PCI DSS: 12 Requirements of the Payment Card Industry Data Security Standard

Whilst not legislation, the 12 PCI DSS requirements are industry standards introduced and maintained by the payment card industry. Small businesses and merchants will want to ensure PCI DSS compliance to their customers’ sensitive data is protected and safe. Formed and upheld by the payment card industry, the PCI DSS (Payment Card Industry Data Security Standard) identifies the criteria payment card merchants need to achieve to minimise and prevent data breaches. Attaining the twelve requirements of PCI DSS compliance protects the merchant should a breach occur from financial penalties levied by banks. Presented below are the 12 PCI DSS requirements and what they cover, helping businesses remain PCI compliant.
Payment Card Industry Data Security Standard (PCI DSS) principles
Before detailing the 12 PCI DSS requirements, businesses and organisations should be aware of the six PCI DSS goals . These goals, or principles, need to be achieved using several procedures and policies identified by the PCI DSS. Each of the 12 requirements correlates to a PCI DSS goal. The 6 fundamental principles of PCI DSS are:
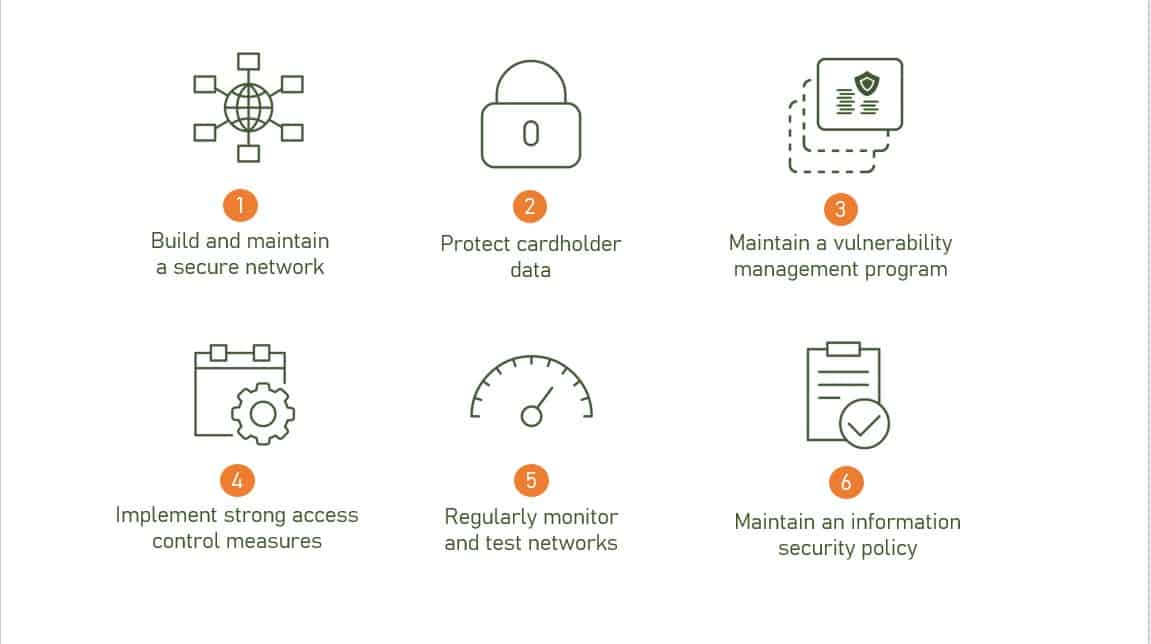
To be considered compliant, the merchant must ensure the environment where the payment card data is processed, stored and captured, meets these criteria. The twelve PCI DSS requirements and how they relate to each of the 6 PCI DSS principles are presented below:
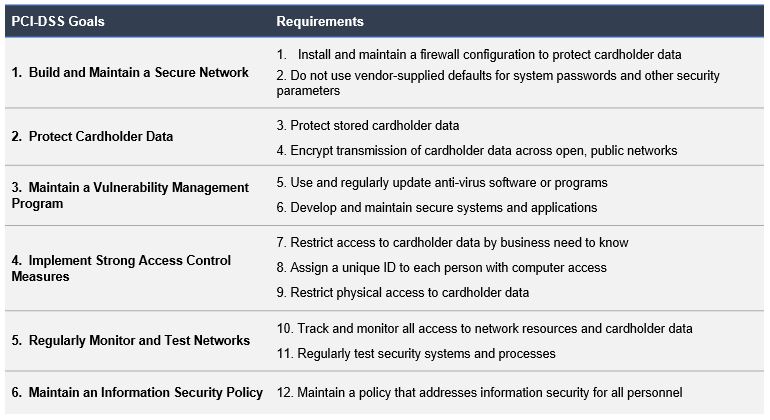
The 12 Requirements of the Payment Card Industry Data Security Standard (PCI DSS)
The PCI Security Standards Council established and maintains the 12 PCI DSS requirements. The standard covers technical and operational aspects of the payment card transaction environment. Crucially, these requirements focus on ensuring that cardholder data is continuously protected. The PCI Data Security Standards are applicable to any organisation which processes, stores or transmits. In addition to small and medium businesses, other types of organisations must thoroughly understand the PCI DSS standards since PCI DSS is also applicable for mobile devices. The 12 PCI DSS requirements are explained further below:
PCI DSS Requirement 1:

Cybercriminals rarely need to access cardholder data physically to steal or exploit it. Consequently, a tenet of the PCI data security standard is to establish, and ensure a safe and protected network is continuously maintained. Identified as the first requirement, PCI DSS requires that merchants, business and other organisations, securely configure firewalls, and routers, where applicable. Criteria for both routers and firewalls need to be established. This will enable the equipment to be tested in a standard manner when either software or hardware changes are implemented. All configuration settings should twice-yearly reviewed to ensure that all unauthorised traffic is restricted. Exceptions may include any requirements whereby a particular communication port is necessary for processing cardholder data. Furthermore, within the payment card data environment, any component or device should be prohibited from accessing the internet. Any computers, laptops or mobiles, used by relevant personnel, to access the organisation’s network, must have local firewall software installed.
PCI DSS Requirement 2:
While cybercriminals and hackers are always seeking new methods to breach a business’s cybersecurity defences, the simplest exploit available to malicious actors is where crucial systems have not had their standard passwords changed. For convenience, network devices such as firewalls, routers, or other system software or hardware are likely to be shipped with a standard username and password. Typically, for instance, such devices will often be supplied default usernames and passwords, such as “admin” as the username, and “123456”, “password” or “admin”, as the password. Malicious actors, whether internal or external to an organisation, can easily identify the default username and password for a particular manufacturer and device with little effort, and as a consequence provide the criminal with the ability to compromise a system. Consequently, the second requirement of PCI DSS aims to address this. In order to meet this requirement, all manufacturer set passwords and default security configurations have to be changed prior to the device, component or system being connected with the existing payment card environment.
PCI DSS Requirement 3:

This requirement focuses on securing stored data. Protecting any cardholder data, whether in a physical or online format, is crucial for several reasons. As such, PCI DSS mandates that all stored data must be encrypted and sensitive cardholder data is never stored or revealed post-authorisation. To prevent unauthorised usage, organisations which accept payment cards must protect cardholder data. Consequently, unless necessary for business, legal, or regulatory needs, organisations should never store cardholder data. Where cardholder does need to be stored, the retention time for that data must be to the absolute minimum, with a purge performed quarterly at a minimum. Sensitive data should only be stored to finalise a transaction – even if that data is encrypted. This requirement further covers the manner in which Primary Account Numbers (PAN) may be displayed, for instance only revealing the first 6 and last 4 digits. It should be noted, any legislative or card provider stipulations, for example, those which may further restrict the data that should be present on POS (point-of-sale) receipts, supersedes this.
PCI DSS Requirement 4:

When cardholder data is transmitted across public networks, cybercriminals can potentially intercept that data. If in the event, a business is processing, storing, or transmitting cardholder data across open public networks (including the internet), they need to be using the strongest level of encryption available to protect that data. Preventing any meaningful use of the data by cybercriminals can be achieved by encrypting data before transmission, and decrypting upon receipt. This requirement makes recommendations which ensure that cardholder data is protected during transmissions through mandating the use of strong security protocols, such as Transport Layer Security (TLS), IPSec, and Secure Shell (SSH), and cryptography. It further mandates the deployment of industry standards, for instance, for wireless networks, it is recommended to use IEEE 802.11i.
PCI DSS Requirement 5:

The PCI data security standard mandates a proactive approach to identifying vulnerabilities, including deploying antivirus. Installing antivirus software will contribute to keeping your customer’s data and your business’ computer system and data safe. Businesses will need to run regular scans, ensure that anti virus is always active, kept up to date and generating auditable logs to provide adequate protection from all online threats. Vulnerability management must not be just limited to core systems. Any computer bespoke applications or programmes which are developed or written will need to be assessed for potential vulnerabilities, through testing and maintenance. All systems should have antivirus installed, including the laptops, mobile devices and computer workstations that are used by relevant for accessing the cardholder data systems both from local and remote devices. Related: Best antivirus for business
PCI DSS Requirement 6:

Building on the theme of vulnerability management, organisations must ensure that systems are kept up to date with the latest manufacturer-recommended updates and security patches. Keeping the software secure will limit the likelihood of exploits by malicious actors. Cyberattackers will often exploit security vulnerabilities to gain access to payment card systems in the targeted environment. In most cases, security vulnerabilities can be fixed with vendor-provided security patches. However, the installation of those patches is often delayed, or worse, not installed at all. To protect the cardholder data environment, PCI DSS calls for all systems and applications to have vendor-approved security patches implemented within a reasonable period. In conjunction with installing critical security patches regularly, organisations must have in place a process to both discover and grade any new vulnerabilities. The requirement to develop and maintain secure systems and applications covers all systems and applications within an organisation’s environment, not just systems and applications bought commercially or developed. See also: Implementing a Patch Management process
PCI DSS Requirement 7:

Within PCI DSS, ‘need-to-know’ is a core concept. Unauthorised access is not only applicable to external malicious actors but individuals within the organisation as well. The objective is to only permit authorised access to the data. An individual requesting data that is not relevant to their task should not be provided access to the data. Robust access control measures would entail merchants determining access to cardholder data as requested. While employees are likely to have authorisation to access specific data generally, that permission may be rescinded in particular circumstances. Therefore, each request must be assessed by the system, considering the individual generating the request and also the scenario or need for that data. The access control system should, by default, function in a manner that any request which is not explicitly permitted is denied. See also: 10 Steps to prevent data misuse and theft by employees
PCI DSS Requirement 8:
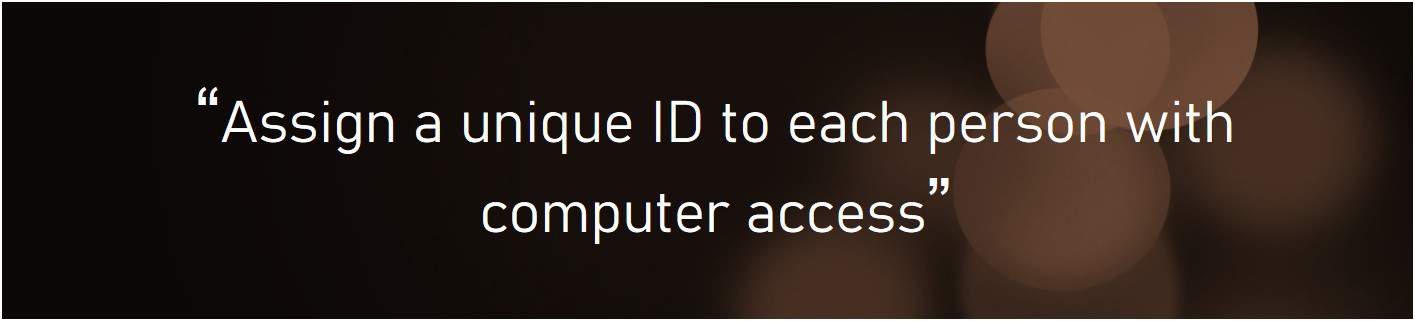
Implementing robust control measures require a unique ID allocated to every authorised user. This allows for an audit trail to be produced of any attempts of unauthorised access at a minimum, but also whenever an authorised user obtains or retrieves cardholder data. Two-factor authorisation (2FA) is a mandatory requirement for remotely accessible system components. With 2FA, one factor cannot be used twice. PCI DSS suggests using technologies such as Remote Authentication Dial-In User Service (RADIUS) and Terminal Access Controller Access-Control System (TACACS). Both of these make use of tokens as a second authentication factor. That is, in addition to a password, a token is used to complete authentication.
PCI DSS Requirement 9:

Access control measures are not limited to just computer systems and devices. Physical access control, limiting physical access to sensitive data, is also mandated by PCI DSS. This ensures that individuals, such as contractors, consultants, employees, guests and vendors, do not have an opportunity to illicitly obtain data via physically accessing the devices, hard copies, and systems. For physical access control to be effective, it needs to restrict movement as well as monitor and log any such activity. Organisations must ensure that appropriate procedures are readily available to quickly identify individuals, who, are not authorised to be on site. This may require employing security personnel or monitored CCTV systems to ensure enforcement. Any media needs to be secured physically, with backups maintained off-site. Organisations should also have in place the controls and procedures to prevent data from being exposed once physical access to the data has been authorised, and dictate the destruction of all media once it is no longer needed by the business.
PCI DSS Requirement 10:
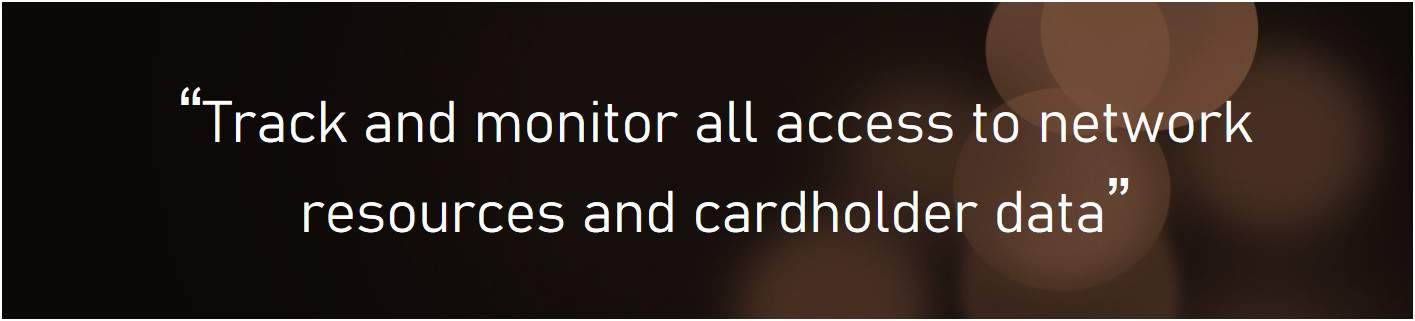
A cardholder data environment is made up of several wired and wirelessly interconnected systems. Data can be stolen by cybercriminals through the exploitation of any network vulnerability. The PCI data security standard aims to identify and minimise the exploitation of any such vulnerabilities by requiring organisations by regularly monitoring and testing their networks. Organisations can fulfil this requirement by employing software and tools to monitor and log network activity in real-time. However, to ensure these systems are effective, thought must be given to the underpinning requirements, for instance, the capability for tracing data traffic to an individual. It is necessary that organisations can reconstruct the events using the data provided from audit trails and logs. Recognising the value of this, PCI DSS specifies a certain quality, in reference to the data captured within the audit trail records. For instance, time synchronisation is mandatory. All audit data has to be stored securely and available for at least 12 months.
PCI DSS Requirement 11:
Due to environmental changes, such as new code or updates, all systems, procedures and processes have to be regularly tested to make sure security is upheld. On a quarterly basis, organisations must test wireless access points (WAP), as well as perform vulnerability scans, both internally and externally. In addition to these, assessments are also required whenever there has been a significant change in the network. PCI DSS also mandates further, ongoing evaluations, such as penetration testing, and using intrusion detection systems (IDS) and intrusion prevention systems (IPS), to ensure the security of the cardholder data environment is maintained. File monitoring has also been identified as a necessity. This allows an alert to be sent whenever an employee has, in an unauthorised manner, modified system files either by way of content, or configuration. By comparing files on a weekly basis, the system can detect changes which may not have been typically noticed.
PCI DSS Requirement 12:

At the core of the payment card industry’s data security standards is the goal of ensuring information and data security best practices, ultimately with the aim of protecting cardholder data. It, therefore, comes as no surprise that developing, reviewing and updating the information security policy (sometimes referred to as InfoSec Policy) is a requirement of the PCI data security standard. PCI DSS goes further, in a sense, that the requirement for the information security policy also highlighted the need to distribute it amongst employees and relevant stakeholders. Companies attempting to attain PCI DSS compliance must implement an annual process which reviews and challenges its information security policy to ensure its relevancy to the organisation’s environment. Furthermore, it is paramount that in line with the InfoSec policy, all procedures and policies relating to security are updated and revised. The requirement further mandates that the responsibility for these activities falls to a single entity, described as an agent (the scope may determine this to be a team, rather than an individual). These agent(s) are tasked with creating the appropriate level of awareness of information security within the organisation. To prevent insider threats, these agents also contribute to the screening of potential employees and contractors during the employee and supplier onboarding processes.
12 requirements of PCI DSS explained
The video below provides an good introduction to the twelve requirements of PCI DSS:



