Technology Risk Management

Risk can be explained as the “effect of uncertainty on objectives,” so if you manage uncertainty in any way, then you can effectively decrease risk to your business. By defining and performing technology risk management, you effectively find out about potential problems before they happen.
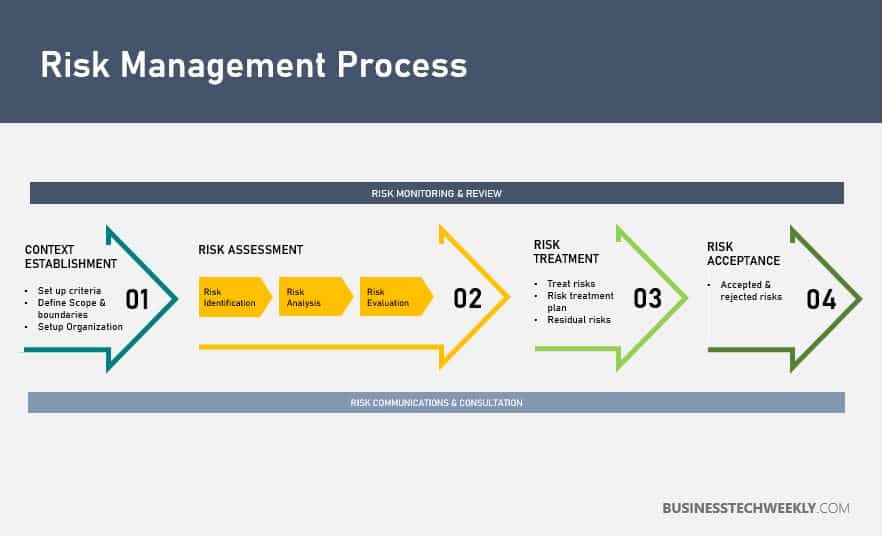
By systematically identifying, analyzing, evaluating, and treating a comprehensive list of relevant risks, undesired situations can be prevented, and negative impacts minimized. In terms of the ISO 27001 standard, this means that information can be protected effectively and used to help a business achieve its goals.
On this page:
What is Technology Risk Management?
Technology risk management entails the application of risk management methods to technology assets to minimize or manage IT risk accordingly.
Technology risk management considers factors such as business criticality and functional and technical fit.

How does Technology Risk Management help?
No organization is free of risks. The increase in international and local regulatory requirements, such as EU GDPR and California’s CCPA, and the need for highly efficient, reliable operations, play vital roles in motivating firms to analyze technology risks.
By adopting a proactive approach to Technology Risk Management, organizations can benefit from:
- A strategic approach to risk management: Creating and allocating resources in the right place, in the right way, and at the right time over time, considering not only the company’s needs but also those of its customers and other interested parties.
- Clear roles: Senior management, technical staff, final users, experts – all individuals involved with information security must have defined functions (e.g., make decisions, identify risks, follow procedures, etc.).
- Actions appropriate to the perceived threats: Companies have to consider and define their limits, so their actions toward risks will be aligned with their objectives.
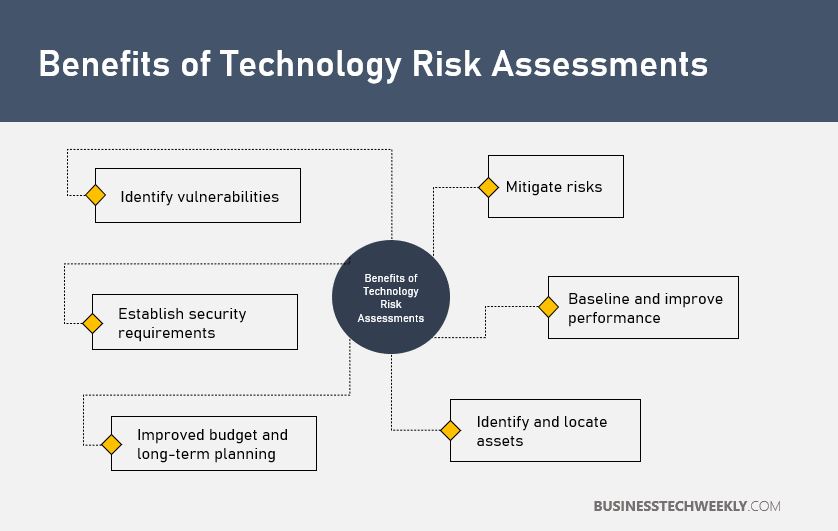
An organization directly benefits from conducting Technology Risk Assessments through reduced costs, a reduction in risk and an increase in your organizational agility.
Overall, these factors increase your business’ competitiveness in a digitalized and fast-paced market.
Conducting a Technology Risk Assessment
Performing a technology risk assessment varies very little from other risk assessments. The primary difference is scope. While well-known risk assessments focus on Information Security risks, Technology Risk Assessments focus on wide-ranging technology assets.
Such technology assets can include hardware, software and applications, and peripherals and multi-function devices.
To conduct a Technology Risk Assessment, you can use an existing Risk Assessment Methodology –remember to augment the scope to include all technology assets.
Mitigating Technology Risk
Technology Risk Management teams should document adequate responses to identified technology risks as part of their risk management plans.
Working top-down, the risk management team can commence by elaborating the risk responses for each technology risk into actionable steps. These step will form the basis of your technology risk management plan.
For instance, you can:
- Review the data you hold on and how it is shared – Ensure proper adherence to data protection laws, and determine what needs to be done public and shared systems. When it is necessary, get rid of sensitive information.
- Install proper security controls – Such as firewalls, anti-virus software or other processes to prevent malicious attempts at penetrating your systems, or gaining unauthorized access.
- Implement adequate security policies and procedures – Such as online usage policies, making sure to train your staff thoroughly. Follow best practices to maintain cybersecurity in the business.
- Contract a third-party computer provider – If you do not have in-house skills or need to bolster your security expertise. Read how to choose the best IT supplier for your business.
Read more about different security measures in ten crucial cybersecurity tips for small businesses.
The risk management team should implement the prioritized actionable steps to proactively prevent the technology risks from occurring. If a technology risk occurs, the risk management team can retrieve the plan and put the appropriate measures into action.
If you cannot get rid of the risks to an acceptable level, you may need to take further steps to prevent these incidents from occurring.
You might want to consider setting adequate procedures for detecting problems (e.g., Viruses affecting the computer system) read about how to identify a security breach.
Where risks cannot be mitigated satisfactorily, you may wish to opt for insurance against the costs of a security breach. Read more about cyber insurance options.
Information Technology Risk Management Policy
IT Risk Management policies and procedures detail the management of technology risks in business. These should form part of your risk management and business continuity strategy.
These policies and procedures need to be made available to your employees. More crucially, you need to take adequate steps to ensure your staff, partners and other resources, are aware of, and understand the following aspects of your IT Risk Management policies and procedures:
- Risks to IT systems and data
- Where are the procedures located and how they are controlled
- Processes for handling daily tasks
- Managing changes in IT systems
- Documented responses to technology or data security incidents
- Acceptable use of technology, such as emails, whilst adhering to data protection guidelines
You should develop what you want and take account of the common problems in your private data. If you haven’t established the threats your business is facing, then it is time to take a computer risk assessment.
What Should A IT Risk Management Policy Contain?
A technology risk management policy contains security procedures, processes and guidance applicable throughout the organization. Often, these are integrated with other employment policies and referenced during the new employee onboarding process.
An Information Technology Risk Management policy may contain:
- IT Security Procedures – Technical controls, such as limiting access to sensitive information, are crucial in securing IT systems. You will require different policies and methods to ensure that adequate controls are in place. Read more about cybersecurity for the company.
- IT Security Standards – Standards are crucial in ensuring that your systems adhere to best practices and industry guidelines. You can read more about IT security standards here.
- IT Staff Policies – Adequate staff policies to correctly handle security threats need to be in place. Consider developing policies which cover social media, internet usage, and emails to protect your systems.
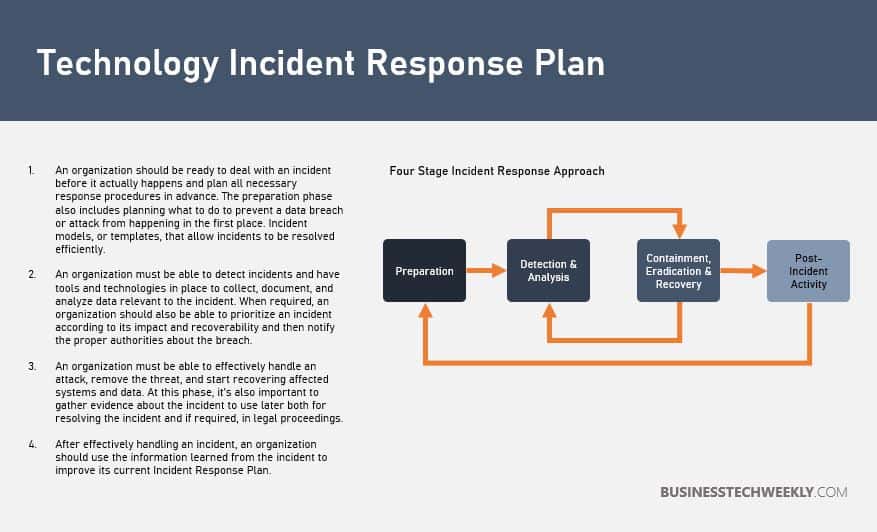
- IT Incident Response and Recovery – IT incident response details how you react to a breach or failure. It is also crucial to identify appropriate actions to take before the occurrence of an incident. This approach will help reduce the damage caused by the incident and reduce the recovery time and costs.
What is an IT Incident Response Plan?
An Information Technology incident response plan is a set of instructions which can help an organization respond to different scenarios such as:
- Data breaches
- Service attacks
- Firewall attacks
- Malware and virus infections
- Insider attacks
- Damage to equipment
- Power and technology failures
Your incident response strategy should identify all the individuals in charge during an incident, clearly describing the roles and obligations. It should state who and how is the plan tested (and how regularly), and also who and how will the plan be implemented.
The business’ incident response plan should be based on comprehensive computer risk analysis.
IT Incident Recovery Planning
How well you respond to severe IT incidents, will determine how quickly your business can recover from the event. It is therefore crucial that you have a plan detailing the steps you need to take to recover from an incident.
Your recovery plan should include at least the following two components:
- A strategy to recover business operations to normal parameters in the fastest possible time
- A description of critical resources, equipment and staff required to recover from the operations.
It is crucial to thoroughly rehearse your plan to shield your business from the incident developing into a full business crisis. You can test the validity of your plan through the following testing methods:
- Checklist Review
- Full-Interruption Test
- Parallel Test
- Simulation Test
- Structured Walkthrough
To aid you in preparing and planning a response to a computer incident, view the NCSC’s guide to recovering the computer system.
You can test and make sure the response is appropriately practised for a cyber attack with the NCSC’s online training tool.

IT Risk and Business continuity
Business continuity planning (BCP) is a crucial part of technology risk management. A business continuity plan will help you to carry out the steps to minimize any potential impact to your business.
You may also need a business continuity plan to:
- Reaffirm to clients that you have seriously considered technology and security risks
- Demonstrate adequate technology risk management to stakeholders, customers, suppliers and insurers
- Ensure you meet any legislative, or industry requirements
How to Write a Business Continuity Plan
Your business continuity plan should take into account certain disruptive events that can impact, your:
- Employees
- Premises
- Technology systems and telecommunications networks
- Utilities and services such as power
- Critical business processes
The plan should state the triggers to activate the plan; what steps need to be taken once the plan is activated, and under what circumstances; and the roles and responsibilities of the individuals and resources involved.
You will need to put in place measures to ensure your business continuity strategy and plan is regularly reviewed and updated. For instance, when employees leave the company, or when new IT systems are introduced.
IT Security Management Standard
The international standard ISO 27001 is an international standard which sets guidelines and best practices for information security management systems. These standards belong to the 27000 group of standards which aim to keep the business’ data assets secure.
See also: What is ISO27001?
ISO 27001 Controls
The standard is what sets controls that are the primary key to maintaining security. The standard covers areas such as:
- Security actions – what does an information security policy cover, what it covers and why the business must have a security policy
- Company security – how to handle data security effectively in business
- Asset control and management – how to properly audit and manage data by itself and different computers, software and services
- Staff security – Training, obligations, procedures and proper response to incidents.
- Environmental security – Keeping critical locations in a safe place and there is proper access to the data and equipment
- Communications management – Proper operation of data processing facilities each day, like computer networks
- Access control – The right to attain data and systems based on business needs, like controlling who can do the things with the data resources
- System development and proper maintenance – If you create your computer software, you will have to figure out how to design the software and properly maintain it to secure and keep the data private
- Business continuity management – Maintaining proper business activities during tough times and dealing with big disasters and typical small problems
- Compliance – Related to national and international laws and regulations
Read more on rules and regulations for best business practices.

