solution’s capabilities can further boost the effectiveness of your security operations.
Creating these feedback loops between SOC personnel and SIEM technology have a profound impact on performance.
Consistent feedback allows you to continuously improve SIEM processes, tuning them to the ever-evolving threat landscape, and your organization’s specific needs.
This iterative process of continuous improvement means your security measures are always effective and up-to-date, offering strong protection against the latest threats.
A significant number of SOC teams receive over 1,000 security alerts daily. Specifically, 61.37% of teams report handling more than 1,000 alerts per day, with 4.29% facing over 100,000 alerts daily.
Continuous Monitoring with SIEM
Continuous threat detection is key to staying one step ahead of attacks—in this respect, SIEM systems are the best in class. SIEM solutions allow businesses to analyze security events in real-time.
This helps you achieve a more proactive security posture, so you’re catching and mitigating threats before they become a serious issue.
This immediate responsiveness is key to preventing and mitigating the effects of security incidents and protecting valuable sensitive information.
The importance of SIEM in ensuring an overall strong security posture is critical.
By continuously monitoring network activities and analyzing security events, SIEM systems help you stay ahead of potential threats, providing the necessary insights to make informed security decisions.
Taking a more proactive stance protects your organization.
It’s peace-of-mind for your stakeholders as well, who can rest assured that their data is protected with state-of-the-art security technology.
Differences Between SIEM and SOC
Critical Differences Explained
To better appreciate the differences between Security Information and Event Management (SIEM) and Security Operations Centers (SOC), consider how each one operates.
Each is needed to build and improve our overall cybersecurity defense.
SIEM should be used as a strong tool for collecting and analyzing data. It brings together data from across your environment to identify and predict potential threats.
It is an important component in providing an overall picture of security events.
By aggregating and correlating data from various sources, including detailed logs, it assists in recognizing patterns that can suggest potential security threats.
SIEM systems are designed to help monitor and detect APTs. Eliminating these threats entirely is often difficult to do.
The SOC works like a well-oiled machine.
Not only do they concentrate on incident response, but they also work to improve the organization’s security posture on an ongoing basis.
This team leverages advanced technology and standardized processes to proactively prevent, detect, analyze, and respond to incidents. The SOC’s role is central to making sure an organization is capable of moving quickly and confidently to mitigate a risk before it’s exploited.
In addition, reducing total cost of ownership becomes a reality for 80% of organizations that outsource their SOC functions.
This speaks to the tactical importance that keeping an internal response team can have at a strategic level.
Data Collection and Analysis in SIEM
SIEM systems collect information from millions of devices such as network devices, servers, and applications. This data aggregation is essential in developing a complete security picture.
By analyzing logs, SIEM systems can pinpoint unusual activities or patterns that indicate security threats, aiding in the early detection of potential breaches.
The capacity to rapidly analyze and interpret this data is critical to improving security efforts.
For example, if SIEM detects a new device on the network, it sends an alert to the SOC, which can decide how to respond.
Incident Response Capabilities
SOC’s incident response capabilities are different than SIEM’s analytical function. Whereas SIEM simply detects the threat that could be present, SOC takes direct action to eliminate the threat.
At the very least, it should involve extensive containment and mitigation strategies to reduce the impact of breaches. Having a dedicated SOC team allows for timely and efficient management of security incidents.
A completely unified solution has SIEM and SOC capabilities natively integrated into a single solution.
This integration minimizes miscommunication and enhances the effectiveness of the security response.
|
Aspect |
SIEM |
SOC |
|---|---|---|
|
Nature of Functions |
Data analysis and threat detection |
Incident response and monitoring |
|
Role in Threat Detection |
Provides log analysis and alerts |
Responds to threats identified |
|
Scope of Responsibility |
Monitors and identifies threats |
Manages and mitigates threats |
|
Response Capabilities |
Alerts on potential threats |
Direct action to neutralize threats |
Choosing Between SIEM and SOC
First, consider the different variables at play that will affect your decision regarding cybersecurity strategies.
From there, figure out if a Security Information and Event Management (SIEM) system or a managed SOC solution will serve you better for effective cybersecurity. These decisions usually depend on unique organizational factors and requirements.
Factors to Consider for Organizations
Larger organizations may require the robust capabilities of a SOC, while smaller entities might benefit from the streamlined processes of a SIEM.
Sectors with stringent compliance requirements, like finance and healthcare, need to ensure their security solutions align with these standards.
Understanding the types of threats your organization faces is crucial. It’s no secret that complex and advanced threats are some of the hardest to remove, requiring more advanced technology to combat.
However, most organizations do not have the internal talent or expertise to run a Security Operations Center (SOC).
Good outsourcing addresses those miscommunications, while also folding in best security practices.
Finding the right balance is important to match security solutions with broader organizational goals to strategically reduce risks while improving operational efficiency.
When to Choose SIEM
Implementing a SIEM is incredibly beneficial for centralized log management and advanced threat detection.
Additionally, 80 percent of organizations use a SIEM system as a central hub to help monitor and analyze their security data.
That rampant usage is key for improving compliance efforts, especially for heavily regulated industries. SIEM tools can only analyze that data and send alerts to SOC teams, but managing false positives is still a big problem.
When to Opt for SOC
A SOC is most advantageous for businesses that need around-the-clock monitoring and rapid, 24/7 incident response. It offers a holistic security approach, particularly in dynamic environments.
A SOC team, made up of security analysts, engineers, and managers, enables rapid detection and effective remediation of security incidents.
Bringing SOC expertise together with SIEM capabilities, however, usually provides the best outcomes.
Points to Consider
Once you dive into SIEM and SOC, you quickly realize how they’re intertwined with the greater security ecosystem.
SIEM provides you the capabilities to collect and analyze data, helping you identify where you have potential issues. SOC proactively manages and mitigates threats, ensuring your systems are safe and your business stays up and running.
Both enable you to secure your data and react to breaches quickly.
- SIEM, or Security Information and Event Management, is an incredible tool. It centrally monitors and analyzes security data from all of an organization’s networks, significantly enhancing organizations’ threat detection and incident response capabilities.
- SOC (Security Operations Center) entails a skilled team dedicated to continuously monitoring cybersecurity operations, proactively identifying and responding to threats to maintain a secure organizational environment.
- To get the most out of SIEM solutions as part of your wider security architecture, it’s important to know what they do well and where they fall short. Consider issues such as data correlation, advanced threat detection, the burden of false positives.
- SIEM is a highly technical technology. SIEM collects and analyzes data to produce alerts that inform SOC’s incident response priorities and strategies to maximize efficiency in threat mitigation and improve overall security posture.
- Organizations should carefully consider factors like budget, infrastructure, and specific security needs when deciding between deploying SIEM or establishing a SOC, ensuring alignment with their unique operational goals.
- Leveraging SIEM also provides benefits such as better compliance and faster incident response. When used in tandem with the proactive strategies of a SOC, organizations can significantly improve their cybersecurity defense.
- Security Information & Event Management (SIEM) and Security Operations Center (SOC) has become crucial in cybersecurity today.

