What is Remote Access? Understanding the benefits and best practices

Digitalization has given rise to working remotely. More and more employees opt for regular work from home flexibility even when living and working in the same city. Remote access solutions help employees become more efficient and productive.
The workplace is no longer confined to physical offices, and resources can be accessed from any location on any device. While cloud storage has made lives more accessible, there are instances where you need to gain access to your computer remotely.
Provided below is an overview of precisely what is remote access, its uses, benefits, and considerations.
On this page:
What is Remote Access?
Remote access refers to the ability to gain access to the data and applications stored on a computer from some other location and device at any time.
With remote access software, you get the facility to open, edit and save files located on the computer from anywhere in the world. Such freedom proves helpful to travelers, offsite workers, and employees working away from the office.
Remote access can be set up in multiple ways. Its function and purpose vary greatly, depending on the use and platform. Access can be given as long as the two devices are connected in some way.

How does Remote Access Work?
To set up remote access, a business needs to deploy software on the server or local workstation. Each of these solutions is different but generally, work similarly.
You will need to install the necessary applications on both the client and server computers and any mobile devices you want to have remote access.
Here are the most popular ways to establish a remote connection:
- Virtual Private Network (VPN) – VPNs enables distant employees to route their internet activities through a secure server that connects them directly to their company’s network. Virtual Private Networks encrypt data transmitted over the network, rendering it unintelligible to anybody who has access to it.
- Virtual Network Computing (VNC) – VNC is a graphical screen sharing that enables users to view and control another computer’s desktop. This is achieved using a network connection and the Remote Frame Buffer (RFB) On the client, a viewer is installed and linked to the server (the remote workstation). VNC is often used in conjunction with a VPN.
- Remote Desktop Protocol – RDP is a proprietary Microsoft protocol for remote access. However, other variants exist for macOS, Linux, and other operating systems. Software firms may even have their proprietary protocols in some situations. With RDP, the server can listen on TCP and UDP port 3389 and accepts connections upon request.
- Internet Proxy Servers – Internet proxy servers enable communication between computers that are not connected to a corporate network or firewall. While this option is advantageous for establishing external connections, remote access connections are often established over a secure VPN.
A remote access software can be installed directly on a local computer, used over the internet, or deployed over a LAN, WAN, or VPN.
It is important to note that each solution has its unique way of working and its set of features and characteristics.
Why is Remote Access Important?
As suggested by surveys and reports, up to 50% of the global workforce will be working remotely in the next few years. Employees will have the flexibility of working from any location, avoiding long commutes to reach the physical offices.
This not only saves time but opens up opportunities for people with physical disabilities, new parents, and those who need to care for their family members. People who are not able to relocate for work can also enjoy job opportunities with remote access.
The increasing shift towards remote working is beneficial to employers as well. Organizations don’t need to spend on rents and resources to maintain offices. They can save money and focus on other aspects of the business.
Employees can also save money spent on the commute and live in more affordable areas. Companies should have a plan for remote access to avoid any downtime in case of a natural disaster and other circumstances that limit physical access to resources.
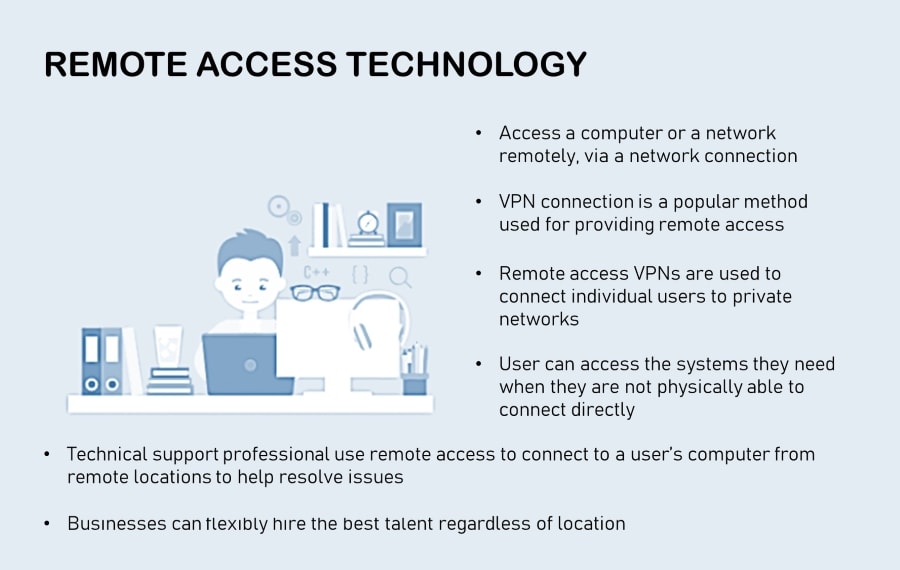
How do Businesses Benefit from Remote Access?
There are several benefits remote access can bring for businesses, from increasing productivity to lowering costs and much more. Here are a few of them.
Improved Flexibility and Productivity
Employees need better tools to be productive when working from home. They require safe and secure access to resources from outside the corporate network. Remote access gives them the tools that help them stay productive and focused from remote locations.
IT teams can manage the information and applications centrally to lower the complexity and maximize efficiency.
Better Security
Today, employees demand easy access to all the cloud, web, and SaaS applications across locations and devices. IT teams should introduce a single sign-in option for users across applications to ensure a seamless experience while taking care of security.
They can use techniques like multi-factor authentication and access controls to maintain end-to-end security for the traffic while letting the users connect from anywhere.
Easy Technical Support
This is one of the most common use cases of remote access among technicians. IT admins can leverage powerful remote access software to control the employee devices remotely, regardless of their physical location.
Whenever there is an issue, either with a file download or an application, teams can quickly provide remote technical support and troubleshoot the problem.
Collaboration Among Dispersed Teams
A company can have its headquarters in one location and offices in multiple locations around the globe.
This poses several difficulties when trying to keep teams on the same page. Remote access helps here by facilitating meetings and training sessions across locations, encouraging collaboration among employees separated by distances.
Improved Business Continuity
Business continuity refers to a company’s ability to maintain functionality before and after a disruption. From outages to natural disasters, so much can affect the productivity of organizations and cost time and money.
Remote access lets employees remain productive even when they are displaced because of an incident.
Low Costs
Digitalization has given rise to a mobile workforce that pushes productivity beyond the constraints of work hours and physical locations. Businesses can introduce Bring Your Own Device (BYOD) programs to allow employees to work from any location on any device.
Workers can use remote access to stay productive, while employers can lower the costs of buying and managing devices.
Better Talent Acquisition
By allowing remote onboarding and access, businesses get an opportunity to hire from a bigger pool of talent from any corner of the world.
As remote access lets employees work from any location, managers are no longer restricted by geographical limits.
Best Practices for Remote Access Security
Remote access has evolved to become effective and convenient but is not free of risks. With cyber threats getting more complex and widespread, IT teams need to be more focused on keeping attackers away and protecting the exposed remote connections. There are several ways businesses can ensure security, whether used for remote technical support or job responsibilities.
Here are a few remote access best practices that businesses may adopt to increase security while maximizing the benefits of technology.
- Prioritize Endpoint Security – Endpoint security is concerned with protecting devices, workstations, and servers that connect to networks. Firewalls, antivirus software, and patch updates are just a few of the most common forms of endpoint protection.
- Create strong passwords – Create unique and complicated passwords that contain at least 12 characters and are composed of a random combination of capital and lowercase letters, numbers, and symbols. Proactive measures such as constantly resetting default passwords, updating them frequently, and never sharing or using the same password can assist in preventing hackers from figuring them out.
- Utilize multi-factor or two-factor authentication (2FA) – Using 2FA to control access provides another degree of security. Two-factor authentication will require creating a username and password and a unique code through SMS text messages. The use of biometrics such as face or fingerprint recognition, multi-factor authentication takes this a step further.
- Establish an account lockout policy – To protect against hackers using brute-force assaults and automated password guessing programmes, it’s critical to configure your computer to lock your accounts after a certain number of failed password entries.
- Maintain firewalls – By restricting who has remote access, firewalls may act as your first line of defence in terms of network security. You should implement firewalls to limit access using software, hardware, or a combination of the two.
- Regularly update your software – Ensure that your software is updated automatically to ensure that you are working with the most up-to-date security patches. This ensures that the most recent security fixes are installed. This can assist in safeguarding you from new malware and other harmful infections.
- Limit the number of remote access users – Restricting the number of remote access users can assist preserve security. Allowing administrators to operate in a restricted mode is one method to do this.
Remote computer access has several benefits for organizations, people, and families. However, it is critical to protect remote access.
Final Thoughts
Remote work is rapidly becoming the norm across industries as employees opt to work from home, relocate to better places and address their responsibilities on the go.
This flexibility helps organizations attain improved productivity and employee engagement. Along with the perks, there are many challenges associated with dispersed teams.
Remote access seems to be highly useful by providing an easy way to bring together users across locations and deliver support.
With the right remote access software, a business can securely communicate with vendors and teams. At the same time, employees can leverage the flexibility to access resources from any device, regardless of the location.

