Cloud Computing Security: Ensuring data protection and privacy in the cloud
Organizations are collecting massive amounts of data. This data ranges from highly sensitive business and financial information to personal customer data. With more and more business moving their data to public, private and hybrid cloud services, ensuring cloud data privacy and protection is more critical than ever.
Being able to access work information from anywhere via the internet has its advantages, for example, allowing employees travelling for business purposes, or by working from. However, such advantages bring their own considerations regarding the security of the data that they access.
If businesses want staff to be able to work information from outside of the office, how do you ensure that confidential data remains secure, and is processed in compliance with regulations and legislation?
On this page:
Why cloud data protection and is necessary
Cloud data protection and other privacy issues are considered as significant risks when keeping personal information in the cloud. The hazards, or risks, posed by storing data in the cloud include:
- Unauthorized access
- Loss or damages caused by the service provider and their workers
- Activities targeting the service provider – hacking or sending malware and trojans
- Weak security practices relating to data protection
- Violation of regulatory controls
Before picking a cloud computing service, you should carry out a risk analysis to assess any potential impact on your organization. With a significant portion of applications and data hosted on third-party infrastructure, protecting and securing data across multiple environments can be complicated, leading to several types of risks. For example:
- Failing to keep track of where their applications and data are stored.
- They are no longer retaining visibility into who is accessing and using the applications and data, from which devices, and how data is being shared.
- Lack of insight into how the cloud service provider is storing and securing the data.
- They are neglecting to acknowledge that cloud security is a shared responsibility. Typically, most cloud providers have state-of-the-art security; however, this can be limited.
- Ignoring that cloud providers have varying capabilities, and failing to address inconsistency in cloud data protection, by developing their own security policy.
Organizations also have to address several other security challenges, such as:
- Security violations
- Data misuse and theft
- System vulnerabilities and malware infections
Consequently, while there are many benefits of cloud computing, there are also pitfalls which must be addressed to ensure that sensitive data is kept secure and protected.
Cloud computing and data protection regulations
Organizations wanting to store or process personal or confidential data in the cloud, whether that data relates to employees or customers, must ensure compliance with data protection and privacy regulations and laws. The GDPR (General Data Protection Regulation) in the EU, or HIPAA (Health Insurance Portability and Accountability Act of 1996) in the US, are two prime examples.
In many cases, these data protection and privacy laws identify the cloud service customer, that is the organization using the cloud service, as responsible for the protection of that data – if the purpose of the data and the way the data is used is determined by them.
Consequently, organizations using a cloud service will be responsible for ensuring compliance with any data protection and privacy legislation, even though they do not have complete control over the cloud. However, you still must retain sufficient control over the data to ensure you meet any legal obligations.

Doing your homework
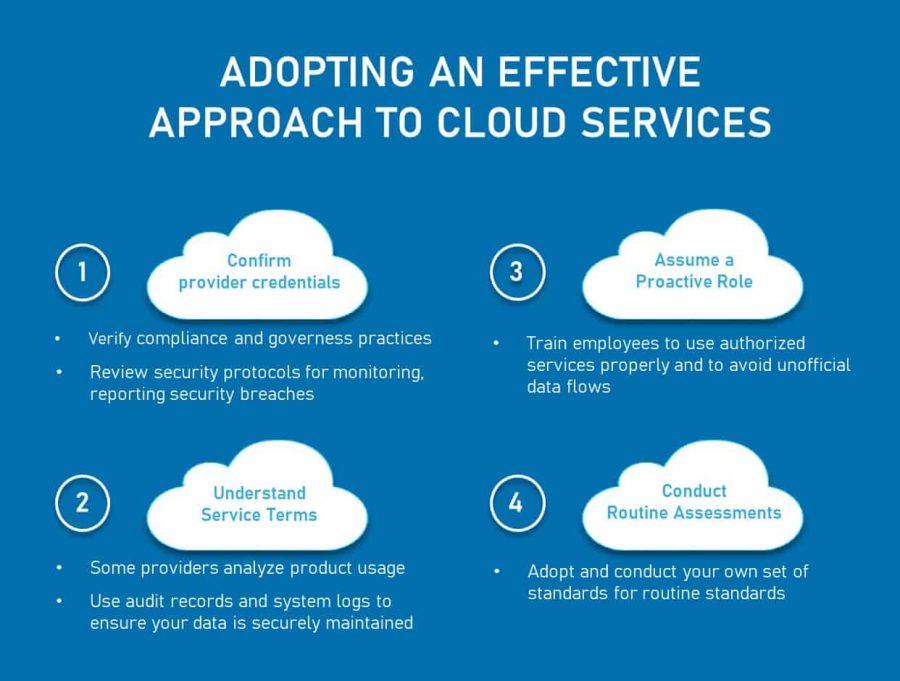
The cloud market has a plethora of service providers, each offering a wide range of services. This allows business and organizations to evaluate several cloud providers to find one that that best meets your security and data privacy and protection needs. However, it is imperative that SMBs ask the right questions before selecting a provider.
If your organization is migrating data to the cloud, you will be responsible for ensuring that any data processed securely – even if the cloud provider is carrying out that processing on your behalf.
Consequently, you will need to choose a cloud provider that can provide adequate written assurances concerning the security or location of their service. The Information Commissioner’s Office (ICO) is a good starting point. Their guidance on cloud computing outlines considerations to be taken into account during the cloud selection process. For example:
- How does the cloud provider store data, for instance, is it co-stored or intermingled with other data?
- Does the cloud provider hold any industry accreditations, such as ISO 27001?
- Can they provide copies of any independent security audits or other evidence of their security track record?
- How do they monitor, report and respond to security breaches?
- Do they permit or use encryption?
- What level of responsibility the cloud service provider will maintain for the security functionality and continuity of service
- Are there provisions for compensation if there is a data breach
- Outline the customer’s rights to access and delete the data, confirming they will act only on the customer’s instructions, for example, deleting any data when requested to do so
- Have the appropriate protocols which specify when the provider can access the data
- Elaborate on how security is monitored, and breaches are dealt with
Cloud service providers not offering assurances could indicate inadequate data protection practices. In such cases, the risk of violating data protection legislation is likely to be higher than necessary.
The benefits of ensuring cloud data protection and privacy
Addressing privacy and security concerns by ensuring cloud data protection enables organizations to:
- Improve governance with regards to data access
- Define appropriate policies, such as an information security policy
- Maintain complete visibility of all user, folder and file activity across multiple environments while simultaneously ensuring secure applications and data in diverse locations
- Identify and mitigate threats, such as security risks, suspicious user behaviour, malware and others.
- Minimize and prevent data loss and theft
How businesses can ensure data protection in cloud environments
Small and medium businesses and organizations are increasingly relying on cloud applications such as Salesforce, Concur, Workday, Dropbox, and more. Such SaaS applications store, process and share data in some form or another.
See also: SaaS vs PaaS vs IaaS
The increased reliance on cloud computing, and the potential risks associated with managing data in the cloud, has given rise to the need for additional safeguards to ensure cloud data protection and privacy.
Cloud applications are often business-critical, and crucial for employees, improving productivity and efficiency across the organization. Blocking them at this point would be silly. Instead, organizations should seek to bring your cloud data into compliance with any data protection regulations or legislation.
This could be accomplished via policy, which can make sure you can take action whether your employees are on-site or remote-based, or on a laptop or mobile device.
To successfully ensure satisfactory and compliant data protection and privacy in cloud environments, organizations should:
1. Conduct an audit of your data
Audit your data to determine if any data can not be shifted to the cloud. This could be because of contractual limitations, which restrict the transfer of sensitive information, or your privacy policy does not permit the transfer of certain types of personal data. Once identified, establish an exact list, categorizing the data you intend to shift to the cloud.
2. Know where your data is being processed and stored
Your data can be moved around between the data centers owned by the cloud provider; also, the vendor’s head offices are rarely the location of your data is being hosted. Organizations should identify exactly where the cloud provider will host their data.
The transfer of personal data outside the EEA (European Economic Area) is regulated by EU data protection law. It’s therefore crucial to ask where the provider will store that data and what safeguards are in place there at that location.Most cloud providers will be transparent when queried.
‘Europe-only’ solutions are offered by some cloud providers. Some cloud providers also offer clouds operating within the ‘Safe Harbor’ regime, as enforced by the Federal Trade Commission. Your particular circumstances will determine if these are necessary. Where in doubt, seek legal advice.
3. Implement appropriate security measures to protect data from unauthorized processing, loss, or alteration
Determine which applications meet your security standards. For those that don’t, either block them or compensate be implementing adequate controls. Read our 10 steps to avoid data misuse and theft.
4. Remove any applications which are not required
Once you have determined which applications are in use in your organization, consolidate or purge any applications which have overlapping functionality.
5. Limit the processing of “special” data and only collect “necessary” data
Ensure your data processing agreement confirms the application only collects personal data from your users that are necessary for performing the application’s function. Also verify that collection of “special” data, which are defined as those revealing things like ethnicity, race, religion, political conviction, and more are limited.
6. Only allow Cloud applications to use personal data for specific purposes
Ensure your data processing agreement, that applications clearly state in their terms that the customer owns the data, and that this data will not be shared with third parties.
7. Erase the data once you no longer need, or use, the application
The terms should clearly affirm that you can download your data immediately, and that once you’ve terminated the service, the application will erase your data. Businesses are advised to identify how long it takes for them to do this. The longer your continues to reside in cloud after terminating the service, the greater the risk of exposure.
8. Ensure, where possible, data is encrypted both at ‘rest’ and ‘in transit’
Any personal data, being transferred from your premises to the cloud provider, i.e. ‘in transit’, should be encrypted to minimize any risk to the data. Any encryption used must meet industry recognized standards. With regards to data at ‘rest”, that is, sensitive personal data is stored in the cloud, the ICO suggest the consideration of encryption.
9. Carefully review your privacy policy
As per the ICO, you should be transparent with individuals when processing personal data in the cloud. If required, you should amend your privacy policy to ensure it allows the processing of personal data in the cloud.
10. Pro-actively manage your contract with the cloud vendor
You should aim to retain full control of your data throughout its lifecycle. As part of these measures, you should be monitoring and reviewing your cloud provider’s security measures periodically to that expected standards are being met. Also checking audit reports and system logs will help achieve this aim.
11. Train your employees
Cloud data protection measures are only effective when people adhere to them. Ensure your staff clearly understand their responsibilities, and are kept updated of the latest protocols and pricedures, for example, following best practices to keep their authentication details secure, maintaining the security of encryption keys, and adhere to access controls.

Cloud data protection and privacy, remains a key concern for small and medium businesses, and is often the main impediment to moving to the cloud.
This guidance aims to introduce areas of consideration when your organization looks to using cloud services and servces as quick checklist for organizations who have already shifted data to the cloud, or provides a starting point for a organizations considering a cloud service.
Regardless of the stage you’re at, a careful consideration of the data risks and challenges in the early stages of planning for cloud data protection and privacy are central to a successful cloud project.

