Cyber Security as a Service (CSaaS): Everything you need to Know

Cyber Security as a Service (CSaaS) provides enterprise-class security for small and mid-sized businesses (SMBs) without the complexity. It bundles a variety of services, such as threat monitoring and data protection, into one convenient package.
As threats such as ransomware continue to grow, CSaaS ensures that you remain protected and secure – no matter what.
What you gain is peace of mind; you no longer worry about your data being compromised and your daily business operations being disrupted.
On this page:
What is Cyber Security as a Service (CSaaS)?
1. Definition of CSaaS
Cyber Security as a Service (CSaaS) is a model through which companies can outsource their cybersecurity requirements to third-party providers. This service enables organizations to outsource their cybersecurity operations without having to invest in an internal security team.
With CSaaS, organizations have access to a more comprehensive suite of outsourced security offerings. These range from antivirus management, intrusion detection, to even real-time threat monitoring.
This delivery model is especially advantageous because it uses specialized teams of cybersecurity experts focused on proactive breach prevention. They take care of protecting organizations—so organizations can get back to what they do best.
2. Core Components of CSaaS
A strong CSaaS service offering contains three critical elements.
These are complex technologies and tools that are used to monitor, prevent and manage threats.
Key components Cybersecurity as a service often includes continuous monitoring and threat intelligence, both of which play an important role in keeping your organization secure.
CSaaS platforms combine these technologies together seamlessly to provide a holistic solution to your security needs. This guarantees that organizations can take a proactive approach in addressing potential threats.
The scalability of CSaaS allows businesses to adjust their security measures as needed, making it a flexible and adaptive solution.
3. Importance of CSaaS Today
Cyber threats are on the rise. CSaaS systematically tackles these challenges by offering specialized services, developed to meet the speed of innovation.
By outsourcing cybersecurity through a Cybersecurity as a Service model, organizations gain access to a wealth of expertise and 24/7 monitoring.
This model ensures a more proactive organization in terms of security posture, while also providing a more budget-friendly solution.
Business leaders like this approach because it helps move the security needle in a positive direction at a lower cost.
As cyber threats are becoming more and more sophisticated, CSaaS allows organizations to focus on their core business while protecting their digital assets and securing their future.

How Cybersecurity as a Service Works
1. Operational Mechanisms of CSaaS
Cyber Security as a Service (CSaaS) operates under a straightforward framework that emphasizes providing a robust cybersecurity solution. At its core, CSaaS offers organizations around-the-clock monitoring and response to potential security threats.
In contrast, managed security companies can often begin monitoring an organization’s environment within just a few days or weeks, ensuring a swift and effective cybersecurity posture.
This seamless deployment is facilitated by a dedicated Security Operations Center (SOC) that leverages advanced security features powered by technology and human intelligence.
To quickly identify cyber attacks, the SOC employs network and endpoint monitoring, behavioral analysis, machine learning tools, and threat intelligence. The integration of automation and artificial intelligence has become essential in detecting a wider range of risks as they emerge.
They also ensure that real-time monitoring and incident response capabilities are always on 24/7. Our clients get alerts via phone call or email as soon as an infection or attack is detected so we can take action right away.
This methodical process helps organizations proactively protect against emerging threats with the least amount of disruption.
RELATED: What is a Security Operations Center (SOC)?
2. Key Features of Service Providers
When choosing a cybersecurity platform, organizations should prioritize flexibility, scalability, and strong reporting capabilities as essential features.
Companies benefit from a pay-as-you-go model, allowing them to scale services quickly to adapt to their evolving needs, making CSaaS a more economical option. This flexibility ensures that organizations can leverage cybersecurity solutions effectively, only paying for what they use.
Providers deliver an integrated interface encompassing email security, cloud security, network security, and endpoint security, which collectively form a unified platform of protection. This combined approach enhances management efficiency and strengthens security operations.
Robust reporting and analytics are vital, offering clear visibility into potential security threats, malware, and vulnerabilities. These reports also provide pragmatic guidance to help organizations improve their cybersecurity posture.
Additionally, they assist organizations with compliance, ultimately increasing their overall security stance against cyber attacks.
3. Role of Managed Detection and Response
Managed detection and response (MDR) is a key feature under the umbrella of CSaaS that improves threat visibility and incident response speed.
MDR services include 24/7 monitoring and rapid detection of security incidents, so your organization can respond to threats sooner and prevent them from becoming major incidents.
Because of the proactive approach of MDR, security measures are working long before threats have a chance to become serious. By addressing both detection and response, MDR enables organizations to better defend against cyber threats.
This multifaceted approach involves scanning policy settings, as well as providing actionable recommendations for enhancing security practices.
This growing trend further highlights the model’s increasing importance in today’s cyber environment.
Types of Cybersecurity Services
1. Overview of Managed Security Services
Managed Security Services (MSS) are the bedrock upon which Cyber Security as a Service (CSaaS) are built. They ensure never-ending security for organizations by outsourcing security management to cloud-based security providers.
With MSS, you get access to a 24/7 team of cybersecurity experts who proactively manage threat hunting, alert monitoring, and incident response. These services are more cost-effective and allow for flexibility.
They’re ideal for companies that need to incrementally increase their security posture without overburdening their in-house talent. MSS’s holistic, full stack approach protects against a variety of threats, from cyber attacks specifically aimed at SMBs to sophisticated, enterprise-level intrusions.
2. Security Information and Event Management
Security Information and Event Management (SIEM) plays an important role in CSaaS. It provides a single pane of glass that brings key security data and analysis together.
With SIEM solutions, you receive critical analysis and insights into security events, allowing you to identify threats before they become an issue. Real-time alerts and reporting capabilities are key features, which enable the fastest incident management and response possible.
SIEM also improves your organization’s operational efficiency and your overall security strategy by integrating seamlessly with existing systems.
RELATED: What is SIEM? Understanding Security Incident and Event Management (SIEM)
3. Identity and Access Management
Security Identity and Access Management (IAM) plays a crucial role in protecting sensitive data by managing who has access to what. IAM solutions bring together capabilities such as Single Sign-On and Multi-Factor Authentication to provide easy access without sacrificing security.
When you implement Role-Based Access Control, you eliminate a lot of manual processes and the risk of insider threats or unauthorized access.
IAM guarantees that only the right users can access sensitive data, strengthening your organization’s security against leaks and breaches.
4. Essentials of Endpoint Protection
In a CSaaS model, endpoint protection is foundational, as it helps protect all devices that connect to your network. Antivirus software, threat detection services, and other essential components work in tandem to recognize and eliminate threats before they can do damage.
For example, CSaaS providers can install Endpoint Detection and Response (EDR) systems in record time, with the guarantee of full deployment across tens of thousands of endpoints.
This unique ability to deploy at high speed increases the overall security of your network and delivers strong protection from malware and other harmful actions.

Implementing Cyber Security as a Service
1. Assessing Organizational Security Needs
To implement Cyber Security as a Service (CSaaS) effectively, you first need to assess your organization’s security needs. This involves identifying key factors such as the size of your organization, the sensitivity of the data handled, and the specific regulatory requirements you must meet.
Understanding the threat landscape specific to your industry is crucial. For example, healthcare organizations face different threats compared to financial institutions.
Conducting a thorough risk assessment helps in identifying vulnerabilities and determining the appropriate security measures to protect against potential breaches.
This step is foundational in setting up a robust CSaaS framework.
2. Selecting the Right Provider
Finding the right CSaaS provider is an important first step. Shortlist and vet potential providers to gauge their market reputation, expertise, and breadth of services. A reputable provider will have a proven track record across their service in cybersecurity.
They can also provide reassurance that your organization’s data is protected by experts.
Above all else, transparency and clear communication are key. By setting a common goal with the provider, you guarantee that they have a concrete understanding of your needs and business goals.
Look for providers that are able to prove their capacity to deliver continuous security monitoring and response.
This unique capability provides CSaaS with a notable advantage.
3. Developing an Implementation Strategy
Crafting a detailed implementation plan will be key to successfully rolling out CSaaS. Any national strategy should involve concrete measurable goals and timelines to measure progress.
It’s critical to remain nimble and willing to pivot the approach as new needs and challenges emerge. Continuous evaluation helps you focus your efforts, so you can better protect your organization while threats are constantly changing and becoming more sophisticated.
A solid strategy delivers by ensuring that security solutions can easily scale to meet security needs as organizations grow.
4. Executing the Implementation Plan
Once your strategy is established, implementing the implementation plan requires several important steps. Training your staff and other stakeholders on new security protocols helps everyone understand their new role in cybersecurity.
Rigorous testing and validation of security systems is required to ensure that they work the way they’re supposed to. During this act, we leverage a proven combination of network and endpoint detection, behavioral analysis, and threat intel.
Using this approach, we are able to identify threats faster and reduce our response times significantly.
5. Continuous Monitoring Approaches
Continuous monitoring is indispensable to staying ahead in the fight against cyberattackers and ensuring resilient cybersecurity protections. Use a combination of machine learning technologies and curated threat intelligence to maintain round-the-clock vigilance over your systems.
This method also allows for fast incident response and remediation, preventing further damage from any possible breaches.
With cyber security as a service, organizations can leverage a real-time, 24/7 monitoring system that allows them to address threats as they occur. Security specialists leverage their expertise to proactively hunt for potential risks.
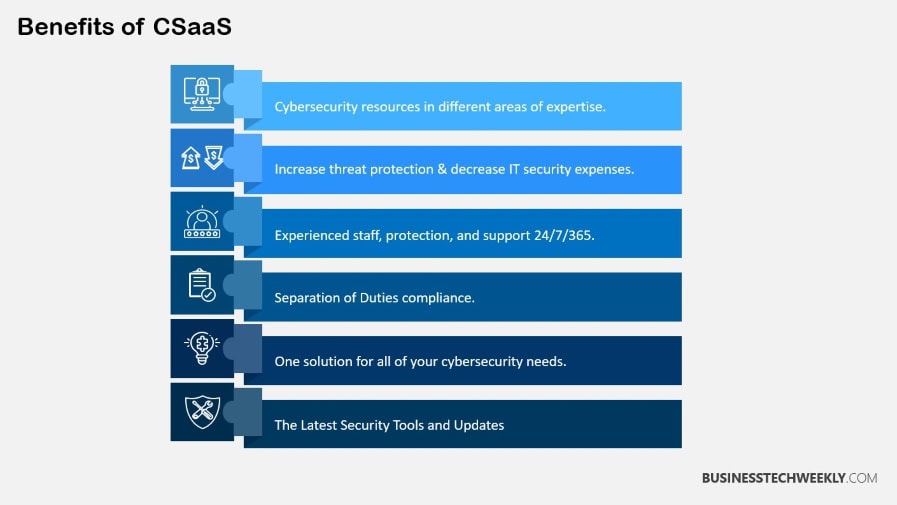
Benefits of Cyber Security as a Service
That’s why adopting Cyber Security as a Service (CSaaS) provides organizations with a host of powerful benefits.
Most importantly, it improves an organization’s overall security posture by offering ongoing, 24/7 monitoring of the ever-changing cyber threat landscape. You get round-the-clock, 365-day-a-year responses, 24/7.
By keeping these eyes always on, businesses are able to quickly adapt to new vulnerabilities, reducing the risk of costly disruptions and increasing overall business productivity.
In addition, the complete network visibility, along with instant notifications, enables organizations to strengthen their security postures with confidence.
1. Cost-Effectiveness for Businesses
Cyber Security as a Service (CSaaS) is the solution businesses need to save money on cybersecurity.
By completely outsourcing their security needs, they also sidestep the significant one-time investments typically necessary for in-house solutions. This model also offers clear financial benefits.
Plus, it relies on a predictable subscription pricing model, allowing you to budget and plan your finances with greater accuracy. CSaaS also provides organizations with access to the latest security technologies as well as the expertise of trained professionals.
This cost-effective solution enables companies to save tens of thousands of dollars as opposed to having an in-house staff.
2. Scalability and Flexibility
Since CSaaS solutions are intrinsically scalable, organizations will find it simple to scale up or down, depending on how their security requirements change over time.
That flexibility is important to allow for more development and business growth without the added costs of big new infrastructure investments.
Businesses can rapidly scale up or down their offerings based on needs. This flexibility gives them the ability to pay only for what they need, when they need it.
CSaaS is flexible and can scale with an organization, making it an attractive solution for enterprises and small and medium-sized businesses (SMBs) alike.
It’s a low-cost solution that grows and changes with your organization.
3. Access to Expertise and Technology
One of the biggest advantages of CSaaS is the on-demand, 24/7 access it gives organizations to specialized cybersecurity expertise.
Organizations get access to the latest technologies and tools without having to constantly train an in-house team.
This access to advanced threat intelligence, machine learning tools, and behavioral analysis technologies enables businesses to stay ahead of emerging cyber threats.
CSaaS providers also bring ongoing professional development. This ensures that security specialists stay at the cutting edge of the quickly evolving cybersecurity landscape.
4. Round-the-Clock Security Assurance
CSaaS offers companies 24/7 cybersecurity protection.
This helps guarantee the earliest possible threat detection, allowing for rapid response to emerging threats. 24/7 monitoring for worry-free security is essential.
Peace of mind starts with constant surveillance. A committed security and support team is working around the clock, identifying and neutralizing threats. 24/7 defense is an unmatched peace of mind for any enterprise.
In doing so, it empowers them to better protect their data and operations from future incidents.
5. Ensuring Compliance with Standards
CSaaS helps organizations with regulatory compliance by offering expert advice on following industry-specific security guidelines.
These services don’t just help with compliance initiatives but also help with audits and detailed reporting.
CSaaS providers help businesses stay up to date on current and emerging regulations.
This proactive and preventive approach not only lessens the likelihood of incurring significant non-compliance penalties, but also fosters enhanced trust and confidence among clients and partners.
Industries Benefiting from CSaaS
1. Financial Sector Applications
The financial services industry is one of the most prominent sectors benefiting from a cybersecurity platform like Cyber Security as a Service (CSaaS). It is essential for these organizations to protect vast amounts of sensitive data, making CSaaS an indispensable resource.
As custodians of both personal and transactional information, financial institutions are alluring targets for cybercriminals, necessitating robust cybersecurity measures.
CSaaS provides advanced security solutions to safeguard sensitive data through 24/7 security monitoring and threat detection. This is particularly crucial since dedicated security operations centers (SOCs) are staffed with highly skilled cybersecurity professionals who understand the intricacies of fiscal management.
As we have seen with the increase in cyber attacks, small businesses are especially susceptible, often without in-depth protection.
CSaaS effectively bridges this gap by offering scalable cybersecurity solutions without the burden of building an in-house cybersecurity infrastructure.
This approach allows financial institutions to save time and resources, which can then be redirected to other mission-critical operations, while ensuring data integrity and maintaining customer trust.
2. Healthcare Industry Needs
For healthcare providers, the challenges are distinct, not least of all because healthcare providers must adhere to strict regulatory standards such as HIPAA. CSaaS offers customized solutions that help maintain compliance through ongoing monitoring and adaptation of security measures.
Safeguarding patient data against hacks and breaches is the law. The healthcare sector as a whole has become a favorite target of cyber criminals. The importance of protecting patient information cannot be overstated, given the potential implications for both patients and providers.
CSaaS offers services that include encryption, access controls, and vulnerability assessments to safeguard health records.
For healthcare organizations, these solutions not only protect sensitive data but also streamline operations by reducing the risk of non-compliance penalties.
3. Retail Sector Security Solutions
Retailers face unique cybersecurity challenges, particularly in safeguarding consumer data and securing customer transactions. The retail environment is complex, with numerous points of sale and online platforms, each representing a potential entry point for cyber attacks.
To combat these potential security threats, organizations can leverage a robust cybersecurity platform that ensures their cybersecurity protection.
CSaaS addresses these issues directly by deploying secure networking and zero trust access, forming the backbone of deep, rich cybersecurity solutions.
Retailers benefit from these advanced security features by proactively protecting themselves from fraud and data breaches, which are critical in a fast-paced retail industry.
The service also offers advanced tools for real-time transaction monitoring and provides vital threat intelligence.
This is especially important in an industry characterized by high transaction speeds, where cybersecurity professionals must stay ahead of cybercriminals.
CSaaS solutions are adaptable, offering subscription-based models that cater to retailers of all sizes, ensuring integrated cybersecurity without heavy upfront investments.
This flexibility is immensely beneficial to small to medium-sized businesses (SMBs), yet many still find themselves unprepared for the everyday cyber threats they face.
4. Manufacturing Industry Protection
The manufacturing sector is indeed fascinating, as it faces specific cybersecurity risks that arise from the need to protect operational technology and intellectual property.
Cyber attacks pose a significant threat, potentially shutting down production lines and exposing proprietary information, resulting in millions of dollars in losses for organizations.
To mitigate these risks, leveraging a cybersecurity platform is essential for enhancing their cybersecurity protection.
CSaaS provides a comprehensive set of dedicated specialized solutions, including advanced security features and AI-driven security capabilities, to safeguard these critical assets.
Securing supply chains is another key area where CSaaS has proven indispensable, especially given the vulnerabilities associated with third-party vendors.
With the interconnected systems in manufacturing, the risk of supply chain attacks is heightened.
CSaaS offers 24/7 monitoring to detect potential security threats before they escalate into crises, ensuring that all vulnerabilities are patched promptly.
By utilizing these services, manufacturers can avoid disruptions and continue to operate without interruptions, keeping their intellectual property safe.

Addressing Cybersecurity Challenges with CSaaS
Cyber Security as a Service (CSaaS) comes out as a key solution in addressing today’s cybersecurity challenges. CSaaS can also fit in well with other cloud services and applications.
This delivers a more holistic security posture that is more scalable and cost effective.
By employing CSaaS, companies are able to outsource their cybersecurity management to third-party providers, allowing organizations to tap into the expert knowledge and round-the-clock protection.
This model not only keeps you compliant, but also adapts to address emerging market challenges, delivering dynamic and intelligent defense against threats.
1. Tackling Ransomware Threats
Ransomware stands as one of the most urgent threats today, with incredible impact on organizations.
Alarmingly, 60 percent of small businesses go out of business within six months of that kind of attack.
With CSaaS, you have a strong defense, using proactive approaches to stop breaches before they occur.
By leveraging threat intelligence, these services help organizations strengthen security strategies. Incident response planning is critical, enabling rapid and effective actions to reduce risk and limit damage.
2. Enhancing Threat Detection and Response
These advanced threat detection capabilities are the foundation of effective CSaaS.
These services also enhance response times, so you can act quickly and efficiently when a security incident arises.
Automation is key here, too—automating many of the processes and workflows around threat response so that bad threats can be identified and neutralized quickly.
By taking a proactive approach, downtime can be decreased and data integrity can be protected.
3. Improving Visibility and Control
CSaaS greatly improves an organization’s visibility into its security posture. Along with this comes the need for centralized management of security operations, enabling a single pane of glass overview and control.
With this new level of visibility comes the ability to identify potential vulnerabilities before they can be exploited, creating a proactive, secure environment. Through CSaaS, organizations gain a better, clearer, more complete view of their security landscape.
Key Points to Remember
Cybersecurity as a service (CSaaS) provides a cost-efficient, scalable solution for defending your digital assets.
You get all the benefits of dedicated security experts, without having to maintain a full in-house team.
This customized approach goes beyond one-size-fits-all offerings, delivering personalized solutions that deliver the deep, dynamic defense you need.
- Organizations can offload both their security needs with Cyber Security as a Service (CSaaS). With this solution, enterprises get an end-to-end approach in managing these threats and fortifying their security posture.
- CSaaS covers core elements such as continuous monitoring and threat intelligence. It also makes use of advanced technologies, including AI, to help ensure strong cybersecurity protections.
- Businesses today need in-depth, specialized expertise to understand and address ongoing rapid technological advancements and stay ahead of the curve with compliance and industry standards.
- Organizations benefit from scalability and flexibility with CSaaS. This gives them the flexibility to modify their security solutions as their needs evolve and expand, all without a crushing financial burden.
- CSaaS provides ongoing security monitoring that doesn’t sleep. This crucial service allows for early threat detection and fast incident response, providing companies with the security they need to operate without worry.
- Core industries such as finance, healthcare, retail, and manufacturing stand to gain significant value from the implementation of CSaaS solutions. These solutions are custom tailored to address their individual security issues and regulatory needs.

