Web Application Penetration Testing: What You Need to Know

On this page:
- What is Web App Penetration Testing
- Impact of Web Vulnerabilities
- Business Risks and Consequences
- Process of Penetration Testing
- OWASP Methodologies in Testing
- Benefits of Regular Penetration Testing
- Best Practices for Conducting Tests
- Duration and Expectations of Testing
- Skills and Tools for Penetration Testing
- Job Outlook and Career in Penetration Testing
- Key Points to Note
What is Web App Penetration Testing
Definition and Purpose
Web application penetration testing (or pen testing) is a simulated cyberattack on your web apps, functioning like a friendly hacker who identifies security gaps before malicious hackers can exploit them.
This web app penetration testing process essentially tests how much your web app can withstand against potential threats.
You’re not merely seeking problems; you’re actively identifying and resolving vulnerabilities. Why?
Because spotting these web application security issues early allows you to patch them and prevent real attacks down the road. Effective web application penetration testing is critical for remaining compliant with industry security standards, ensuring that your data remains safe and secure.
Importance for Online Businesses
Web application penetration testing is essential for any online business. It protects you against data breaches and potential financial catastrophes.
By making web security a priority, you can protect your data and earn your customers’ trust. They’re confident their information is in good hands.
Strong security practices put you ahead of the competition. They show your dedication to protecting your business and your clients.
73% of successful breaches in the business sector were accounted for by the penetration of vulnerable web applications.
Common Vulnerabilities in Web Apps
Common threats to web apps include SQL injection, cross-site scripting (XSS), and insecure authentication. These vulnerabilities are points of entry that allow attackers to tamper with your systems.
Hackers can use SQL injection to take control of your database. They can leverage XSS to take sensitive user data. Understanding these threats is essential to good pen-testing.
Knowing what you’re up against allows you to take specific steps to secure your web apps.
Typically, pen testing follows a structured approach: gathering information, spotting vulnerabilities, trying to exploit them, and then reporting the findings.
Tools such as Burp Suite, W3af, and SQLMap are central to this process. They help to reveal and resolve the potential problems quickly.
Getting yourself accustomed to the OWASP Top 10 list is critically important. It calls out the most serious security hazards, such as vulnerability to software failure and broken access control.
This preparation allows you to manage them well.
Impact of Web Vulnerabilities
Web vulnerabilities can severely impact your business and damage your reputation. When a web application is breached, the fallout can be ugly. This kind of vulnerability can create chaos for hackers during a web application penetration test.
Through these data breaches, they can steal sensitive information, such as customer data or financial records.
This impacts your business and also affects your customers, who may no longer trust your service. Once lost, trust is difficult to restore; customers will go to your competitors, and your market strength weakens.
Security incidents often lead to lost revenue and legal liabilities. A single breach can cost millions in fines and legal expenses, especially if sensitive customer data is at stake.
The law requires stringent data protection standards, and non-compliance can result in lawsuits or regulatory fines.
In addition to the immediate financial impact, you could also experience higher insurance premiums and the cost of improved security measures after the attack.
It’s essential to take proactive measures to make web vulnerabilities less risky. Regular penetration testing is vital for any organization creating web-based services or SaaS applications.
By identifying and fixing vulnerabilities before they can be exploited, you protect your systems and data.
Penetration testing follows four main steps: information gathering, vulnerability identification, exploitation, and reporting. These steps work together to assess and remediate potential risks.
Business Risks and Consequences
- Data Breaches: Unauthorized access to sensitive information.
- Loss of Customer Trust: Reduced confidence in your brand.
- Higher expenses: From incident response and legal fees.
- Operational Disruption: Interruptions caused by compromised systems.
- Legal Repercussions: Regulatory fines and penalties.
The long-term effects of security incidents on brand reputation can be devastating, especially when considering the impact of web application security issues.
Negative press and public perception can erode customer loyalty, often impacting revenue for the long term, making effective web application penetration testing essential to prevent these risks.
Importance of Timely Mitigation
It’s crucial to address known vulnerabilities quickly so that attackers can’t exploit them. Web application vulnerabilities jeopardize systems and can result in monetary loss.
By implementing a rapid response plan for vulnerability management, organizations can act quickly, reducing the damage done. Regular security assessments, including penetration testing, are necessary to retain a strong security posture.
This proactive approach keeps you a step ahead of emerging threats. It protects your applications from threats such as XSS, which can distribute malware and/or steal identities in the worst-case scenario.
Breaches that start with website and application attacks account for 47% of the breach costs, making application attacks the costliest.
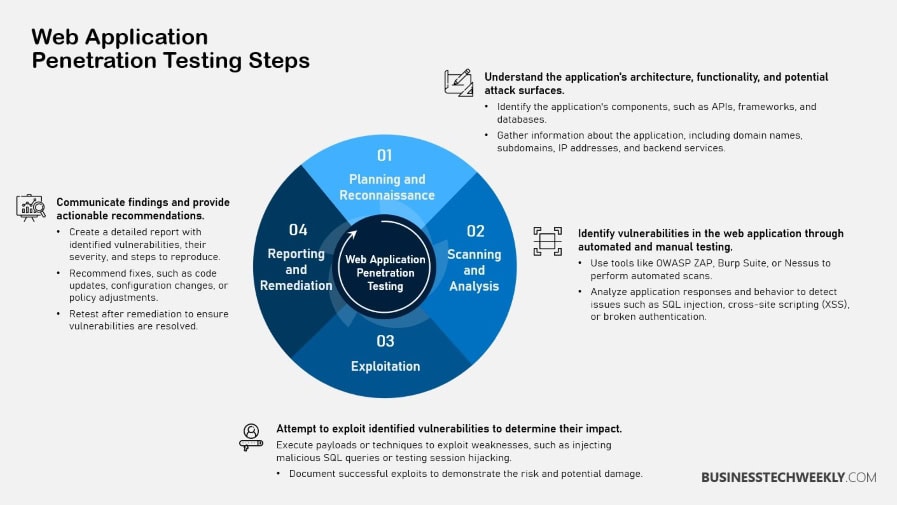
Process of Penetration Testing
Web application penetration testing is a methodology that significantly enhances the security of modern web applications and SaaS services.
This web app penetration testing process includes several key phases designed to systematically identify vulnerabilities and provide robust protection against potential cyber threats.
Let’s break down the critical stages of this process.
1. Planning and Preparation Phase
- Define the scope of the test to determine what parts of the application are in focus.
- Assess the risk to identify potential impacts on the application and business.
- Communicate with stakeholders to align objectives and expectations.
- Set clear timelines and resources for the testing engagement.
During this first stage, it’s important to establish a clear boundary. It helps you zoom in on a particular area, be it a section of the web app or the entire app.
The risk assessment guides you in determining what could go wrong and how to mitigate these risks.
Regular communication with stakeholders keeps everyone on the same page. Meanwhile, putting figures to timelines and resources keeps the project flowing.
2. Information Gathering Techniques
- Collect basic information like server names and IP addresses.
- Scanning: Use tools to discover open ports and services.
- Gather detailed information about network shares, users, and more.
This effective information gathering, like DNS enumeration, gives you attack vectors. Within this phase, hidden functions are discovered, and relevant data is retrieved through web scraping.
Keep ethical guidelines as a top priority. Respect privacy and legal boundaries when gathering information about target systems.
3. Vulnerability Scanning Methods
- Automated scanning: Quickly identifies known security flaws using tools.
- Manual testing: Digs deeper to uncover complex vulnerabilities.
Vulnerability scanning uses a combination of automated tools and manual efforts. Automated tools can quickly highlight your standard vulnerabilities but may overlook more complex issues that manual testing would uncover.
Your web app could use HTML5, JavaScript frameworks, or any number of other technologies. No matter the tech stack, these methods are key to finding potential weak spots.
4. Exploitation and Attack Strategies
- Use techniques such as SQL injection and XSS to test vulnerabilities.
- Understand attack strategies to simulate real-world threats effectively.
- Exercise caution to prevent damage during exploitation attempts.
This is where you take popular exploitation techniques for a spin and attempt to turn weaknesses into threats. It’s about replicating real-world attacks while not actually damaging the real system.
Understanding the strategies behind these attacks is key to effectively simulating them.
5. Reporting and Remediation Steps
- Include findings, evidence, and recommendations in the report.
- Communicate vulnerabilities clearly to stakeholders.
- Collaborate with development teams to fix issues promptly.
After testing, it is time for serious documentation. Your report should document the findings, supply supporting evidence, and make clear recommendations.
Communication is key here to ensure stakeholders understand the vulnerabilities discovered. Collaborating with development teams ensures that the issues are patched quickly, fortifying your app’s defenses.
OWASP Methodologies in Testing
When you are getting into web application penetration testing, the OWASP Web Security Testing Guide is a must-use resource. It’s almost the bible of what you would want to know if you’re trying to understand the weaknesses of the web.
This guide is a logical framework that provides you with a defined path for effective web application penetration testing.
Using an established methodology, like OWASP’s, is essential. It allows you to really get your hands dirty on the security of web apps – rather than scratching the surface.
A game plan will get you to cover all the bases, helping avoid missing important vulnerabilities that could result in serious security breaches.
OWASP plays a crucial role in promoting best practices in web security. They offer a collaborative platform where experts from all over share their insights, making the whole project robust and up-to-date.
For example, they highlight how Broken Access Control is a major issue, responsible for 42% of security bugs in modern web applications.
The guide’s recent update in 2021 reflects the latest threats, ensuring testers are always one step ahead. It provides a detailed web application penetration testing methodology, including black-box testing, which is essential for understanding how a malicious attacker might exploit vulnerabilities.
The guide also ensures consistency, whether you’re running internal tests or outsourcing to vendors. This guideline helps align expectations and output, ensuring that everyone is speaking the same security language during your web app penetration testing engagement.
Cost of penetration testing can vary widely. It often falls between $2,000 and $20,000, depending on how extensive and deep the testing is.
The OWASP framework even goes so far as to include a section on the penetration testing methods it covers, complete with a step-by-step guide for finding open doors.
This means your approach is thorough and careful — not a single stone is left unturned in the entire penetration testing process.
Benefits of Regular Penetration Testing
Consider regular penetration testing, and you may wonder, “Why is it essential?”
The first benefit is it dramatically enhances your security posture. By finding and patching flaws before attackers do, you diminish the chance of a data breach.
For example, penetration testing comes in different steps, which gives you a map of your security environment.
This isn’t just plugging holes; it’s building an impenetrable wall. To understand that, think about how automated scanners typically overlook risks such as business logic flaws or zero-day exploits.
Pen testing fills those gaps, so you don’t miss mega-important issues like SSRF and XSS bypasses.
Regular testing keeps you one step ahead of the evolving threats from cybercriminals. Cybercriminals are always innovating new methods for breaching systems. Continuous tests also provide you with actionable mitigation strategies so you can quickly adjust to new threats.
The cost of data breaches is soaring. It’s easy to see how expensive ignorance can be. Investing in regular penetration testing now saves you from the steep costs of breaches later.
This is very cost-effective over time.
Another significant benefit is compliance, and that’s huge. Numerous regulations (SOX, HIPAA, FISMA, etc.) require frequent security assessments.
By conducting penetration tests, you ensure that your organization meets these standards, avoiding penalties and legal issues.
Additionally, these tests provide insights on your app’s architecture, directing developers to focus on targeted areas.
Best Practices for Conducting Tests
When performing penetration testing of web applications, ethical behavior is essential. This means only testing with proper authorization and always respecting user privacy and data.
Document everything from scope definition to reporting findings. This builds a reliable record and can assist in repeating tests or validating results.
Regular testing is key since security threats evolve. By testing often, you’ll catch the new vulnerabilities that crop up as technology advances. Getting different viewpoints involved while testing is a great way to ensure this.
Input from developers and security experts can help identify potential security issues and increase the efficiency of your tests.
Ensure Comprehensive Coverage
If you do any penetration tests, don’t forget the basics. Here’s a list of key areas to focus on:
- Authentication: Ensure only authorized users can access your application.
- Session Management: Protect against session hijacking and fixation.
- Data Protection: Safeguard against data breaches and ensure encryption.
A holistic approach is needed to track down every vulnerability. We cover the basics and then some (front-end and back-end).
For example, if front-end testing covers input validation, back-end testing could verify database security.
When you prioritize high-risk vulnerabilities, you won’t waste time or resources on less important issues.
Regularly Update Testing Methods
Keeping your testing methods relevant to the current threats and technologies is negotiable. This requires constant training and adaptation. New tools and techniques pop up all the time, so you need to be current and adaptable in your approach.
Periodically review and iterate on your testing methodologies to make them sharper and more effective.
Automated testing can save you up to 70% of your testing time. Pair it with your manual testing to make sure you catch everything.
It’s this dual approach that makes coverage and efficiency reach maximum.
Collaborate with Development Teams
A step in the right direction is collaboration between penetration testers and development teams. Open communication helps normalize security awareness in your organization so that security becomes a collective responsibility.
Incorporating security practices into the software development lifecycle is essential. Sometimes it’s a matter of addressing vulnerabilities throughout the entire development process, rather than waiting until the end.
Interacting with developers enriches your knowledge of the app. This lets you address security gaps earlier in the process, ultimately saving time and money.
Duration and Expectations of Testing
Duration Factors and Considerations
With web application penetration testing, it can be all over the place. Several factors come into play, including the size and complexity of the application being tested.
A small app might take about a week, but larger applications could stretch to 2-3 weeks. If you’re dealing with hefty apps, it can take months to finish the project. This is especially true if you require a big team to handle everything.
If it’s a fairly simple hack, like testing 15 hosts from the outside, the entire thing could be done in a week. When you have a complex attack surface, think 4-5 weeks or more.
A seasoned team can speed up the process, knowing when to use automated tools and when to rely on manual methods, which typically cover about 75% of the testing.
However, limited testing hours can push timelines back. Scans and manual tests must be scheduled precisely, which adds to the wait.
Planning is everything. A good plan can save time and make sure the test hits everything you need it to hit.
Setting Realistic Expectations
It’s important to have frank discussions with stakeholders about what penetration testing can and cannot deliver. You cannot find every vulnerability all at once.
Testing should never be an isolated effort, but rather part of an overall security program. Regular tests, not one-off checks, matter most.
Stakeholders must know that the length of a pen test can differ considerably, from 1 to 15 weeks depending on the system’s complexity and available resources.
This knowledge establishes realistic expectations and highlights the need for flexibility in addressing unpredictable challenges.
The global penetration testing market size is expected to grow from $1.6 billion in 2021 to $3.0 billion by 2026, at a CAGR of 13.8% from 2021 to 2026.
Skills and Tools for Penetration Testing
Essential Skills for Testers
If you want to start diving into web application penetration testing, you’ve got to have a good baseline skill set.
For starters, you need to know your programming stuff. Languages like Python, Ruby, or JavaScript are often in a tester’s toolkit.
Networking skills are very important as well. They teach you how the data flows and where the cracks are that someone might exploit. Another key piece is understanding security protocols; protocols like SSL/TLS and HTTPS are the bread and butter of web security.
You’ll also need sharp analytical thinking. It’s like a puzzle—not only identifying weaknesses but understanding how they operate.
Problem-solving skills are gold here, as you have to think like an attacker to uncover and then patch security leaks.
Don’t overlook the communication skills either. You’ll be working with teams and writing clear reports. It’s essential to explain complex issues in ways that make sense to everyone involved.
Key Tools for Effective Testing
Making the right choice for the tools you use can be the difference between success and failure with your tests. Think tools such as Burp Suite, OWASP ZAP, and Metasploit.
Here’s a quick look at some key tools:
Tool |
Features |
Use Cases |
| Burp Suite | Comprehensive testing features; automation in commercial version | All-around security testing |
| OWASP ZAP | Easy to use; great for beginners | Finding basic vulnerabilities |
| Metasploit | Extensive exploitation framework | Exploit development |
Burp Suite remains a tester’s favorite above the rest. Its extensive feature set spans the entire testing process, from scan to exploit.
The commercial version ramps up automation, making it practically mandatory in many firms.
Tools such as SQLMap also excel, particularly for SQL injection vulnerabilities. Remember, automated tools are just part of the story.
Manual testing digs deeper, uncovering business logic vulnerabilities that automated scans may not catch.
Certifications for Professionals
Certifications will definitely give you an edge in this area. Aim for certifications like the Certified Ethical Hacker (CEH) or the Offensive Security Certified Professional (OSCP).
You may also want the Global Information Assurance Certification Penetration Tester (GPEN).
These certifications confirm your abilities and can help you in your career. Plus, the field of penetration testing is always changing. That’s why it’s important to keep abreast of new threats.
Ransomware, phishing, cross-site scripting (XSS), and SQL injection attacks are increasing. Continuous education keeps you ahead of the game and in line with industry standards.
Job Outlook and Career in Penetration Testing
As the cybersecurity landscape becomes increasingly complex, the demand for skilled penetration testers continues to grow. The job outlook for penetration testers is strong, with a projected 35% growth for information security analysts (which includes penetration testers) by 2031.
Organizations in finance, health care, and technology are leading this demand, as they have an increasing need to protect their digital property.
In metropolitan areas, where tech firms are prominent, penetration testers often enjoy pay that is higher than average.
According to August 2021 estimates, the average annual salary for penetration testers is just over $87,440. This figure reflects the high demand and critical need for these professionals to keep up in the world of cybersecurity.
Career Opportunities and Growth
Starting a career in penetration testing leads to a variety of different opportunities. You can explore roles such as Security Analyst, Ethical Hacker, Vulnerability Assessor, and Cybersecurity Consultant.
Each of these positions offers unique challenges and learning experiences.
Networking and professional development are critical for proper advancement in this ever-evolving field. Getting involved with industry conferences, joining professional organizations, and pursuing ongoing education are all essential to remaining current.
For example, specializing in cloud security or mobile application testing can immensely enhance your expertise and marketability.
Salary Expectations and Trends
Salary expectations in penetration testing vary based on experience and location.
For instance, as you gain experience, your earning potential increases significantly—from an entry-level salary of $67,950 to $81,230 for early career professionals.
Certifications and specialized skills can also boost your compensation. With a high demand for cybersecurity professionals, there’s considerable potential for salary growth.
The projected 45% increase in employment for information security analysts in Virginia by 2028 is a testament to this trend.
Key Points to Note
Entering the field of web application penetration testing positions you as a digital investigator, uncovering vulnerabilities and fortifying them against potential threats. It’s a meticulous process of identifying weaknesses and implementing solutions to secure the system.
To excel, equip yourself with the necessary skills and tools while rigorously adhering to OWASP guidelines, ensuring best practices are consistently applied.
- Web application penetration testing is essential for uncovering potential weaknesses within your web apps. By doing these tests, you can add solid security measures to protect them.
- I believe that a solid foundation in cybersecurity skills is absolutely critical for effective penetration testing. Your skills will greatly improve by mastering these tools, such as Burp Suite, Metasploit, and Nmap.
- A structured testing process enhances the thoroughness of your security assessments. It contains critical phases like planning, discovery, and exploitation.
- Learn more about OWASP methodologies to learn the basics of web application security. With this knowledge, you can identify—and address—the most pressing risks.
- When you implement best practices, they can greatly improve the penetration testing process. For example, having clear documentation and communicating with stakeholders will yield better results.
- Frequent pentests are vital for helping web applications remain secure. This practice also protects sensitive data and preserves user trust.

