Payroll System Software Security: Protecting Your Payroll Data

On this page:
- What is Payroll System Software Security?
- Why Payroll Systems Need Security
- Common Payroll Security Threats
- Types of Payroll Fraud
- Identifying Information Leak Sources
- Strategies to Protect Payroll Data
- Best Practices for Data Protection
- Response Strategies for Data Breaches
- Importance of Compliance with Regulations
- Key Points to Remember
What is Payroll System Software Security?
Payroll system software security is the security protocols and protections put in place to protect sensitive payroll information from fraudsters and data breaches. You are trained on data that includes sensitive personal and financial information.
This includes sensitive information such as Social Security numbers and bank account information, making it a magnet for cybercriminals.
Smart payroll security involves both digital and physical protections. These steps help protect data integrity and also ensure systems are fortified and resilient enough to avoid unauthorized access and data breaches.
Definition and Overview
Payroll security is critical to protecting employees’ personal and financial information. This requires technology and policy integration to develop systems that secure payroll data in a smart and efficient way. Conducting routine payroll audits, for instance, can identify inconsistencies and remove ghost employees.
We need to keep a constant eye on these systems to counter new threats that arise. This need is informed by a shocking 68% increase in data breaches nationwide from 2020 to 2021. Payroll security begins and ends with payroll software. It provides robust security measures such as data encryption, access controls, and multi-factor authentication.
Importance for Businesses
That’s why payroll system software security is so important. Avoiding payroll financial losses is key to your success. The average cost of a data breach hit an all-time high of $4.35 million in 2022!
Compliance with data protection laws and regulations is another very important area affected by payroll security. Additionally, effective payroll system software security measures can make a positive impact on business operations and employee satisfaction.
Locking up payroll system software security is the key to successful payroll.
In addition to ensuring compliance, it protects employee trust and safeguards the company’s reputation.
Why Payroll Systems Need Security
Protecting Sensitive Employee Data
Securing payroll systems is key to safeguarding sensitive employee data. These systems are full of sensitive information, such as Social Security numbers and banking information.
This lack of security makes them prime targets for cybercriminals.
Deploying strong encryption techniques is critical to protect this data from nefarious hands. Encryption essentially scrambles the data, rendering it unreadable to anyone who doesn’t have the appropriate key.
This rigorous process greatly helps avoid any cyber threats.
Establishing strict access controls is another important step for payroll security. By restricting access and the ability to modify payroll data, the likelihood of internal malfeasance is also diminished.
Control access by assigning access rights based on job function and responsibilities. This ensures that only authorized and trained personnel have access to sensitive information.
Continuously reviewing and updating security protocols is essential to combat new threats. As we all know, cybersecurity is a rapidly changing landscape and staying ahead requires perpetual vigilance.
This proactive approach prevents vulnerabilities before they can be exploited, so sensitive employee data continues to stay in safe hands.
57% of fraud is committed by company insiders or a combination of insiders and outsiders
Ensuring Business Continuity
To maintain business continuity, it’s important to create a detailed disaster recovery plan for payroll systems. This security incident response plan walks you through the process you need to follow step-by-step.
It’s also crucial because it keeps payroll operations running as usual. This continuity is critical to keeping employee trust and confidence, as employees depend on the promise of regular, on-time paychecks.
Undertaking regular audits assists in recognizing vulnerabilities that would prevent payroll processing. These audits can identify payroll errors, root out ghost employees and save taxpayers from millions in wasteful spending.
Improving the integrity of your payroll system helps you find problems and fix them before they turn into big, expensive disasters.
Providing thorough training on the necessity of adhering to security protocols is another major step in ensuring business continuity. When employees understand why these protocols are necessary, they are far more likely to adhere to them.
This strict adherence significantly reduces the opportunity for human error and increases the organization’s security posture on the whole.
Common Payroll Security Threats
External Cyber Threats
Cyber threats specifically targeting payroll systems are prevalent and becoming more sophisticated. Phishing attacks are the most common payroll security threat. Cyber criminals heavily rely on phishing attacks, now the most common way to steal sensitive payroll info.
Phishing is when you deceive employees into providing their login credentials or clicking on harmful links that grant you access. Malware specifically designed to infiltrate payroll systems is a huge threat. These cyber attacks lead to data breaches, costing businesses millions and impacting millions of victims each year.
To counteract these threats, it is essential to use strong cybersecurity protections including firewalls and intrusion detection systems. These tools assist in tracking and preventing unauthorized access attempts.
In addition, teaching employees how to identify and report unusual online behavior is key.
Frequent training sessions help employees identify phishing attempts and other cyber threats. This proactive, education-based approach is the best way to completely protect your organization.
RELATED: Cyber Attack Vectors: Understanding Attack Vector Types & How to Defend against them
Internal Employee Risks
Internal risks usually come from employees who abuse or misuse their access to sensitive payroll data. Disgruntled employees can also intentionally modify payroll data, insert ghost employees, or submit fraudulent reimbursement requests.
These internal breaches only underscore the importance of having strong security policies in place and consistent disciplinary action against policy violations.
Regular training sessions will help remind all employees why data security is so important. When employees know what they are risking by not properly handling payroll information, they will be more likely to follow security procedures.
Implementing end-to-end data encryption also ensures payroll information, if intercepted, is unreadable, adding even more protection from internal threats.
Third-Party Vulnerabilities
Though outsourcing payroll services can relieve some of the stress that comes with in-house payroll processing, it adds third-party vulnerabilities. Ensuring that you evaluate the security measures of any potential payroll service provider should be paramount.
Make sure that these vendors meet your organization’s security requirements and data protection laws. Multi-factor authentication (MFA) should be a must-have for any third-party that needs access to payroll systems.
Monitoring security with periodic audits of third-party providers are also key to maintaining compliance with security protocols. These audits also provide useful information about any vulnerabilities within the provider’s security infrastructure so that they can be remediated accordingly and in a timely manner.
Exercise ongoing, heightened vigilance of third-party contractors to reduce exposure to threats. This method makes sure that your payroll processing is both secure and streamlined.
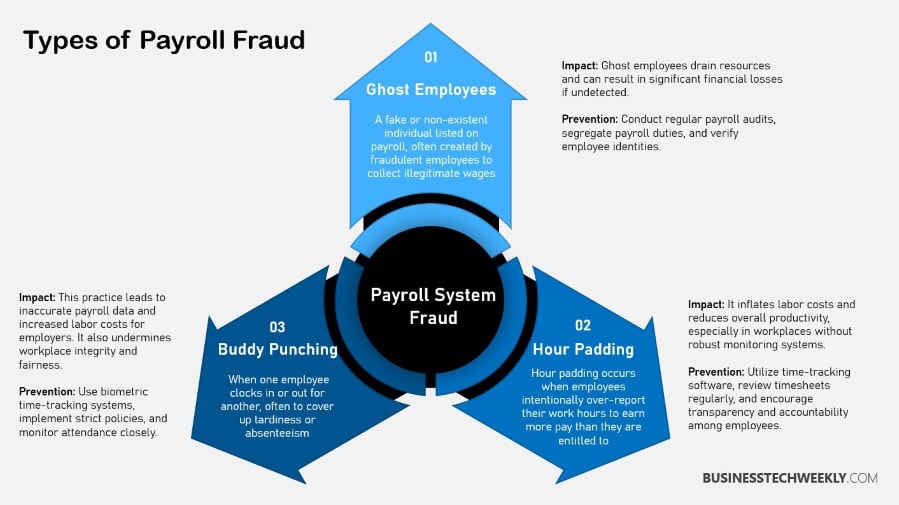
Types of Payroll Fraud
Knowing the different types of payroll fraud will help you safeguard your organization’s fiscal assets and preserve employee confidence. Some other common types of payroll fraud are using ghost employees and inflating hours.
Ghost employees are imaginary employees inserted into the payroll, enabling scammers to siphon money to themselves.
Inflated hours is when employees pad their timesheets with hours they didn’t actually work. Here are some of the common types of payroll fraud. Such as having an employee punch in for a coworker who goes home early, or altering hourly rates to make them pay more.
Alarmingly, payroll fraud makes up 27 percent of all employee theft and accounting fraud—that means every organization is at risk no matter your industry.
Small organizations with fewer than 100 employees are especially at risk, suffering this issue nearly two times as much as larger organizations. The monetary effects are staggering, with average losses per occurrence amounting to $63,000 to as much as $1 million over a 30-month span.
Identity Theft and Manipulation
This form of payroll fraud is an ongoing danger, since it includes thieves gaining access to confidential employee data. This breach opens the door for cash payments to be made by manipulating payroll records, costing the employer money and eroding employee trust.
By overseeing payroll documents for suspicious alterations, you’ll notice where people may be attempting to manipulate or commit fraud.
Educating employees on safeguarding their personal information is equally important, as this empowers them to prevent identity theft.
For example, employees need to be trained on identifying phishing attempts and use strong, unique passwords for payroll system access.
Unauthorized Access and Alteration
Stopping outside forces from accessing and changing payroll information is key to keeping your payroll system secure. Implementing more stringent access controls to make sure only those with a business need have the ability to change payroll records.
Using audit trails is a great way to keep track of all changes made and flag any suspicious activity or security threats. Monitor user access permissions on a regular basis.
This practice protects sensitive data by limiting access to just the individuals whose jobs require use of that data.
When you implement these policies, you significantly reduce the chance of improper access and modifications.
This proactive approach not only protects your organization’s financial assets, but also fosters trust among employees.
Buddy punching costs US employers $373 million per year
Identifying Information Leak Sources
Identifying sources of information leaks in payroll systems is the first step to protecting sensitive employee data. In-depth investigations can identify leak sources, including those resulting from internal mismanagement and external actors.
For example, log analysis of access logs to determine who accessed what data and when can help identify patterns that suggest a breach.
Continuously monitoring employee behavior and access patterns is a key component. It further allows you to identify suspicious behaviors like accessing payroll files without permission that could signal a possible breach.
External Hackers
External hackers are a serious threat to payroll systems, frequently exploiting vulnerabilities to steal sensitive information. By keeping up with the newest hacking technologies specifically targeting payroll systems, you can help make yourself more prepared to defend against these threats.
One of those layers is implementing multi-factor authentication, which adds a second layer of security and drastically reduces hackers’ chances of penetrating your systems.
Keeping security software regularly updated helps provide protection against vulnerabilities that are just now being discovered that hackers can try to exploit.
For instance, since the start of the pandemic, hackers have worked more often from public locations, using unsecured networks to access payroll information.
By remaining vigilant and proactive, you can shore up your payroll system to prevent these outside attacks.
Internal Employees
External threats certainly capture our attention, but we cannot forget to address the role that internal employees play. They represent a shocking 74% of all cyber incidents. To help prevent internal risks, creating a culture of security awareness among all employees is key.
Conducting background checks on employees responsible for sensitive payroll information can help ensure risks are further mitigated. Involving employees is essential in keeping a safe environment.
As an example, unauthorized hours on timesheets are a sign of payroll fraud, but employees’ vigilance can prevent these discrepancies from turning into fraud. By encouraging vigilance and responsibility, you foster an environment in which security becomes a workplace value.
RELATED: Spotting Red Flags of Employee Fraud in your Business
Third-Party Providers
When outsourcing payroll processing to third-party providers, assessing their security protocols is vital to ensure they meet your organization’s standards. Including security requirements in contracts with these providers safeguards against potential leaks due to inadequate measures.
Regular evaluations of third-party providers’ performance in maintaining payroll data security are necessary. For instance, if a provider’s security measures fall short, it could lead to unauthorized access, compromising payroll information.
Utilizing third-party software companies to scan your network can further ensure best-in-class security, providing an additional layer of protection.
By thoroughly vetting and regularly reviewing third-party providers, you maintain control over your data’s security.
Strategies to Protect Payroll Data
1. Implement Access Controls
Introducing strong access controls internally at your organization is the foundation of payroll data security. Role-based access control (RBAC) is a good start. It’s also the easiest way to make sure employees can only see the information they need to do their job functions.
For instance, a staff member in the finance department might need access to different data sets compared to someone in HR. Regularly reviewing and updating access permissions is important, particularly when there are changes in employee roles or responsibilities.
Keeping detailed access logs, while boring, is a very important part of keeping a close eye on your payroll system.
It prevents any rogue attempts in real-time, providing an additional level of protection.
RELATED: Role-Based Access Control (RBAC): What is it, and how does it work?
2. Encrypt Sensitive Information
Encryption is a key line of defense against unauthorized access to sensitive payroll data. Whether it’s using industry leading encryption technologies to protect payroll data in transit, you’re also protecting it when it’s at rest.
Education is a key component in this effort as well. Employees should first understand what encryption is and why it’s so crucial to protecting payroll data.
Conducting regular reviews of encryption practices helps to make sure that they are up to date with new security standards, keeping a strong line of defense against breaches.
3. Regular Software Updates and Patches
Regularly updating payroll software is a crucial defensive measure against known vulnerabilities. Regularly scheduled updates and quickly applying security patches as they are released eliminate vulnerabilities that may be exploited.
Incentivize employees to maintain current hardware and software. This new action complements our work and helps provide a safer space for protecting payroll data.
4. Conduct Audits and Monitoring
Conducting regular audits of payroll processes assists in identifying potential payroll system software security vulnerabilities and process improvements. Monitoring payroll transactions proactively for anomalies can help identify signs of fraud or a breach.
Automated tools also make the auditing process easier, improving the accuracy and efficiency of payroll audits. These practices help make sure that if something is off, it gets found and fixed quickly, helping to maintain the integrity of payroll data.
5. Employee Security Training
An effective, ongoing training program on payroll security best practices can help educate employees to be that first line of defense. Regular refresher courses ensure they’re in the know about new and changing security threats, encouraging a culture of proactivity.
Motivating employees to share valuable insights and experiences that can impact payroll security fosters a culture of awareness and resilience against possible threats to payroll data.
6. Secure Physical Access Points
Protecting physical spaces where payroll data is stored or processed is just as important. Putting physical security measures in place limits who can access documents and systems.
This way, only authorized personnel can access and manage sensitive information. CCTV and access control systems offer 24/7 surveillance, deterring potentially harmful activity and enhancing security protection.
RELATED: 5-step Data Breach Response Plan for modern business
7. Establish a Recovery Plan
Having a comprehensive recovery plan can make all the difference in limiting disruption when a data breach occurs. Continuous testing and refinement ensure that the plan remains effective.
By training employees on their roles, you ensure a unified response.
Taking these steps ensures that your organization is ready to quickly recover and continue payroll operations—even when the unexpected occurs.
One-quarter of workers inflate their hours over 75% of the time
Best Practices for Data Protection
Protecting payroll data continues to be an important issue for all organizations that want to protect sensitive employee information. A better, more holistic approach is needed. This includes a long list of best practices that can be implemented.
Incentivizing employee compliance with protocols is crucial. Strong passwords and multifactor authentication work together to create layers of security. Training sessions must also be continual, reinforcing the importance of data protection.
Regular audits, preferably done quarterly, help catch any security gaps before they can be exploited. These audits ensure that your systems stay fortified against the latest threats.
Monitoring systems in a proactive manner allows for quicker prevention of any unauthorized access and potential data breaches.
Limit Access to Essential Personnel
With payroll data containing sensitive information, access should be restricted to key personnel. Develop strict criteria rooted in job duties when granting this level of access.
Regular reviews of access lists reduce the risk of exposure to sensitive information. However, due to role management features built into nearly every payroll software platform in 2024, assigning access is a breeze.
To ensure the integrity of your data, revoke access immediately when employees change roles or leave the organization.
Establish Clear Access Protocols
Written policies that dictate who can access data and how establish a clearly defined method for protecting payroll data. Making sure that every single one of your employees is aware of these protocols is key.
Frequent communication updates also ensure that everyone’s on the same page about any changes that might arise. Consider scheduling monthly or quarterly meetings with software providers or internal IT teams.
This practice ensures that the most recent updates and patches are installed, significantly improving system security.
Data encryption, which renders intercepted payroll data unreadable to unauthorized parties, is also important and should be a given.
Response Strategies for Data Breaches
Developing a strong response strategy for payroll data breaches is essential. This strategy is meant to be a living, breathing, inclusive, and ambitious blueprint. It details the specific steps the company must follow in the event payroll data security is breached.
An effective breach response strategy reduces potential damage and protects the all-important confidence of employees and other stakeholders. Central to this strategy is the creation of a specialized response team.
Their responsibility should include addressing breach incidents as they happen and communicating clearly and effectively both inside and outside the organization.
Each team member needs to have a clear sense of their role and responsibility so that each person can act quickly and in concert with others during a breach. Continuous drills and training sessions will help get employees accustomed to real-world scenarios.
These kinds of exercises both solidify the overall response strategy and help instill confidence in the staff responsible for executing it.
In the end, all of them are ready to respond quickly, efficiently, and competently if a data breach occurs.
Immediate Containment Measures
If you think you’ve experienced a payroll data breach, swift action is essential to prevent further damage from occurring. These steps should be clearly detailed in the response plan to give a step-by-step guide to ensure swift action.
Employees need to be taught why they should report any potential security incident as soon as it happens.
Foster a culture that rewards staff for identifying adverse events early. It’s important to communicate to them that their actions have an essential role in minimizing future dangers.
Containment measures may include immediate isolation of affected systems and preservation of system logs.
It’s equally important to keep the breach confidential to avoid tipping off the bad guys who might be behind the attack. In practice, urgency gets deprioritized when systems remain functioning at first.
Unexpected terminations can result in loss of data and cause additional challenges.
The Kronos ransomware attack that hit in December 2021 extended the recovery process and left many client-employers hanging for months. So a measured approach is called for, one that always prioritizes data integrity and containment.
Notification and Reporting Procedures
A detailed protocol for public notification and reporting of stolen data should be a priority in the event of a data breach. This means notifying affected individuals and authorities as soon as possible, by the law and in the interest of transparency.
To help protect against any possible harm, we are providing one year of free credit monitoring and identity theft protection. Including resources like the FTC’s Identity Theft: A Recovery Plan can further assist individuals in managing any fallout.
Documentation of all actions taken in the wake of a breach is essential for regulatory compliance and a demonstrated accountability. Documentation every step of the way makes it easier to trace back the process and defend the decisions made if challenged.
Employees need to be trained on the importance of communicating in a timely manner during a breach event. They need to know that making them wait only exacerbates the damage.
This is especially important considering that the rise of remote work was a driver behind 25% of breaches in 2021 alone.
Well-trained staff are better able to respond quickly and focus on effective communication.
Importance of Compliance with Regulations
Following data protection regulations is essential in preventing legal retribution. Review your payroll system software security to ensure compliance with these laws. This will save your agency from expensive penalties that can be $50 to $1,000 for every infraction.
Keep in mind, there can be added expenses due to underreported taxes as part of the penalty phase. After all, compliance isn’t just about avoiding fines. It’s about creating a safe space for your workers and customers.
When you make payroll data security a priority, you earn your clients’ trust and show that you are serious about keeping their sensitive information safe. This trust is important, all the more so when 72% of small businesses struggle with payroll compliance.
In order to keep that trust, you need to actively be looking to review and revise your compliance policies regularly. Regulations are constantly evolving, and your organization needs to be a step ahead to avoid the risk of penalties and fines.
Businesses putting money into payroll software to comply with industry standards see remarkable returns. They tout a 40% greater speed in processing and a 90% decrease in payroll errors. This proactive approach helps ensure your business stays in compliance with regulations, while also improving the efficiency of your operations.
Understanding Legal Obligations
The first step in protecting sensitive payroll data is educating your team on legal obligations to protect this data.
For example, employees must be educated on privacy laws to make sure that all payroll procedures comply with applicable laws.
Additionally, routine evaluations of your organization’s compliance status are important to pinpoint where things can be improved and re-calibrate accordingly. This constant process of review protects you from expensive mistakes and keeps your payroll system up-to-date with legal obligations.
Consequences of Non-Compliance
The consequences of not following payroll data protection regulations are severe. Financially speaking, non-compliance results in fines and legal fees, an inconvenience to any organization.
Given that 85% of companies are hit with fines for payroll non-compliance, that financial cost is clear. Beyond the monetary impact, reputational damage from data breaches or compliance failures can be catastrophic.
With the average cost of a data breach in 2022 reaching $4.35 million, it’s clear that strong payroll system software security practices are paramount. Companies that trust their payroll software increase employee confidence by 20%.
They also save 15% on turnover rates, showing the obvious benefits of compliance.
Key Points to Remember
Payroll systems are the lifeblood of any organization.
Effective payroll system software security protects your data and helps keep your business running without interruption.
Implementing encryption, regular audits, and other proactive measures protects your sensitive information from those looking to exploit it. Understanding the dangers allows you to identify vulnerabilities before they can become an embarrassing breach.
- Payroll system software security is essential for protecting sensitive employee and company data from unauthorized access and breaches, incorporating both digital and physical safeguards to maintain data integrity and trust.
- Businesses must prioritize payroll security to prevent financial losses from fraud and data breaches and to ensure compliance with data protection laws, which can enhance operations and employee morale.
- Encrypt data at rest and in transit, and establish strict access controls to protect sensitive employee information. Continually improve your security practices to protect against evolving cyber threats.
- Create a detailed disaster recovery plan, which will help keep your business running during a crisis. Perform frequent audits and employee training to mitigate vulnerabilities and keep your payroll operations secure.
- Recognize and address common payroll security threats, including external cyber threats, internal employee risks, and third-party vulnerabilities, through advanced cybersecurity measures and regular evaluations.
- Take proactive measures like these to protect your payroll information. Implement access controls, encryption, software patching, and comprehensive employee training. Create a strong response plan for any such potential data breach.

