Why establishing an Information Security Strategy is crucial for your business

When crafting an information security strategy, it is essential to get the input of senior executives as they can provide key insights. Your goal is to understand your business’s IT direction and the strategic approach that will support its needs.
On this page:
Why your Organization needs an effective Information Security Strategy
It all begins with strategy. An IT security strategy plan enables you to define precisely what you will safeguard and how. This contributes to establishing expectations and goals for the entire IT department and business.
With stated goals – and a strategy for achieving them – everyone in the firm can do their duties more efficiently, and businesses have something against which to measure their success.
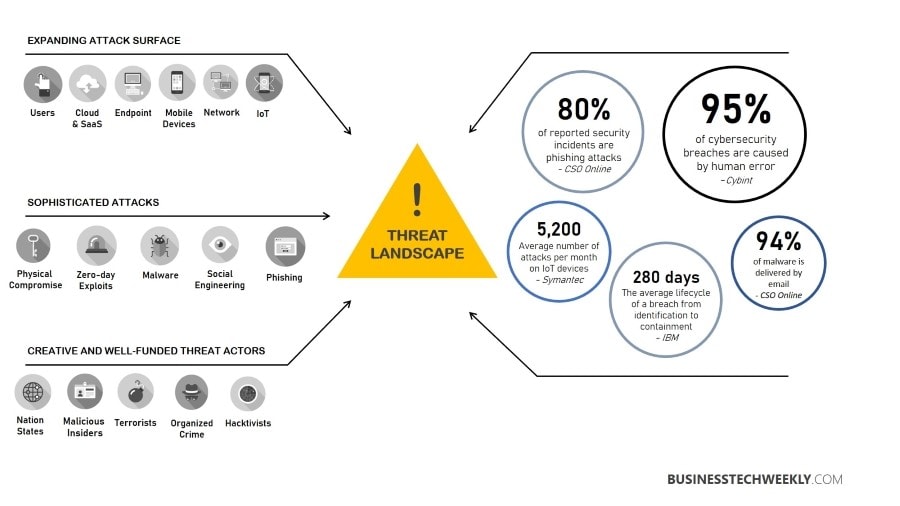
Cyber-attacks are increasing in frequency and severity
Research shows that cyber-attacks are increasing worldwide as more people gain access to the internet and become dependent on it for commerce and communications.
Hackers are constantly looking for new vulnerabilities to exploit, and their attacks are not relegated to a specific industry, which means anyone can be targeted. Small businesses are frequently targeted, with over 40 per cent of cyberattacks being directed at them.

RELATED: Cybersecurity – Who, What, Where, When, Why and How?
Cybercriminals are no longer content to target big corporations and governments; small businesses are now fair game. According to estimates, the average small business loses more than $30,000 a year because of data breaches.
Employee mobility is growing
Working remotely is a growing trend that has been bolstered further by recent events. While there are many benefits to working remotely, many security breaches occur while employees use public WiFi networks in coffee shops or cafes.
Remote employees must be fully integrated into your organizational security strategy. Policies must be implemented to prevent cyber-attacks and minimize the damage if they occur.
RELATED: 5 Cybersecurity Tips for Remote Workers
These measures include ensuring that employees’ personal and work-related data are separately stored, prohibiting employees from transmitting confidential info while connected to public WiFi networks, and ensuring that any security software installed on their devices is regularly updated.

The value of your data has increased significantly
Data has always been valuable, but its value has increased substantially in this day and age.
This is because machine learning allows consumer information to be processed at a rate that wasn’t achievable in the past. This gives companies far greater insights into the interests and behavior of their consumers. Still, this more significant emphasis on data also means that the consequences of having it compromised are severe.
RELATED: How to Protect your Business Data in 10 Simple Steps
For this reason, business owners must protect and correctly store data to ensure it is not compromised or misused. The litigation that can occur if it is could financially cripple you, possibly forcing your company into bankruptcy.
Large corporations can usually cover the litigation costs of having customer data compromised; many small and medium-sized businesses can’t. Ensure that your business complies with GDPR (General Data Protection Regulation), HIPPA or CCPA.
IT is now more prominent
While digital transformation has historically been associated with e-commerce businesses, many non-digital enterprises now depend on information technology.
They are using machines and appliances which incorporate smartphone apps, artificial intelligence and smart electronics. Generally speaking, companies that operate primarily in the digital sphere move quicker than their traditional brick and mortar counterparts.
Consequently, many physical stores, shops and services still lack a digital presence. Even if they have one, many are not adequately prepared for cyber-attacks, which hackers will be happy to take advantage of.
The days when only financial or IT firms were targeted are long past. Even traditional businesses like restaurants are now at risk, so developing a strategic security plan is paramount.
Developing your IT Security Strategic Plan
Once your strategic plan has been crafted, you will significantly boost and extend the institution’s security capacity. Such plans will improve effectiveness and efficiency in making security-related decisions, closely aligned with business and IT strategies.
Furthermore, you’ll be better positioned to adapt to ever-changing compliance requirements. An effective strategic plan defines an overall path for obtaining objectives while focusing on those tasked with completing the mission.
However, it is crucial to understand that crafting an effective strategic plan for your security can be complex. It encompasses a wide range of evolving processes, people and technologies. It, therefore, requires an investment of time, money and effort on your part.
Such plans will guide executives in managing risk correctly while visualizing its overall strategy and purpose.
Developing Your IT Security Strategy
While the need to have a strategy may seem self-evident, developing that strategy may be more challenging.
Here are some basic steps to get started.
- Assess your assets: The first step in developing a protection and security strategy is determining precisely what you want to safeguard. This entails conducting an inventory of your current assets, including data, programmes, and hardware.
- Be offensive and defensive: The most outstanding security strategy examples incorporate preventative measures, routine maintenance, and ongoing education to stay current on emerging risks and contain defensive plans implemented during a security breach or assault.
- Form teams: As you implement your strategy, ensure that everyone on your team understands their role.
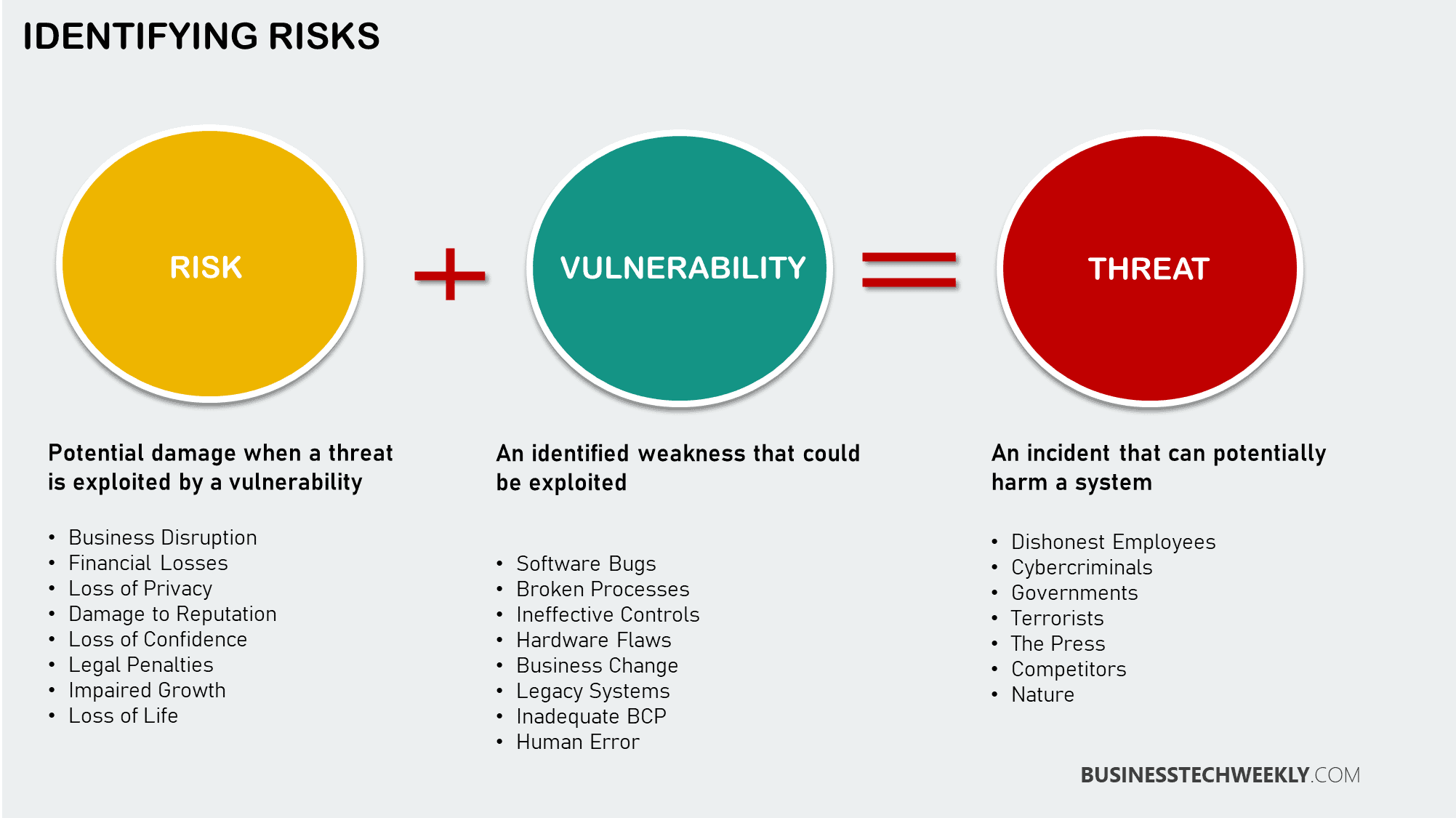
What should be included in an Information Security Strategic Plan?
A strategic strategy for information security can help a company minimize, transfer, accept, or avoid information technology risks associated with people, processes, and technologies.
Additionally, a well-defined plan enables the business to preserve the confidentiality, integrity, and availability of information appropriately. Effective information security strategic planning has significant economic benefits and can provide a competitive advantage.
These may include adhering to industry standards, preventing a damaging security incident, preserving the business’s reputation, and adhering to the business’s commitments to shareholders, customers, partners, and suppliers.
An information security strategic plan should include:
- Detecting and resolving problems
- Reducing the time to delivery from concept to implementation
- Provisioning flexible and adaptable architectures
- Establishing consistent and integrated methodologies for design, development, and implementation
- Making proactive decisions to more efficiently deliver results
- Eliminating redundancy to better support achievement of objectives
A gap analysis of your business’s current state and ongoing actions is a necessary first step toward developing a strategic security plan.
A recorded assessment of an information security programme against a specific standard, such as ISO/IEC 27002, offers more efficient planning, even more so when the standard is incorporated into the strategy.
Additionally, when developing a policy, it is necessary to define the vision, mission, strategy, initiatives, and tasks to be performed to complement the existing information security programme. The strategy should include a list of deliverables or metrics for each effort and the individual accountable.
Your Cyber Security Strategy begins at the top
To obtain the most optimal security program, every function which is security related should be coordinated by the CISO or Chief Information Security Officer. In some organizations, this responsibility may fall under the mandate of the CIO (Chief Information Officer).
CISOs must be strategically positioned to ensure the proper visibility for security-related issues while managing risk that aligns with the organizational directives.
Ideally, the CISO is a focal point for information security and might collaborate with a committee to ensure the LOB (line of business) directives are achieved. They will serve as information security leaders and coordinate programs complementing LOB executives.
RELATED: An Executive Overview to Establishing a Cybersecurity Compliance Plan
When CISOs are used in this role, organizations will significantly enhance their security level while lowering risk. CISOs are responsible for the overall security framework and will offer the presence and focus needed to accomplish its mission.
- Align Business Goals with IT Initiatives – Hiring the correct CISO is the most critical aspect of the program. They must champion protective initiatives across the institution. The CISO should manifest robust leadership, extensive knowledge of security-related matters and proper placement inside the institutional framework.
- Robust Leadership – A robust CISO can offer executive-level leadership when planning, development, supervision, staffing, and coordinating every security or data-related activity.
- Extensive Security Knowledge – The best CISOs have an extensive background in Information Technology and how to secure it. At a minimum, they should have ten years’ worth of field experience. They must also demonstrate exceptional diagnostic capabilities to interpret and apply theoretical solutions to practical challenges.
- Proper Placement – Institutional placement for the security head can vary from one institution to another. However, security programs must be viewed on an enterprise level that addresses technology issues, processes and personnel. Therefore, every CISO requires executive support and sponsorship.
Hiring a CISO or even a CIO may be beyond their need for smaller businesses and organizations. However, such organizations can still establish a tailored information security strategy by engaging the services of a virtual CIO (vCIO).
Establishing your Information Security Strategy in your Business
Changing cyber security policies within an established firm is not always straightforward.
One objective that should be stated to the organization is that short-term convenience will be sacrificed in favor of long-term cyber security protection that mitigates the chance of a massive data leak.
User education programmes can be initiated to teach users how to recognize phishing and social engineering warning flags and cyber security methods, becoming an integral part of an effective onboarding strategy.
RELATED: Ten tips to improve Information Security Awareness amongst your employees
A cyber security strategy should include user onboarding methods, password regulations, and training. User account creation, maintenance, and deactivation procedures can be incorporated into this strategy.
As difficult as it may be to convince a business to adopt these measures, a qualified vCISO can explain why these steps are necessary to improve data protection and mitigate dangers that may cost millions in damages.
Another advantage of a security strategy is that regardless of when someone joins the firm or where they work within the organization, there is an established framework for protecting data and information.
Because data security is most effective when everyone is on the same page, having a comprehensive, accurate, and up-to-date IT security strategy plan helps guarantee that everyone is aware of the plan, even if it directly impacts their daily job.
RELATED: Responding to a Ransomware Attack: The crucial initial steps businesses must take
Additionally, any newcomers can be onboarded more quickly when an information security strategy is documented on a page that can be referred to at any time.
Other benefits of an information security strategy include:
- Simplified solution implementation
- Improved forecast of potential IT security concerns
- Simplified resolution of security issues
- Improved planning for potential security issues
- Improved teamwork on information security initiatives
- Simplified detection of new threats
A sound strategy can ultimately aid in better problem prediction and resolution. It enables a more effective response to any potential concerns that may occur.
Just as sales, marketing, and customer support teams require goals and strategies for achieving them, the IT team requires a security strategy to safeguard assets and ensure the seamless operation of the business’s data processes.
Developing and maintaining an IT security strategy plan is one of the most effective strategies to avoid data loss, theft, and threats.
Additionally, it guarantees that your organization is adequately prepared and understands how to respond to an incident. Does your firm have a robust information technology security strategy in place?

