Social media and Identity Theft: What to look out for

Sharing much personal information over the web can lead to your identity being stolen. With the rapid rise of social networks, scammers can now use your photos and data to create profiles and defraud others. So it’s no surprise that businesses are concerned about social media and identity theft.
The risks of social networking sites arise when a person acquires access to an organization’s or executive’s online account by one of two methods. Either by obtaining the third party’s password or building an entirely fake profile and impersonating that organization.
Here we explore the common scams used by cybercriminals to obtain personal data. Also provided are what steps you can take to prevent identity theft of your social media accounts.
On this page:
Why is Social Media being targeted by Identity Thieves?
Social networks are a treasure trove of personalized data and information. Once someone has gathered enough data on you, they can then use it to craft profiles which appear legitimate.
The goal for most cybercriminals is to make money. After they’ve created a false social media page, they’ll contact your co-workers, family members or friends to request money for a completely bogus charity.
Related: 20% of small and medium businesses have been hacked on social media
They might also appeal to their sincerity, claiming that they’re going through hard times and need the money to cover the bills. Once the funds are sent, the funds are never used for the purpose claimed.
However, not every data thief is financially motivated. Some are interested in promoting hate speech or a political agenda and will use fake social media profiles for this purpose.
They are usually enemies of the people whose identities they steal. They will then spread hate messages in a manner that tarnishes or destroys the reputation of the victim.
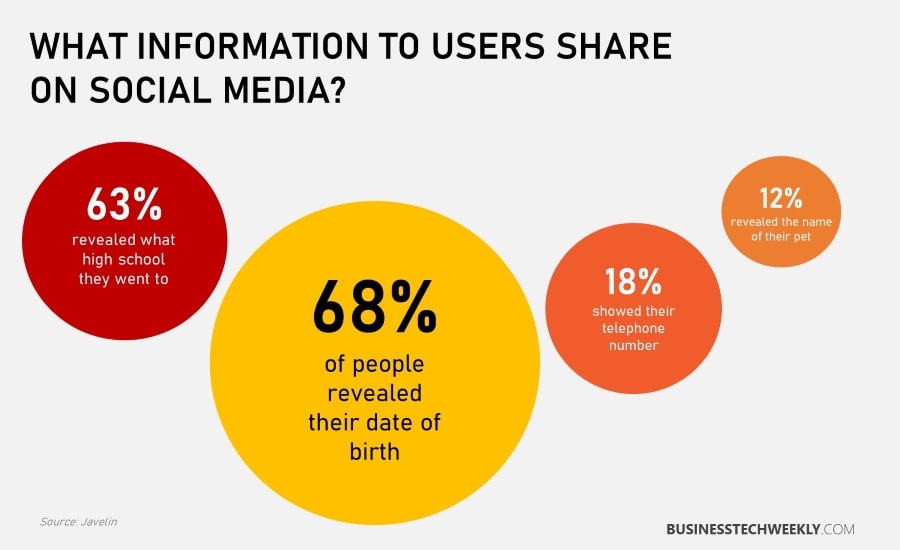
Many users of social networks provide more than enough information for cybercriminals to steal and then create false profiles. Generally speaking, it is better to omit excessive information on such pages. Any information you provide should be generalized.
For example, you might name the state when listing your location, but you don’t have to name the city and certainly not the neighborhood.
How the Scam Works
Thieves use numerous techniques to craft profiles that look convincing. The first and most important is to get your actual name and photo.
Once they have these two things, they can generate a profile good enough to fool most people.
The most sophisticated criminals will look for even more information, such as where you live, went to school, the company you work for, etc. The more accurate info they have on an individual, the easier it is to create a deceiving profile.
Phishing Emails
Another option is to utilize phishing emails to trick people into providing personal data. In the message, they may appear to be an old friend. They will correspond with you, getting you to provide them with more details regarding your address, marital status, the type of work you do and whether you have children.
Once they have sufficient info, they can develop a false profile using your name.
Puzzles or Games
Some scammers use puzzles or games to gather information. They send them to the friends or family of the victim, getting them to name the street you grew up on, the very first pet you had and its name, or restaurants you frequent. The games seem colorful and fun, but in reality, they are designed to gather information, including passwords.
Business or Employment Opportunities
Almost everyone needs a way of making a living, so presenting false business or employment opportunities is one of the common tricks of the scammer.
The exact techniques may differ from one scam to another. However, they all have in common that the initial message you receive will usually be unsolicited.
They’ll promise to send you some product or service that you can sell, which of course, you’ll have to pay for upfront. Essentially, this is a pyramid scheme. If you’re foolish enough to give out the credit card number, you’ll never get the product, and your number will be used for fraudulent purposes.
How to secure your Social Media Data in 6 Steps
There are several steps you can action to protect your social media profile. Becoming more security conscious and disciplined is the best way to avoid becoming a victim.
1. Keep your privacy settings strict – Access the settings for your social media account and edit it in a way where personal data is private. Your personal data includes your current workplace, birthday and other details.
These should only be available to trusted family or friends whom you’ve verified. Being too lenient with privacy settings and making your info available to anyone makes it easy for thieves to acquire and use your information.
2. Log out of your account when not in use – Remaining logged in when you’re no longer using your machine is just foolhardy. An unlocked device allows anyone to access or modify your profile.
If your computer or laptop is stolen and accessed without authorization, your information can be at risk.
3. Install online security software – Security software will actively conceal your identity while surfing social media or the web.
If you mistakenly click on links or download something that contains malware keystroke software, it still won’t be able to access your data.
4. Never post or tag your exact location – Many social media networks have a feature called location tagging. This feature allows people to know your precise location at any given time.
While it might be fun and helpful at times, it can make you highly vulnerable if criminals decide to take advantage of it. It would be better to avoid using this feature unless you have a good reason.
5. Use robust passwords – Identity thieves are always on the lookout for passwords that enable them to access your account. When you use easy and obvious security phrases, it makes it a lot easier for them.
Do not use complete words in your password or include anything involving your birthdate or address. Combine random numbers with symbols and letters that are in a non-sequential order.
6. Make sure your connections and friends are legitimate – When using social media, never provide information to individuals you haven’t met in the real world.
When you befriend people you’ve never interacted with physically in cyberspace, it is easier for them to collect your data and use it against you.
Also read: What is shoulder surfing?

Next Steps
Scams involving social media on sites such as LinkedIn and Instagram are becoming more common. So it’s no surprise that many are concerned about social media and identity theft.
Additionally, just because someone contacts you claiming to be a friend or family member doesn’t mean it’s that person. It might be, but it could also be a scammer posing as them to gather information on you.
There are two ways to tell who is who; the first is to ask them very detailed questions, not on your social media profile that only the actual person would know. The second is to contact them by phone to find out if they sent you a social media request.

