Information Security and Risk Management: Developing a comprehensive approach

As more businesses embrace digital transformation, they become increasingly reliant upon cloud service providers and other third-party vendors. Having a comprehensive information security and risk management approach is more crucial now than ever before.
With so many providers accessing company information, there is an increased security risk to business data. Apart from third-party vendors, even fourth and fifth-party service providers experiencing data breaches can leave your system and information vulnerable to malicious attacks.
An effective risk management system is one of the first things organizations can consider to protect their valuable information and services from security breaches.
On this page:
What is Information Security and Risk Management?
Information security and risk management often go together. Generally referred to as security risk management, information risk management, or IT risk management, it stands for the process of addressing organizational information security risks. A company should establish information security to be able to understand and manage overall risk to the services.
Risk management is at the core of information security. It ensures that risks to your assets and services are continuously evaluated and addressed to reduce the risk to a comfortable level.
It is a process of managing risks associated with the use of IT. It involves identifying, assessing, and addressing risks to the business assets’ integrity, availability, and confidentiality.
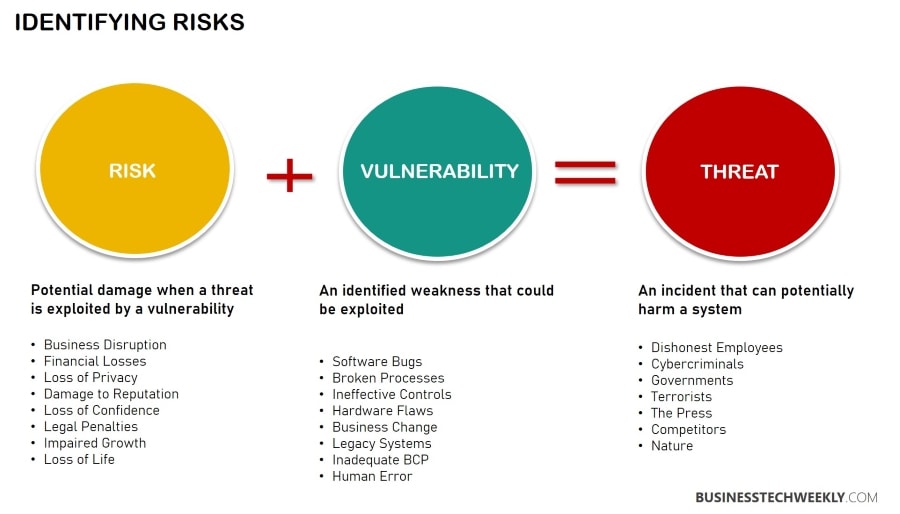
Why is Risk Management Important for Information Security?
Risk management is a process of decision-making and taking measures to address uncertainties around organizational assets to ensure that business goals are achieved. Risk management is a crucial component of information security in a company.
Regular assessment of risks is a critical step in ensuring the ongoing security of the system and data. The goal of this process is to treat risks in accordance with the company’s tolerance levels.
By identifying and analyzing vulnerabilities in the network and system, businesses can prepare well for security attacks and take appropriate measures to minimize the impact of an attack if it occurs.
The policies and procedures forming a part of the risk management program can guide the decision-making about how the organization can manage risks while keeping the bigger goals in focus.
Key Steps in Information Security Risk Management Process
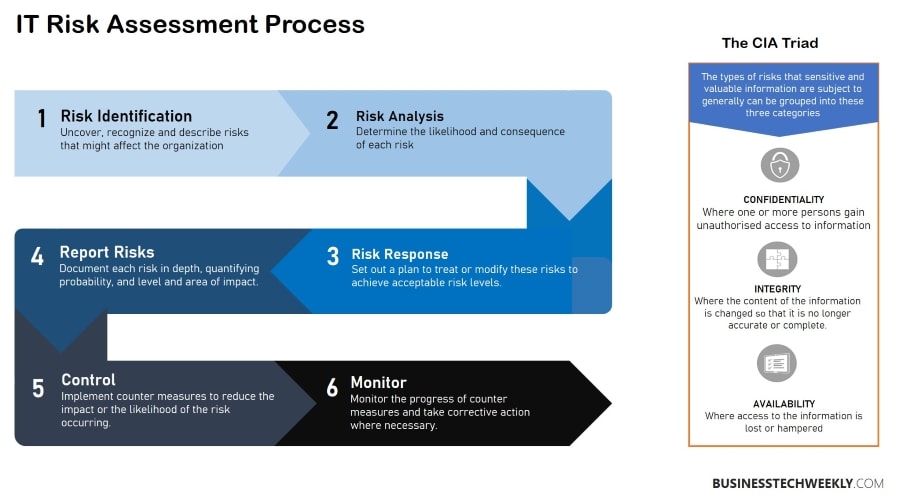
There are a few critical steps that businesses should follow for an efficient information security risk management process.
It is essential to identify the information location, analyze the type of information, prioritize risk, establish a risk tolerance for different data assets and continuously monitor the IT network.
Let us look at the key steps involved in building an effective information security risk management program.
Identification and Categorization of Assets
The first step in securing your organization’s information is to identify what you have. This essentially involves identifying all the locations where the company data is stored. Most businesses conduct an inventory of their databases and applications, but it takes a little more than that.
As organizations embrace cloud-based strategies, data gets more dispersed and is highly vulnerable to threats. Companies don’t rely on server-based storage any longer.
Today, most businesses use serverless and cloud-based storage like shared drives. Some other organizations even use newer ways to collect data, such as customer portals. Newly emerging channels like messaging and email also change the way information is shared.
Finding out where your data resides is not enough for risk management. You should also understand how data moves inward and outward, how the system functions, and what assets are significant for whom.
By understanding the purpose of different assets, you can categorize them based on various factors to identify where you should focus.
Risk Assessment
Once you identify and categorize the assets, the next step involves assessing each asset’s risks. Risk assessment is about identifying the exposure to vulnerability and possible threats for different assets.
Then, you can determine the chances of these threats exploiting the assets. This step helps identify what areas are most likely to be affected by a threat. This will also let you focus your efforts and resources on the most critical risks with the highest impact on the organization.
Response and Mitigation
After you have assessed the risks, you want to address these risks to bring each down to a level that suits your tolerance. In general, there are four responses to any risk – accept, mitigate, transfer or refuse.
The option you choose for each risk depends on the overall risk appetite of the company. As a guideline, you want to put your efforts and resources on the risks that pose the most significant threat and execute controls around these risks to reduce them to acceptable levels.
Monitoring and Reporting
Malicious actors always keep evolving their methods. For example, as IT teams improve identification and protection against new ransomware strains, attackers focus more on phishing and cryptocurrency. So, an effective risk monitoring and reporting system should be in place.
This also means you should not follow a “set and forget” approach to risk management for information security. You should maintain a register of risks and processes and review them regularly. Any changes made to the methods, system, or vision should be reflected in the register.
Risks should also be reassessed when the business environment undergoes any change.
Information Risk Management – Best Practices
A robust risk management system uses a set of policies and strategies tailored to the business. This is because attacks can take several forms, and what works for one asset might not be helpful for another.
However, there are some practices that organizations can implement to start strengthening their information security status. An important consideration is that security teams should have continuous monitoring to ensure that efforts keep up with the evolving landscape of security threats.
Here are some of the best practices organizations can adopt for effective risk management for their information security.
Monitor the IT Environment
Risk management professionals should continuously monitor the IT environment to identify weaknesses, potential risks, and new trends as they emerge and determine what impacts the organization the most.
Monitoring the risk environment also helps the organization prioritize risk mitigation activities. It is essential to analyze vulnerabilities and exposure on a bigger scale to understand the risk landscape in-depth.
Some examples of new trends in the risk environment include changing hacker strategies, an update in technology that could make your system out-of-date, or a recently identified gap in the security system. There are various ways to handle information security risks. It is up to the teams to decide how to manage them.
- Acceptance is when you decide not to fix the risk as it takes more time and effort than the loss incurred if it was realized
- Avoidance means removing all the exposure to any identified risk
- Transfer refers to recovering from the costs of the risk by transferring it to some other entity
- Control involves either fully fixing the risk or lessening its impact to some extent
Every risk requires a different response which can be developed through knowledge and experience.
Monitor Compliance
With data threats becoming stronger, legislative bodies and regulatory agencies have released more stringent standards and requirements. Several new laws have been introduced which require continuous monitoring for compliance.
To create a compliant risk management system, you must monitor and document activities and prioritize mitigation actions while presenting proof to auditors.
Related: Cybersecurity Compliance: An Executive Overview to Establishing a Cybersecurity Compliance Plan
Get Management Support
Top managers in the company should be on board with risk management activities. They should help security teams implement risk management practices by encouraging employees to show expected behavior.
Train Employees
It is worth understanding that risk management is not the sole responsibility of the IT department. This function should not be siloed; departments must be encouraged to participate in the processes actively. Employees should be trained and educated about effective ways to mitigate information security risks.
The risk management team should prioritize creating awareness about security issues and promote a culture of information safety. The risk protocol should be defined well along with the human factor contribution.
Many breaches originate from internal sources, either through an intentional action or an accidentally generated vulnerability.
One of the newest security issues associated with employees is social engineering that uses phishing and other strategies to encourage people to reveal confidential information. Educating employees about these new forms of malicious actions and threats can reduce the occurrences of such issues.
Also see: Ten tips to improve Cyber Security Awareness amongst your employees
Enforce Security Protocols
If staff are allowed to work on their devices from remote locations, measures should be taken to ensure that data on their devices is also encrypted and password-protected.
Protocols like user roles and authentication help avoid unauthorized access and monitor any changes to data through such activities. Certifications and protections for servers can be obtained to ensure systems are not vulnerable to external attacks.
Also, see that all the company data is backed up regularly and all the backups taken offsite are up-to-date. This will make certain valuable data doesn’t get lost in case of an incident.
Whenever possible, try to consolidate data and systems into a single source. Information scattered across multiple locations is harder to monitor and protect.
When you simplify the system structure, it increases the efficiency of the IT team, allowing them to focus more on reducing information security risks.
All the devices and systems within an organization should have end-to-end security installed. A strong password policy should be implemented across the organization with a good level of protection and changing frequency.
Evolve with the Technology
Technology constantly evolves. Therefore, systems must evolve to keep up with the latest changes. Risk management teams must consider the industry standards, internal requirements, and competitors before implementing new technology.
Big pieces of equipment that cannot be replaced should be updated and maintained regularly to ensure they always meet the standard. A weak, out-of-date system is an easy target for attackers.
Final Words
Information security is one of the most vulnerable areas in any industry today. However, implementing a risk management program helps identify, address, and monitor critical risks, protecting business data and services.
With the right strategies and activities, organizations can manage their information, avoid vulnerabilities and stay ahead of threats.

